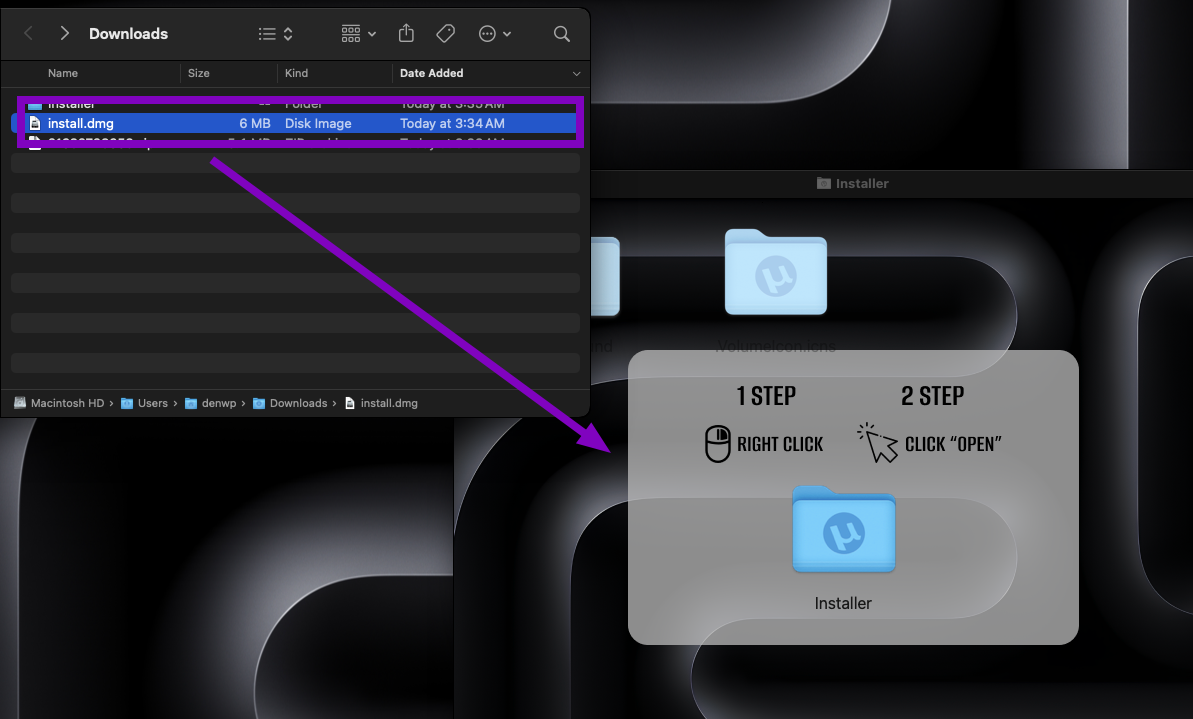
Summary: A new version of AMOS Stealer specifically targeting macOS has emerged, effectively evading detection and exploiting system vulnerabilities to exfiltrate sensitive data. This malware circumvents macOS Gatekeeper through user interaction and is designed to steal credentials, cryptocurrency information, and personal files. Security researcher Tonmoy Jitu has detailed its evasion techniques and functionality in a comprehensive analysis.…
Read More 





 THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More