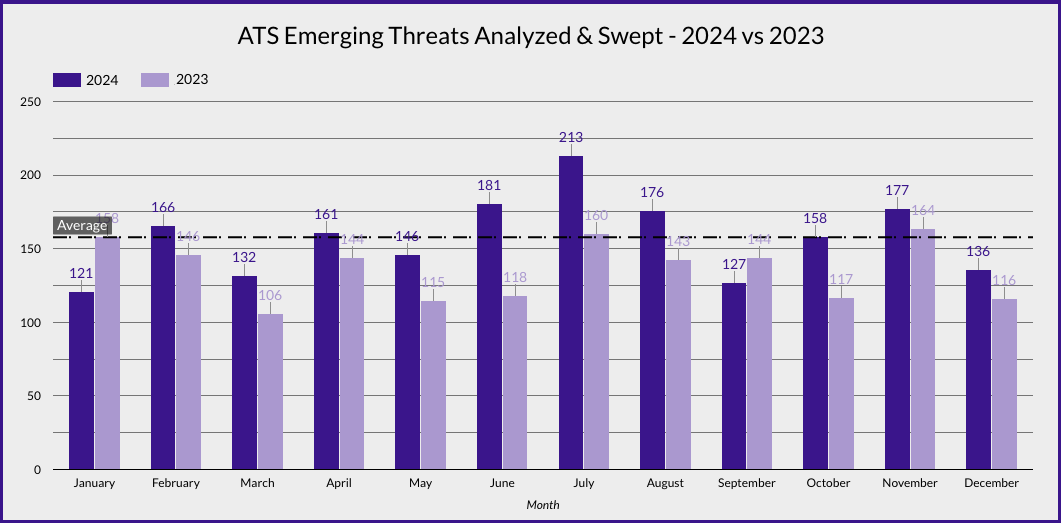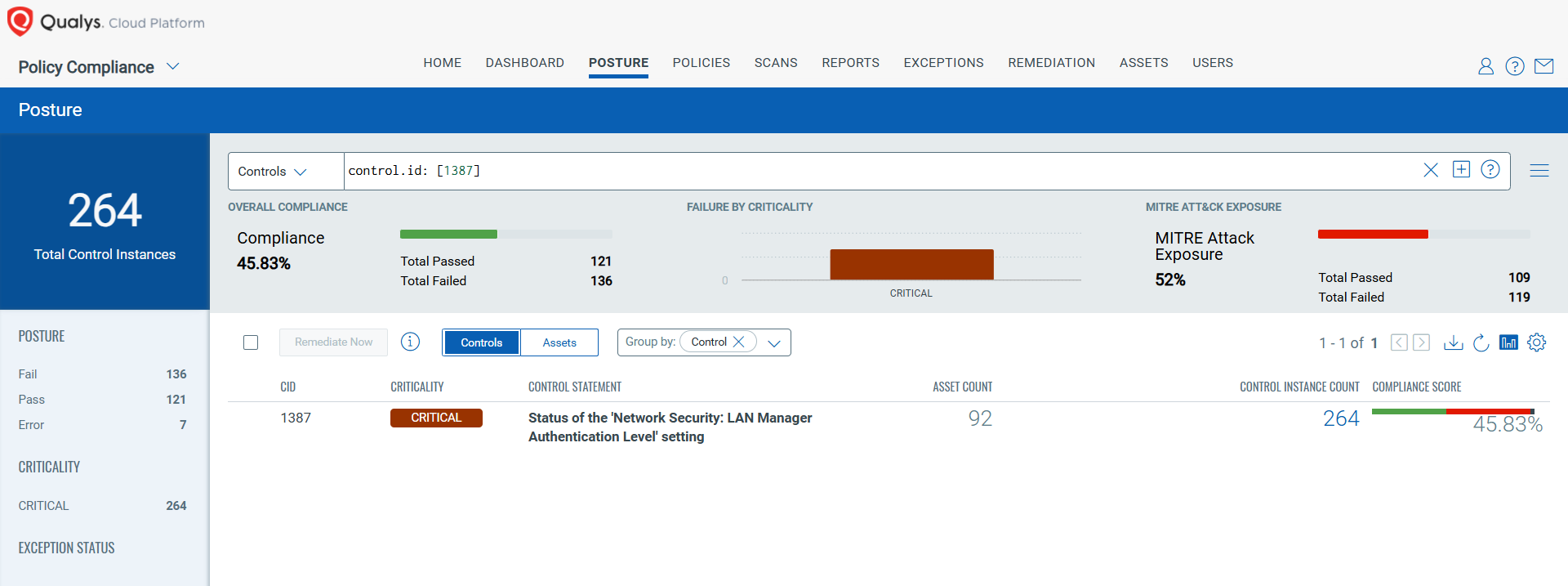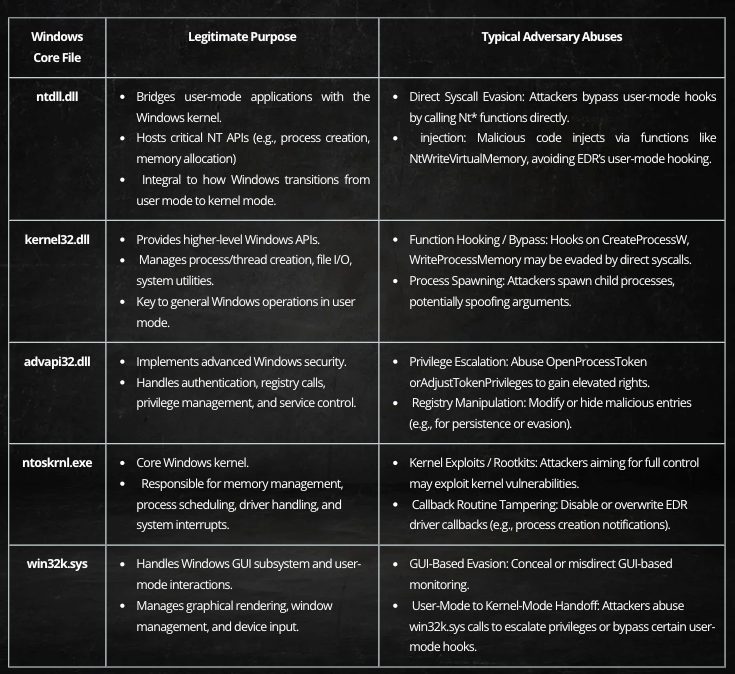
Endpoint Detection and Response (EDR) solutions are crucial for modern cybersecurity, enabling quick threat detection and response through extensive telemetry. However, attackers utilize various evasion techniques to bypass these systems, exploiting vulnerabilities in EDR architecture and Windows core files. This guide provides insights into EDR monitoring, evasion methods, and defensive strategies.…
Read More

_Luis_Moreira_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)