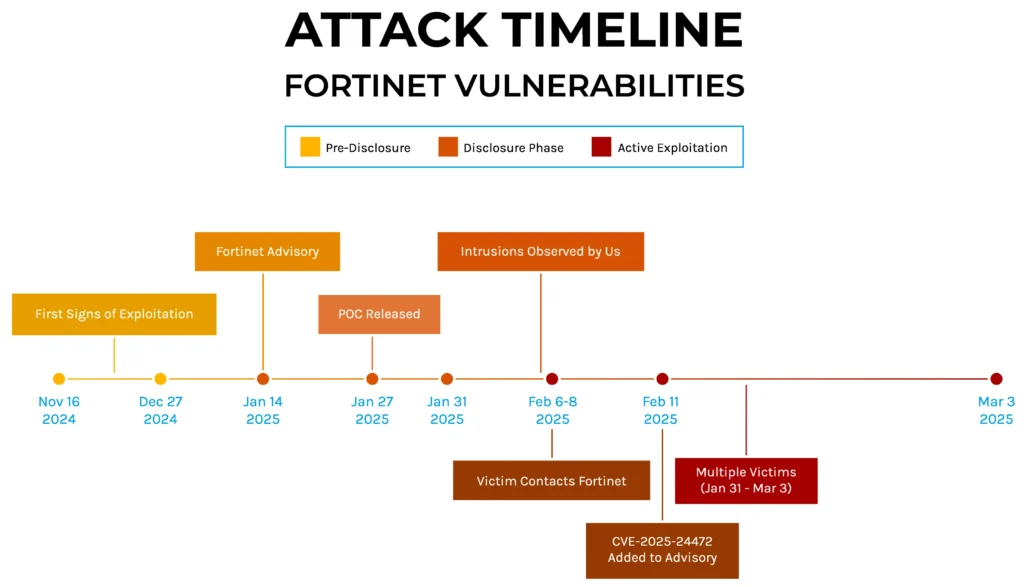
Forescout Research has identified a new ransomware strain, dubbed SuperBlack, linked to the threat actor “Mora_001”, exploiting vulnerabilities in Fortinet devices. This threat actor is connected to the LockBit ransomware ecosystem and demonstrates sophisticated tactics including rapid ransomware deployment, user account creation across victim networks, and the use of modified LockBit tools.…
Read More 













 THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact
THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact