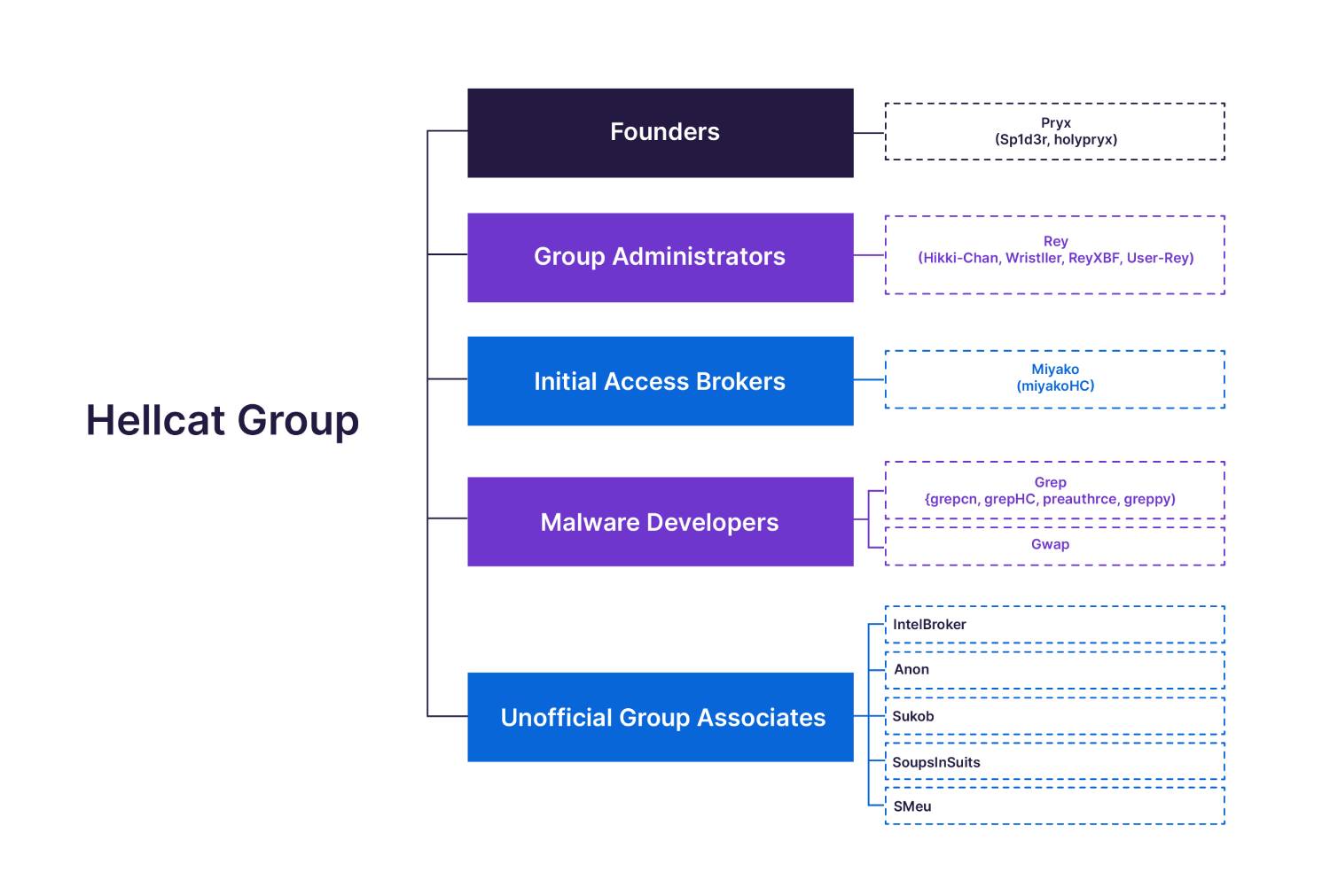
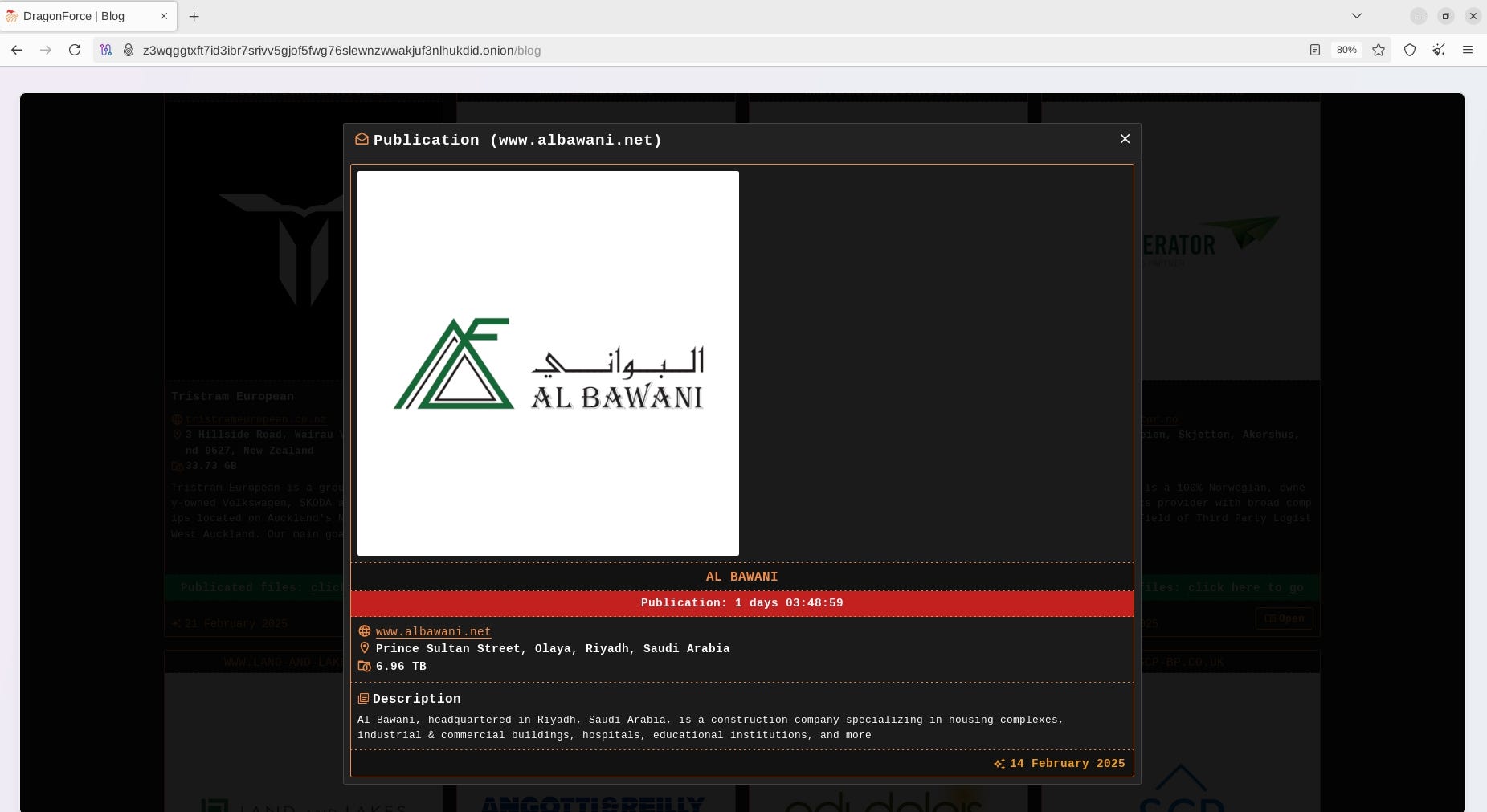
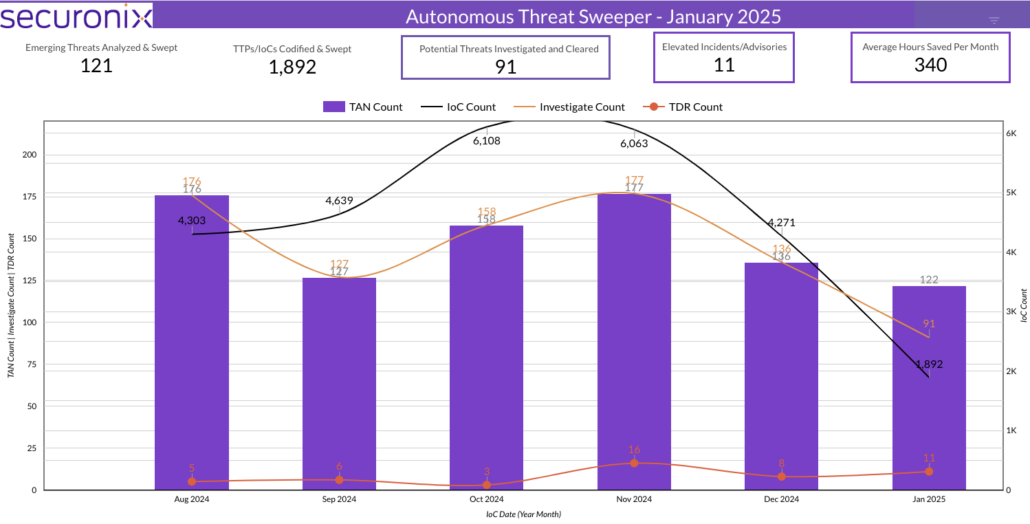
Summary: Ransomware groups are evolving their tactics by focusing on targeting weak credentials rather than exploiting vulnerabilities, as highlighted in Travelers’ latest Cyber Threat Report. There was a noted surge in ransomware activity, particularly in Q4 2024, with a record number of victims. The report emphasizes the effectiveness of basic attack techniques, urging businesses to implement stronger security measures like multifactor authentication (MFA).…
Read More 
 THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact
THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact