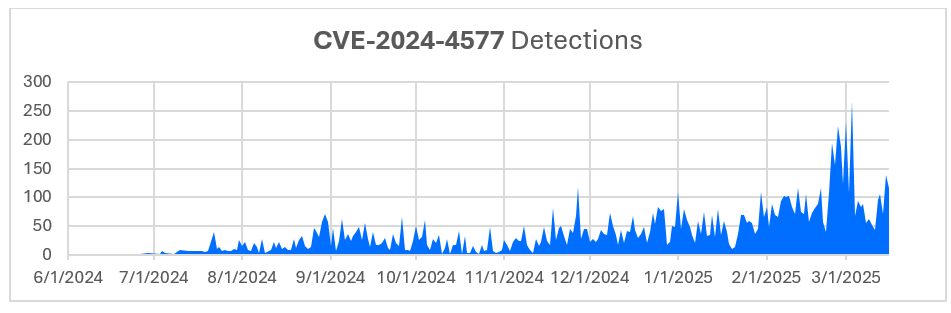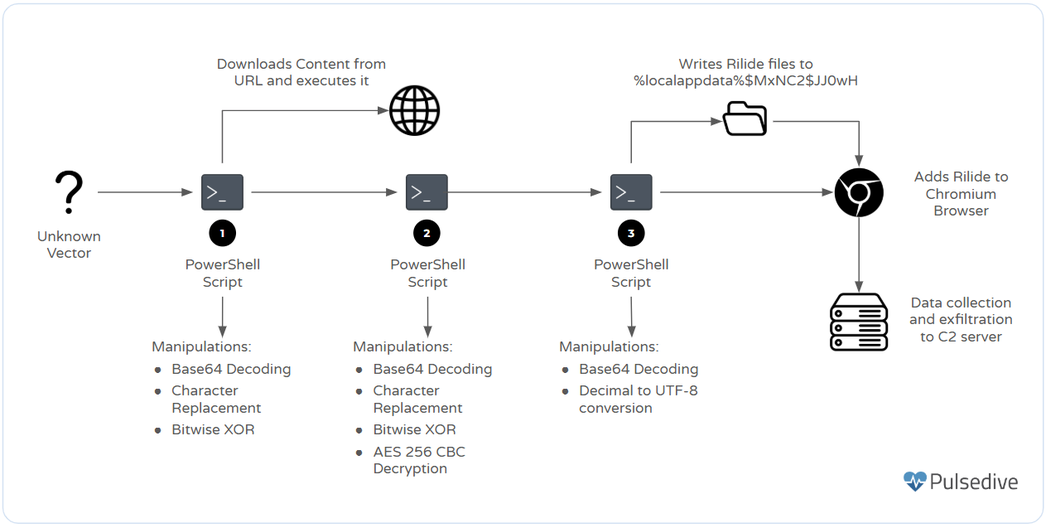
Summary: A new threat named “Rilide” has emerged as a malicious browser extension that steals sensitive user information, primarily targeting Chromium-based browsers. Disguised as legitimate extensions like Google Drive, Rilide employs deceptive tactics including phishing campaigns and PowerShell loaders to install itself and capture data such as passwords and cryptocurrency credentials.…
Read More 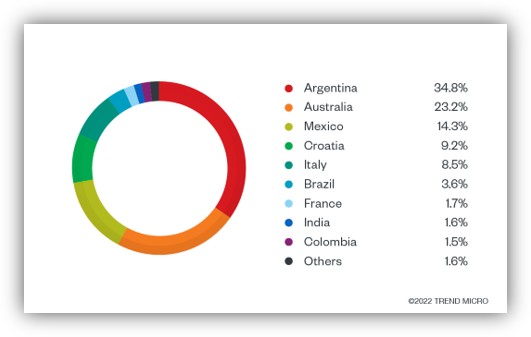






 THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More