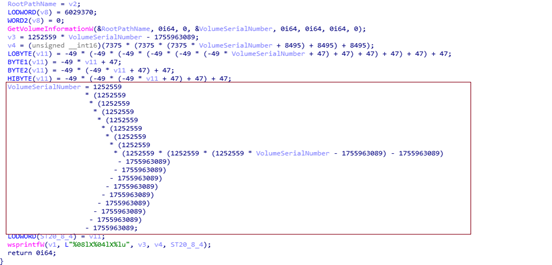
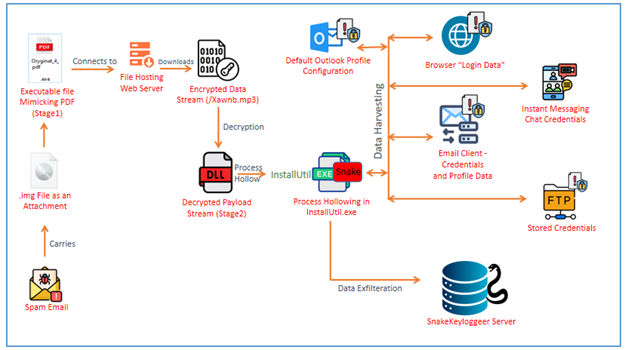
This article discusses various known attack surfaces and potential risks associated with GitLab, highlighting a range of vulnerabilities, including Remote Code Execution (RCE), SSRF, XSS, and permission escalation issues. The information covers the history of vulnerabilities, their impact, and famous cases, emphasizing the importance of security measures for self-managed GitLab instances.…
Read More