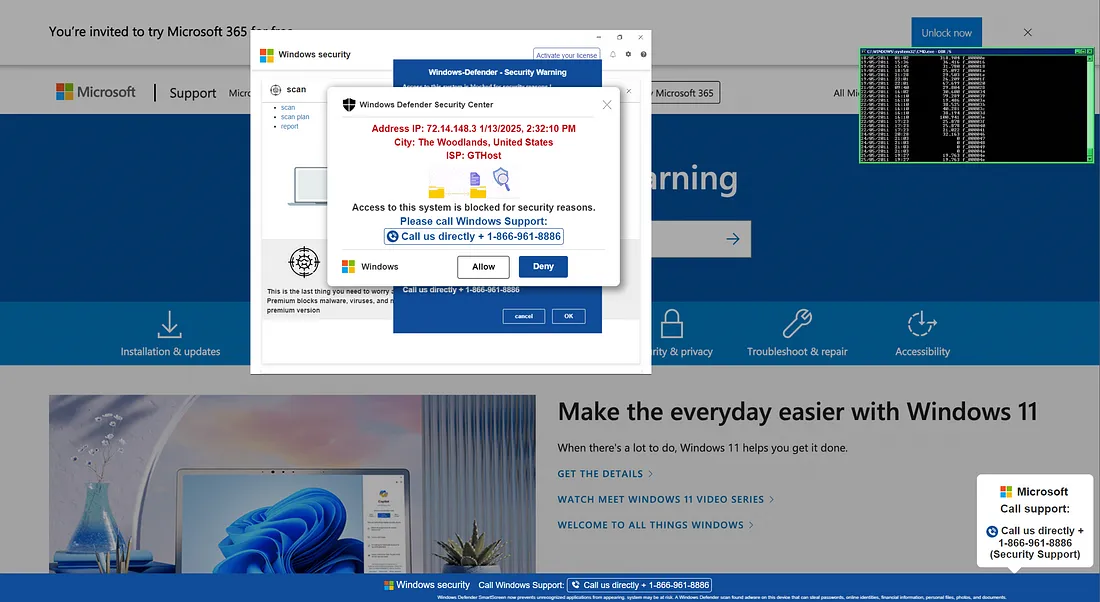
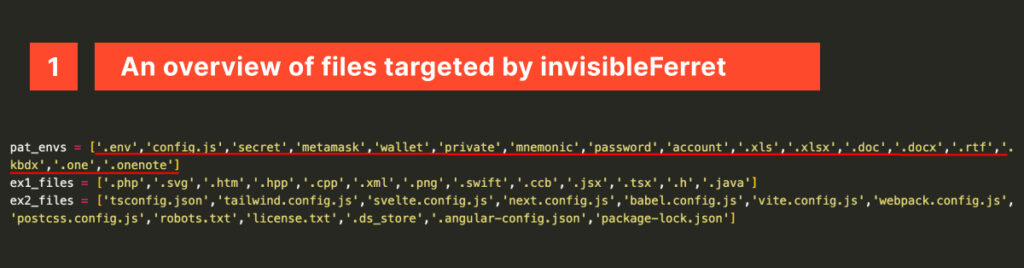
Summary: A report by Recorded Future details the operations of a Russian crypto scamming group known as Crazy Evil, which utilizes advanced techniques and malware to conduct scams on social media, targeting cryptocurrencies and digital assets. The group has been active since 2021 and is linked to multiple active scams, reportedly generating over million in illicit revenue while compromising tens of thousands of devices globally.…
Read More