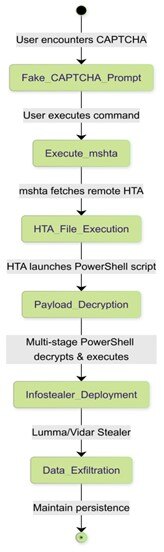
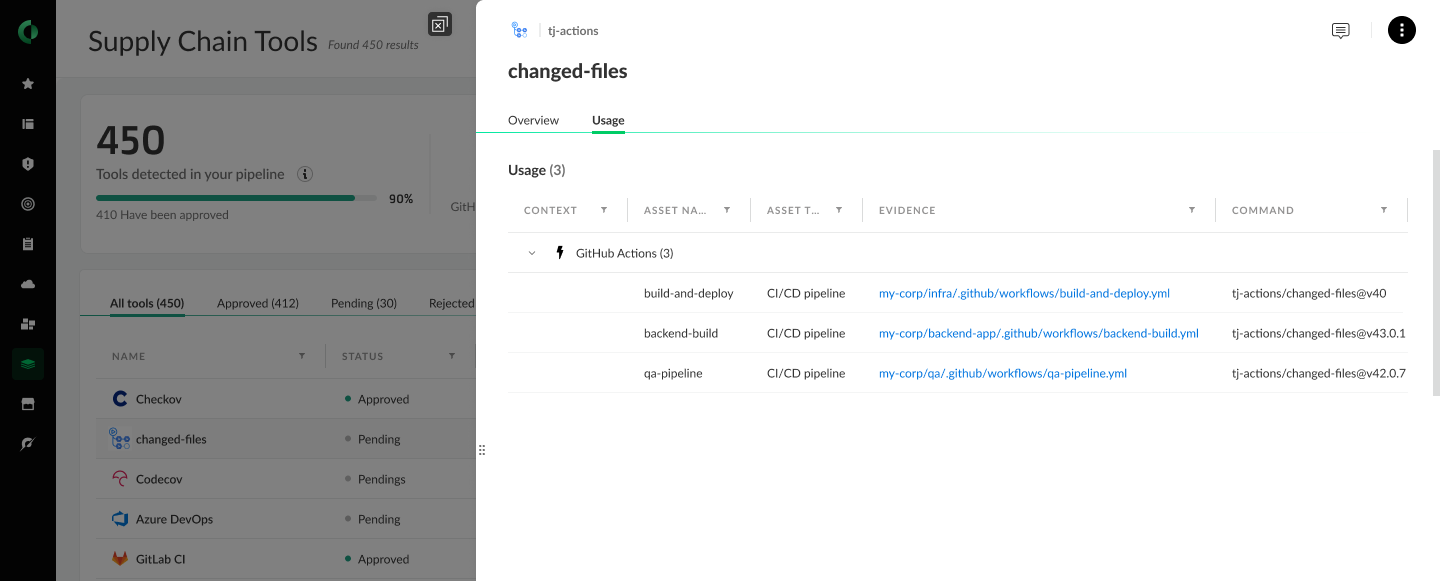
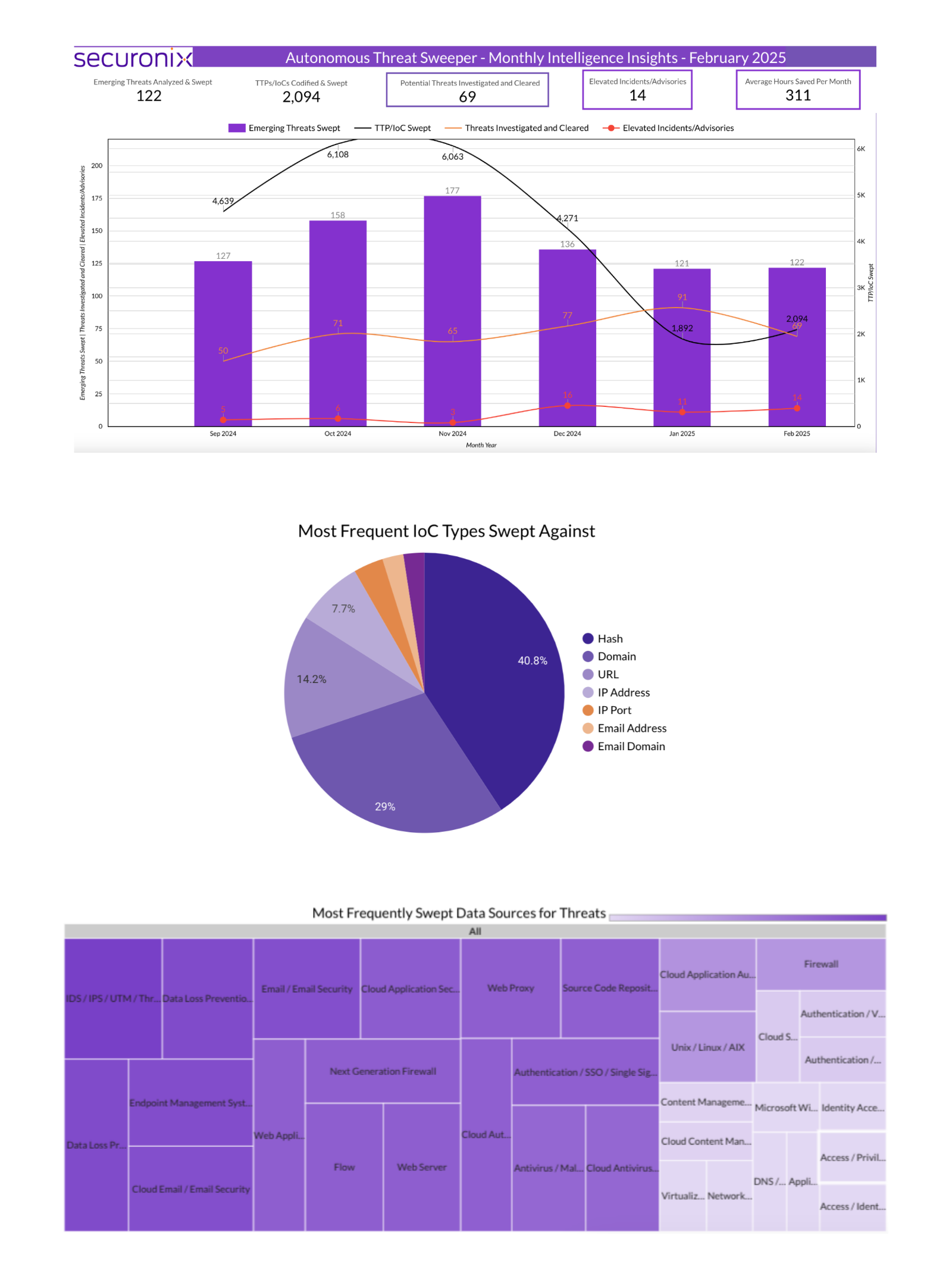
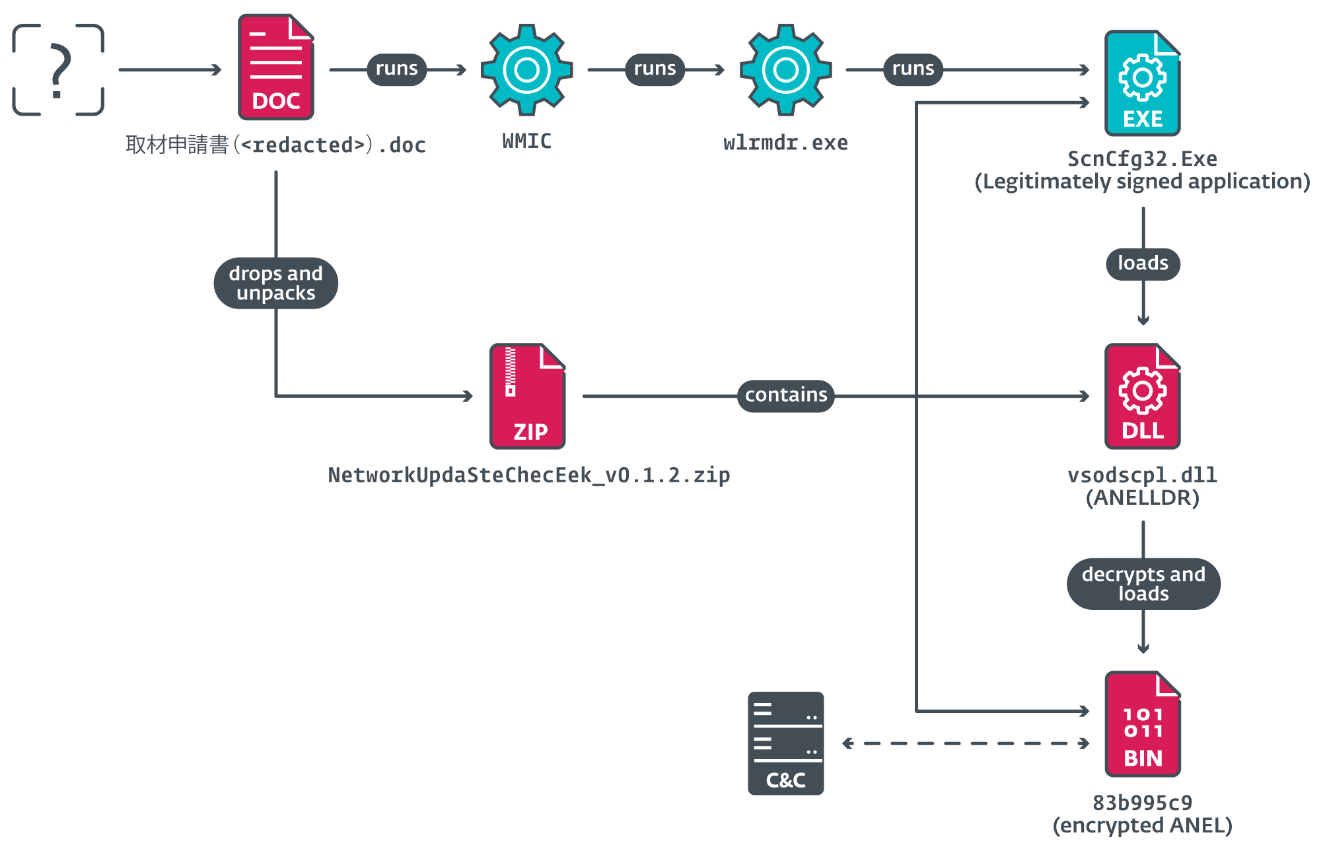
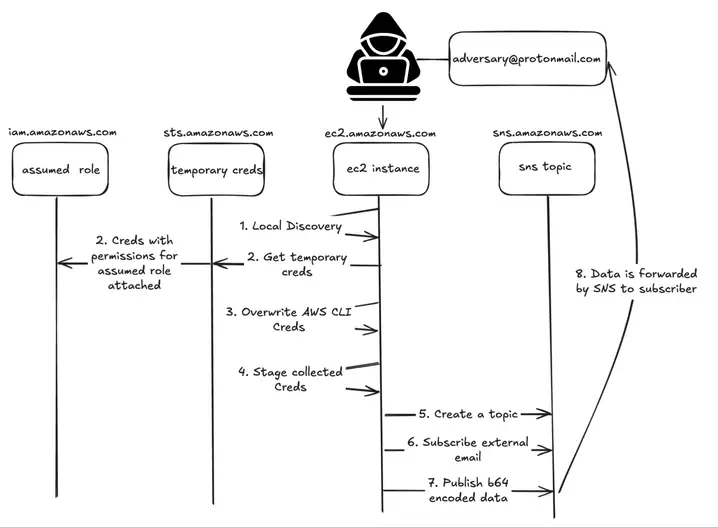
