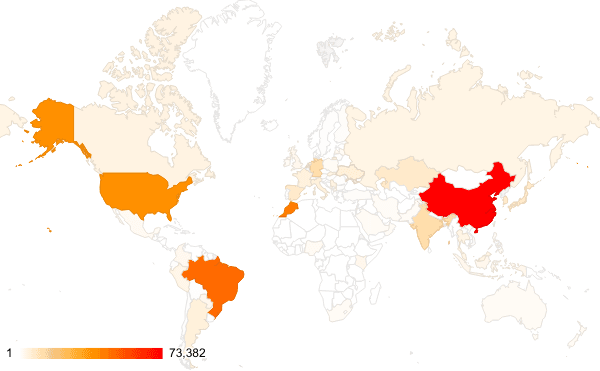
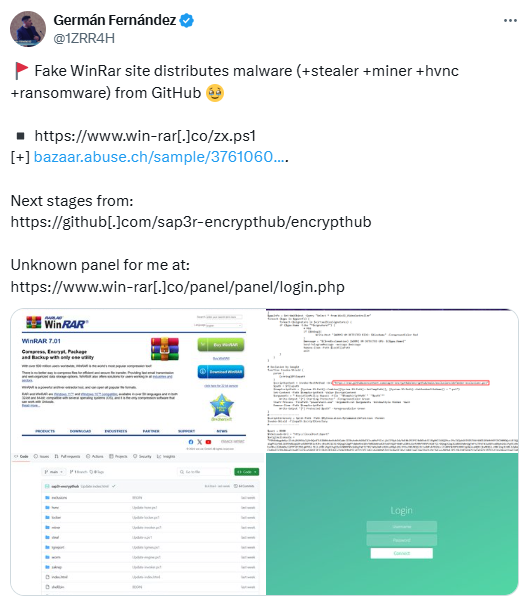
Summary: A critical security vulnerability (CVE-2025-31103) has been identified in a-blog cms, enabling attackers to exploit untrusted data deserialization and potentially execute arbitrary scripts on affected web servers. The Japan Computer Emergency Response Team (JPCERT/CC) has highlighted the urgency of the issue, as attackers have already begun targeting vulnerable versions of the software.…
Read More