The blog outlines several critical unauthenticated Remote Code Execution vulnerabilities found in Ingress NGINX Controller for Kubernetes, collectively dubbed #IngressNightmare. These vulnerabilities can grant attackers unauthorized access to all secrets within a Kubernetes cluster, risking complete takeover. With a CVSS v3.1 score of 9.8, it is estimated that 43% of cloud environments, including many Fortune 500 companies, are at risk.…
Read More Tag: PROXY
Summary: A hacker claimed to have exfiltrated 6 million records from Oracle Cloud, including sensitive data such as customer security keys and email addresses, by exploiting a vulnerability in one of its Single Sign-On servers. Despite the hacker’s assertion and evidence of the breach, Oracle has denied any security compromise.…
Read More 
Summary: Sygnia reported on a sophisticated cyberattack by a China-nexus threat actor named Weaver Ant targeting a major telecommunications company in Asia. The group utilized complex methods, including web shell tunneling and advanced evasion techniques, to maintain persistent access for espionage purposes. Their persistent approach integrated multiple web shell types and various stealth techniques, demonstrating high adaptability and evasion from detection mechanisms.…
Read More 
Summary: A critical vulnerability (CVE-2025-29922) in the kcp project allows unauthorized creation and deletion of objects across arbitrary workspaces through the APIExport Virtual Workspace, despite the intended access controls. With a CVSS score of 9.6, this issue poses significant security risks for users in multi-tenant environment configurations.…
Read More Summary: The video discusses how understanding Java’s URL handling and specifically the Spring Boot actuator can expose security vulnerabilities in web applications, leading to significant financial rewards through bug bounty programs. The presenter shares techniques on how to bypass security measures to access protected critical functionalities and heap dumps containing sensitive data.…
Read More 
Summary: A China-linked advanced threat group named Weaver Ant infiltrated a telecommunications provider for over four years, utilizing compromised Zyxel routers and advanced tactics for data exfiltration and remote access. They employed a custom web shell called INMemory and sophisticated methods like web shell tunneling to maintain control and evade detection.…
Read More 
Summary: A set of five critical vulnerabilities, collectively named IngressNightmare, has been identified in the Ingress NGINX Controller for Kubernetes, exposing over 6,500 clusters to potential unauthenticated remote code execution. These vulnerabilities could lead to unauthorized access to all secrets across various namespaces, potentially resulting in complete cluster takeover.…
Read More 
Summary: Recent cyber threats highlight vulnerabilities in open-source tools, escalating ad fraud through mobile apps, and advanced ransomware tactics targeting critical defenses. Notably, attacks have leveraged AI, and a supply chain breach at Coinbase exemplifies these risks. A rise in stolen credentials further underscores the urgent need for improved cybersecurity measures.…
Read More 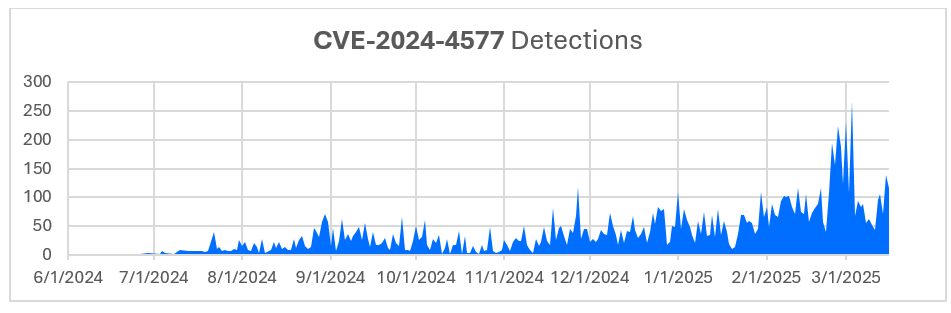
In June 2024, Bitdefender Labs highlighted a critical security vulnerability (CVE-2024-4577) in PHP affecting Windows systems in CGI mode, allowing remote code execution through manipulated character encoding. This vulnerability has seen an increase in exploitation attempts, especially in Taiwan and Hong Kong, with attackers also modifying firewall settings to block known malicious IPs.…
Read More
Hunt researchers exposed a web server hosting tools linked to an intrusion campaign against South Korean organizations. This server, available for less than 24 hours, encompassed a Rust-compiled Windows executable that deployed Cobalt Strike Cat along with several other open-source tools. The attacker appears to have focused on exploiting vulnerabilities in government and commercial entities.…
Read More 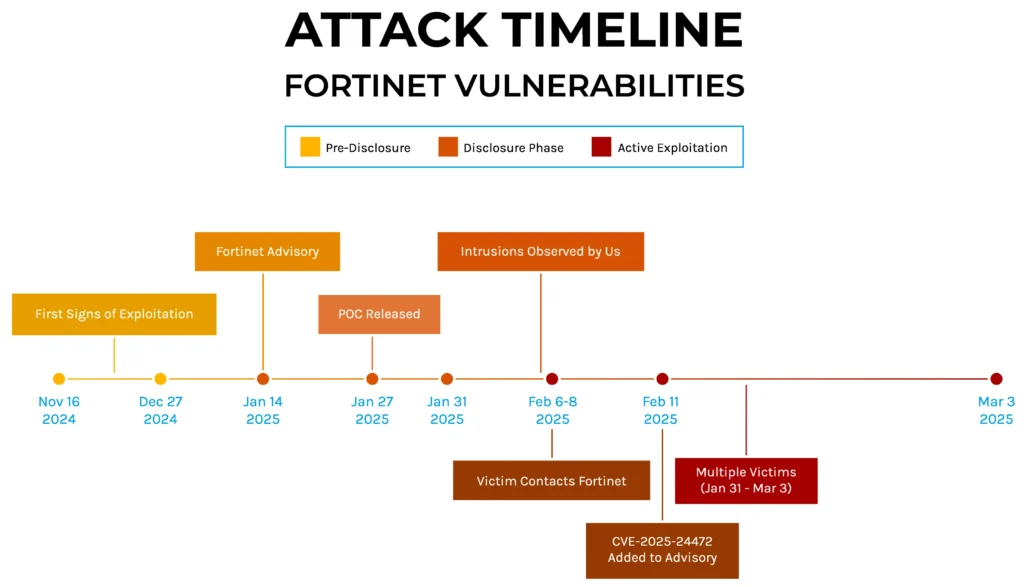