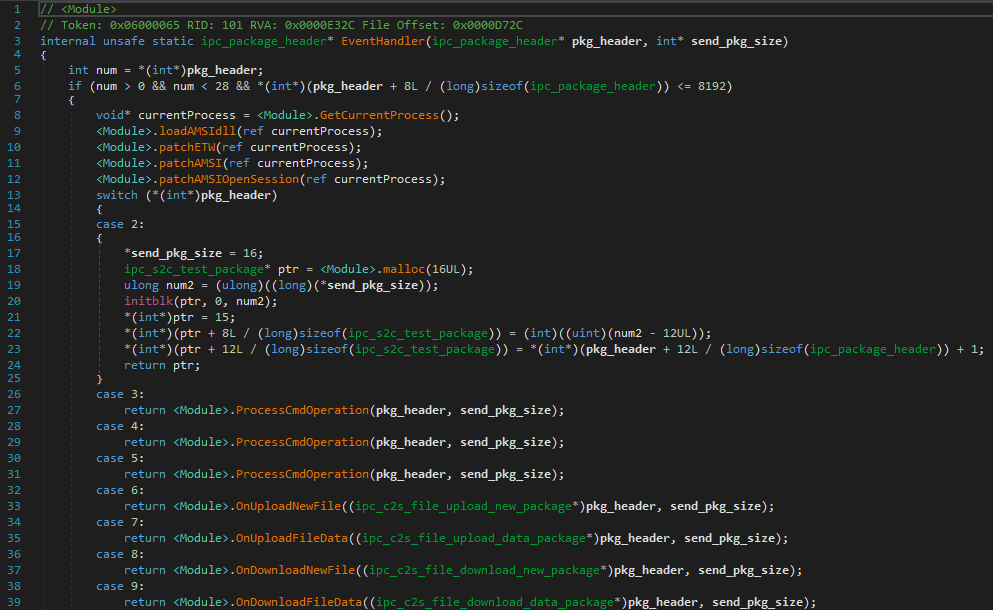
This article discusses a range of exploits and malware variants associated with RansomHub, Betruger, and various other threats. Notably, it highlights multiple hashes identified as indicators of compromise related to these malware family. The findings suggest significant concerns regarding the cybersecurity landscape with active threats to different platforms.…
Read More