Threat Actor: Unknown | unknown Victim: Tails Users | Tails Users
Key Point :
Critical vulnerabilities in Tails 6.10 and earlier versions could allow persistent malware installation via Tails Upgrader.…
Threat Actor: Unknown | unknown Victim: Tails Users | Tails Users
Key Point :
Critical vulnerabilities in Tails 6.10 and earlier versions could allow persistent malware installation via Tails Upgrader.…
“`html
Check Point Research has identified a new version of the Banshee macOS stealer malware, which has been evading detection since September 2024. The malware targets macOS users, stealing sensitive information and utilizing an encryption algorithm similar to Apple’s XProtect. Despite the shutdown of its original operations after a code leak, Banshee continues to be distributed through phishing websites and malicious GitHub repositories.…

Threat Actor: UNC5221 | UNC5221 Victim: Ivanti | Ivanti
Key Point :
Mandiant identified exploitation of CVE-2025-0282 by Chinese hackers, linked to previous attacks on Ivanti products.…
Threat Actor: Microsoft | Microsoft Victim: macOS users | macOS users
Key Point :
Issue affects macOS 15 Sequoia users when opening or saving files in OneDrive.…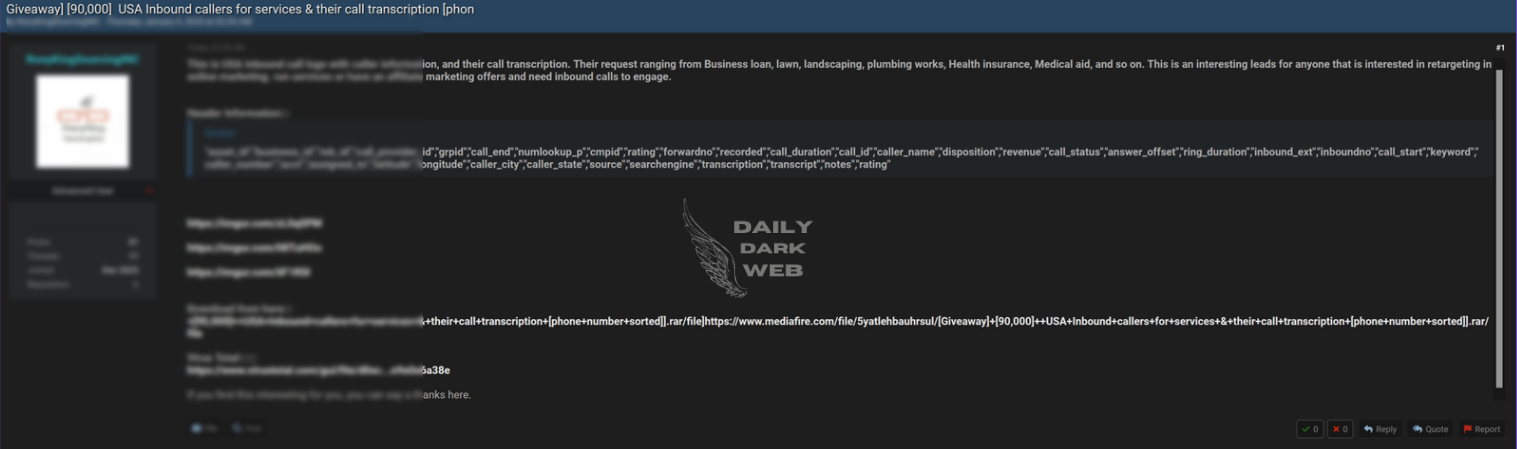
Key Points :
A reported data breach has exposed sensitive information from 90,000 inbound calls. The leaked data includes detailed call transcriptions and associated phone numbers.…
Key Points :
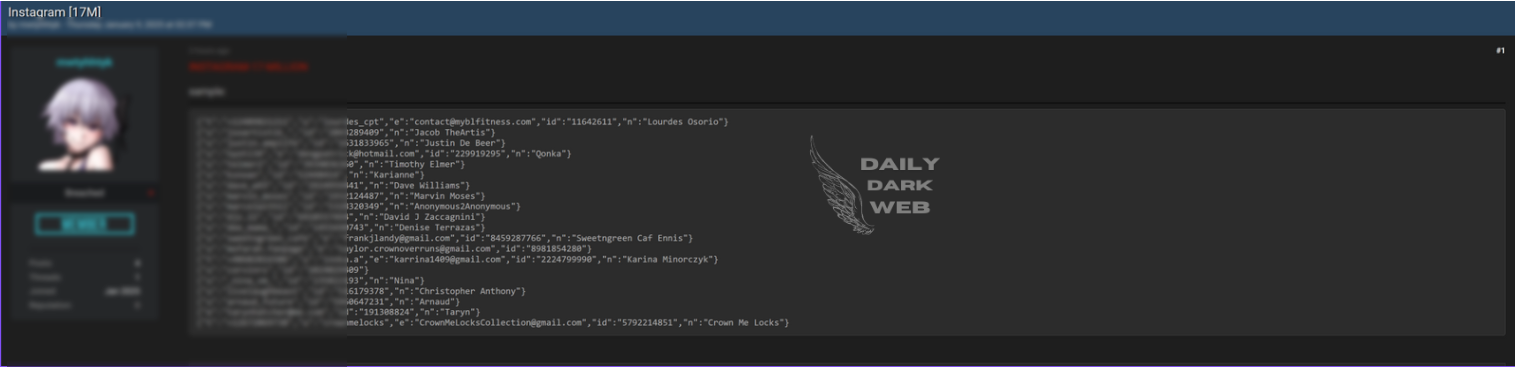
17 million Instagram users’ data exposed in a reported breach. Compromised data includes user IDs, email addresses, and phone numbers.…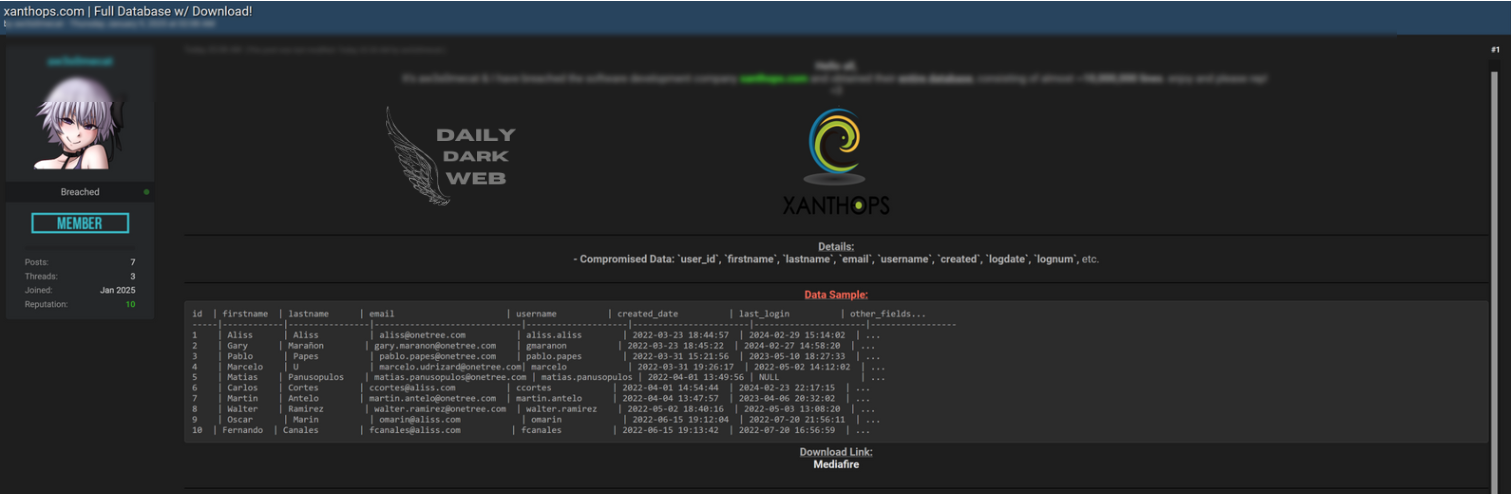