Forescout Research has identified a new ransomware strain, dubbed SuperBlack, linked to the threat actor “Mora_001”, exploiting vulnerabilities in Fortinet devices. This threat actor is connected to the LockBit ransomware ecosystem and demonstrates sophisticated tactics including rapid ransomware deployment, user account creation across victim networks, and the use of modified LockBit tools.…
Read More 
Summary: Hunt researchers have detected a sophisticated cyber intrusion campaign focusing on South Korean organizations, utilizing modified Cobalt Strike tools and various open-source exploitation tools. The attackers leveraged a publicly exposed web server to distribute their malware and gather intelligence on over 1,000 Korean domains, targeting government and commercial entities.…
Read More 
The US Department of Justice has indicted employees of the Chinese contractor I‑SOON for conducting espionage campaigns, particularly targeting governments, NGOs, and think tanks through the FishMonger APT group. The campaign, termed Operation FishMedley, involved complex techniques and tools typically used by China-aligned threat actors, leading to the compromise of several organizations across various continents.…
Read More 
Summary: A new advanced persistent threat (APT) group named UAT-5918 has been identified, targeting critical infrastructure and various sectors in Taiwan since 2023. Their tactics include gaining long-term access for information theft using web shells and open-source tools, leveraging known security flaws in outdated systems. Researchers associate their methods with other Chinese hacking groups and highlight a sophisticated approach to credential harvesting and data theft.…
Read More 
This article discusses a range of exploits and malware variants associated with RansomHub, Betruger, and various other threats. Notably, it highlights multiple hashes identified as indicators of compromise related to these malware family. The findings suggest significant concerns regarding the cybersecurity landscape with active threats to different platforms.…
Read More 
Summary: Russian internet users experienced significant outages this week due to disruptions linked to Russia’s blocking of Cloudflare, affecting various online platforms and banking services. The internet regulator Roskomnadzor attributes these issues to reliance on foreign server infrastructure while suggesting a switch to local hosting providers.…
Read More 
The CYFIRMA Research and Advisory Team has discovered the VanHelsing Ransomware, which targets Windows systems and uses advanced encryption methods, making it challenging to detect and remove. It employs double extortion tactics, threatening to leak sensitive data, and stresses the importance of proactive cybersecurity measures and incident response strategies.…
Read More
SideWinder, also known as Rattlesnake or T-APT-04, is an advanced persistent threat group from India that has expanded its operations to target maritime and nuclear sectors across Asia, the Middle East, and Africa since 2012. Known for quickly adapting to security measures, SideWinder employs various tactics, techniques, and procedures (TTPs) to execute sophisticated cyber-attacks, primarily through phishing and malware.…
Read More 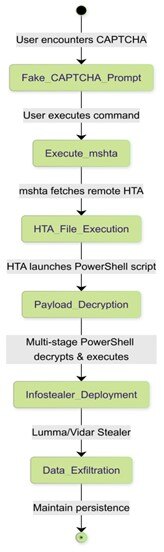
The article discusses a recent investigation by Trustwave SpiderLabs that uncovered a campaign leveraging fake CAPTCHA verifications to execute malicious PowerShell scripts, leading to the deployment of infostealers like Lumma and Vidar. The multi-stage attack involves deceptive prompts to execute commands, downloading HTA files, decrypting payloads, and executing infostealers.…
Read More 
Summary: Ukraine’s Computer Emergency Response Team (CERT-UA) has issued a warning about targeted attacks utilizing compromised Signal accounts to deliver malware to defense industry employees and military personnel. The attacks involve messages with archives masquerading as meeting reports, leading victims to inadvertently execute harmful files. This activity, tracked as UAC-0200, has seen recent updates in phishing tactics to align with urgent military topics in Ukraine.…
Read More  THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More