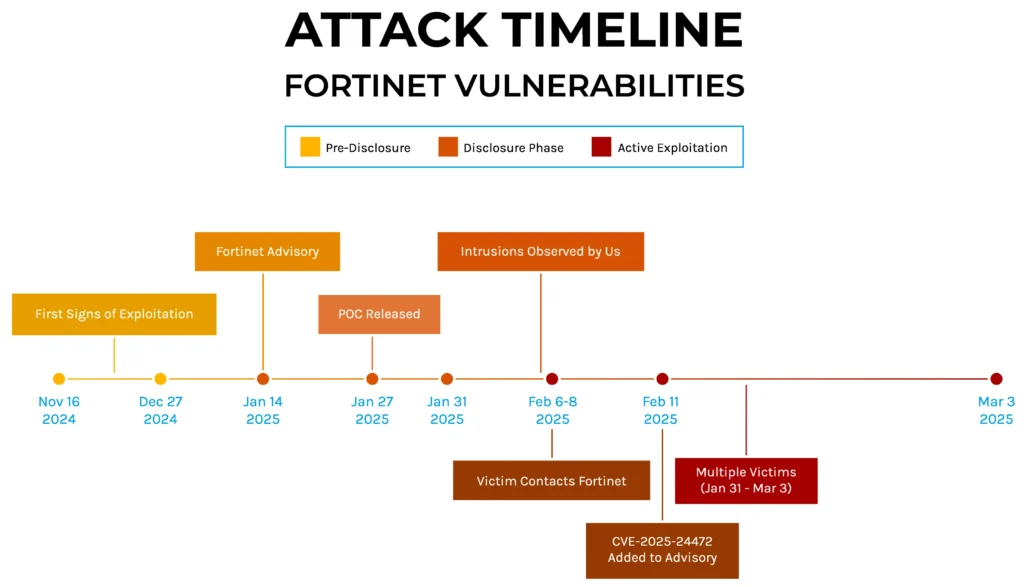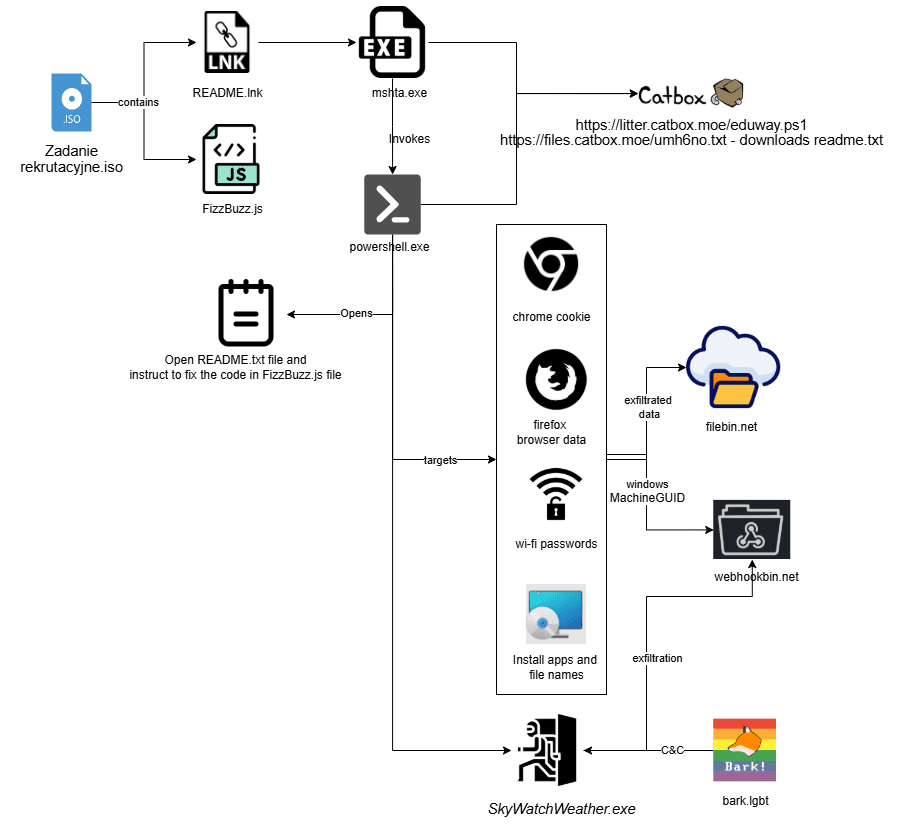
A targeted social engineering campaign has emerged, with a GitHub repository posing as a coding challenge aimed specifically at Polish-speaking developers. The campaign utilizes a malicious ISO file that, when executed, installs a backdoor called “FogDoor,” which collects sensitive information and communicates with a social media platform to execute commands.…
Read More 
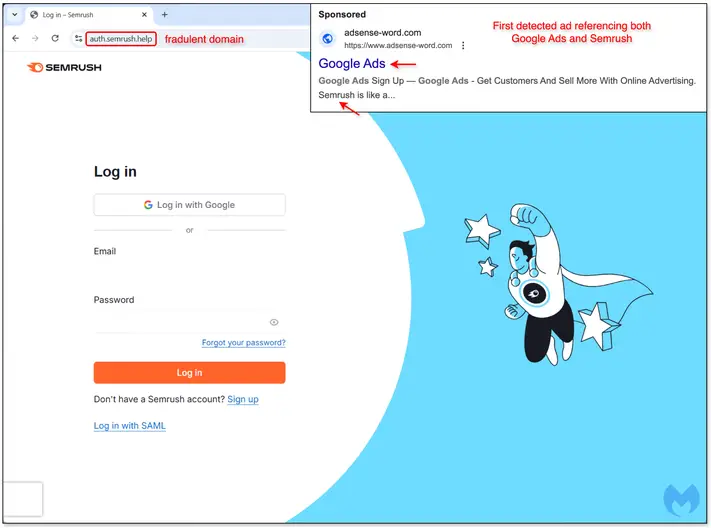




 THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More