Key Points :
A significant data breach has exposed the full database of Xanthops.com. Compromised information includes sensitive user data such as names, email addresses, and encrypted passwords.…
Key Points :
Unauthorized access to the systems of two companies based in New Zealand has been reported. The breach includes access to sensitive corporate data, raising concerns about cybersecurity vulnerabilities.…
Threat Actor: Unknown | unknown Victim: Linux Systems | Linux Systems
Key Point :
The vulnerability affects OpenSSH versions 8.5p1 through 9.8p1 on glibc-based Linux systems.…
Keypoints :
Black Basta utilizes phishing emails to create a smokescreen for attacks.…
Threat Actor: UNC5337 | UNC5337 Victim: Ivanti | Ivanti
Key Point :
CVE-2025-0282 is a stack-based buffer overflow with a CVSS score of 9.0, affecting multiple Ivanti products.…
Keypoints :
The Azure Machine Learning (AML) service is used for data processing and integrates with other Azure services.…


Threat Actor: Unspecified | Unspecified Victim: Ivanti | Ivanti
Key Point :
Two vulnerabilities, CVE-2025-0282 (critical) and CVE-2025-0283 (high), have been identified in Ivanti’s products.…
Threat Actor: Cybercriminals | cybercriminals Victim: Medusind | Medusind
Key Point :
The breach exposed personal and health information, including health insurance details, payment information, and government IDs.…
Threat Actor: Initial Access Brokers (IABs) | Initial Access Brokers Victim: Various organizations | Amazon Web Services, Geico, ADT
Key Point :
IABs operate like legitimate businesses, offering tiered pricing and customer support for stolen access.…