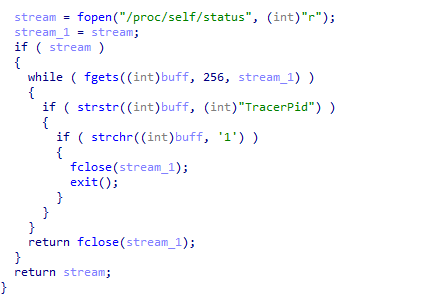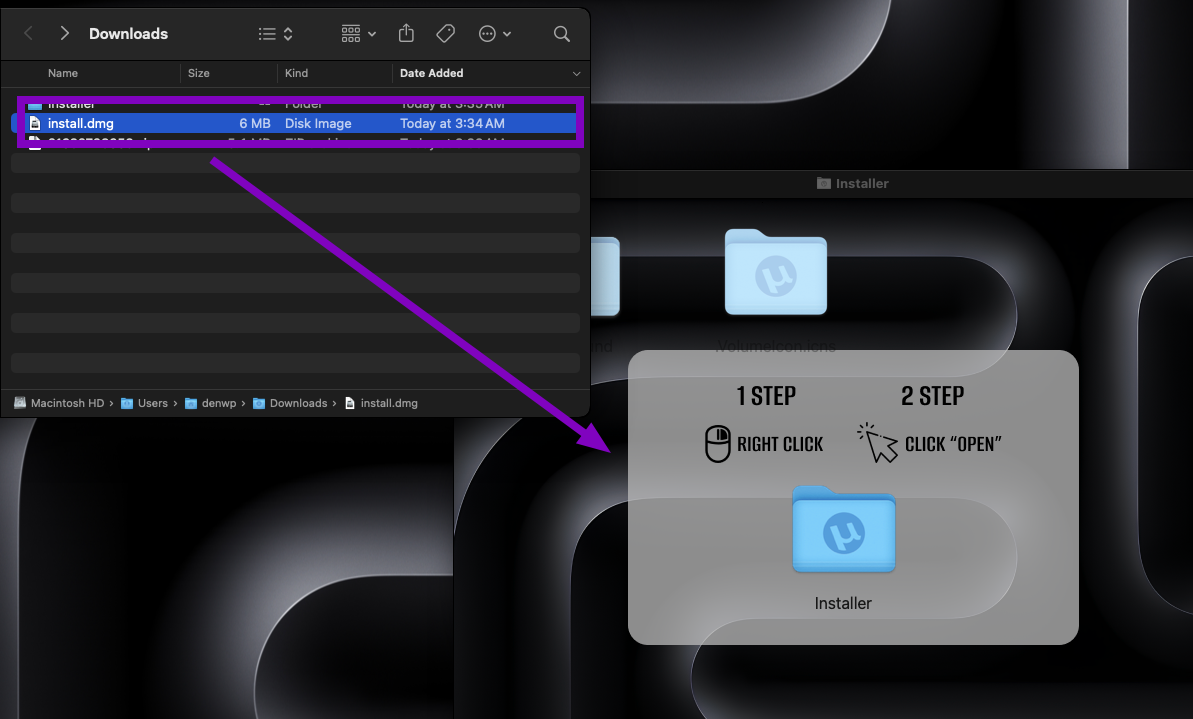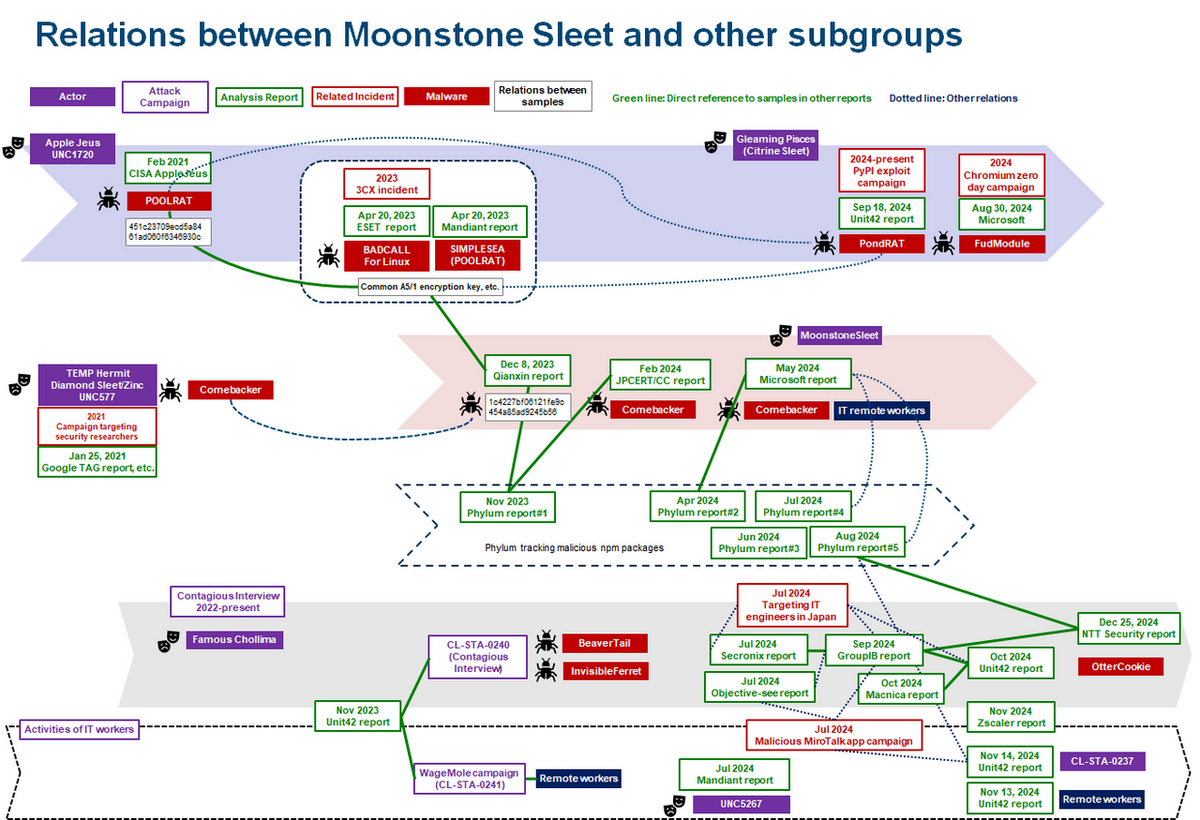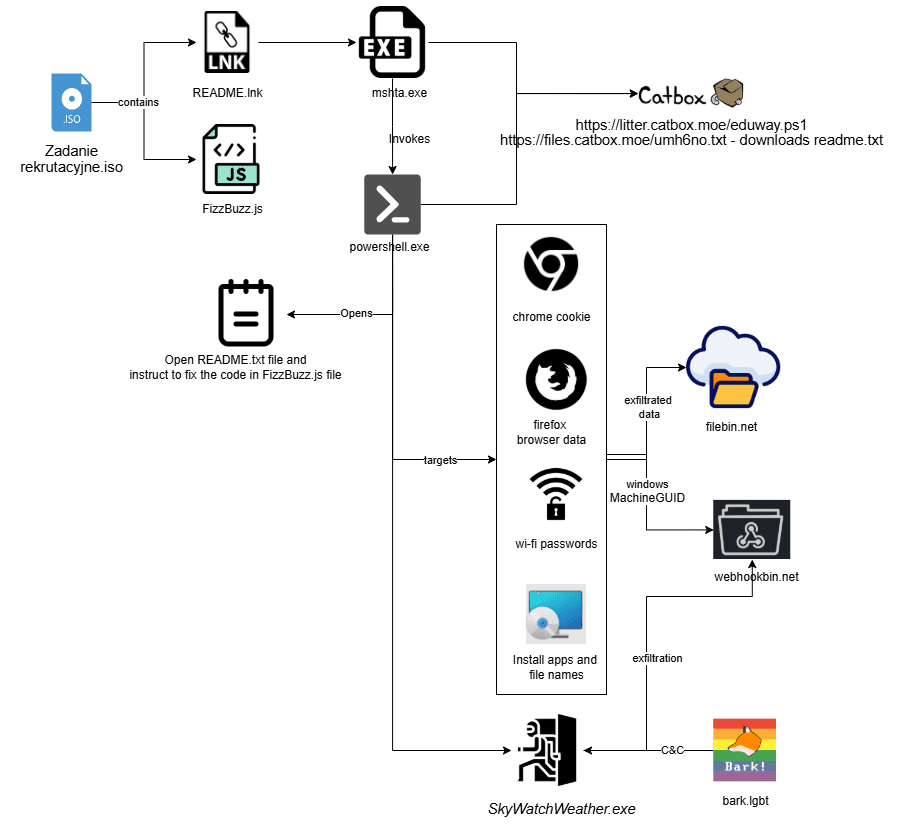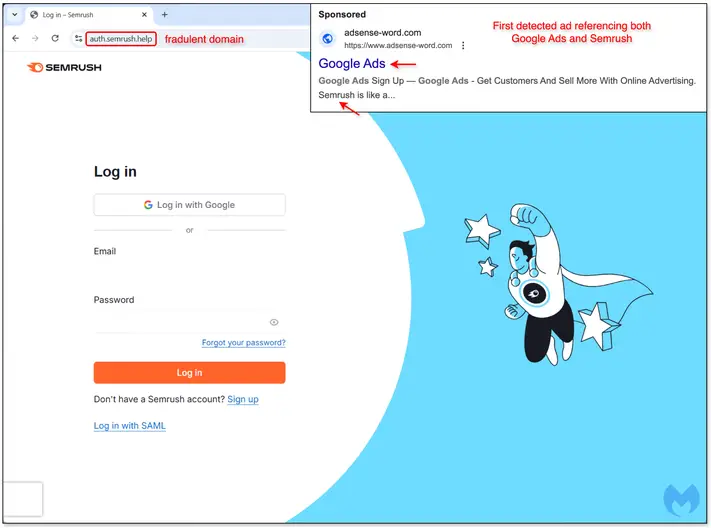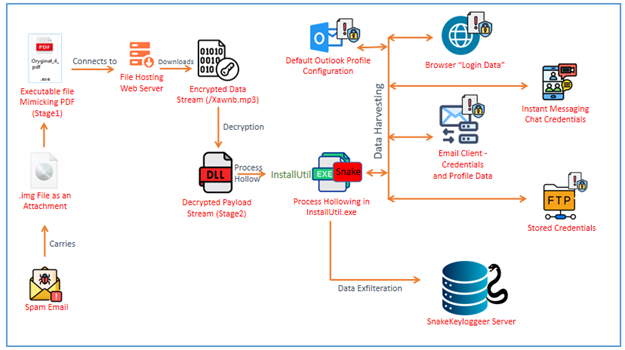
The SnakeKeylogger campaign illustrates a sophisticated credential-stealing threat targeting both individuals and businesses. Utilizing multi-stage infection techniques, it cleverly evades detection while harvesting sensitive data from various platforms. Attackers employ malicious spam emails containing disguised executable files to initiate the infection. Affected: Individuals, Businesses, Email Clients, Web Browsers, FTP Clients.…
Read More