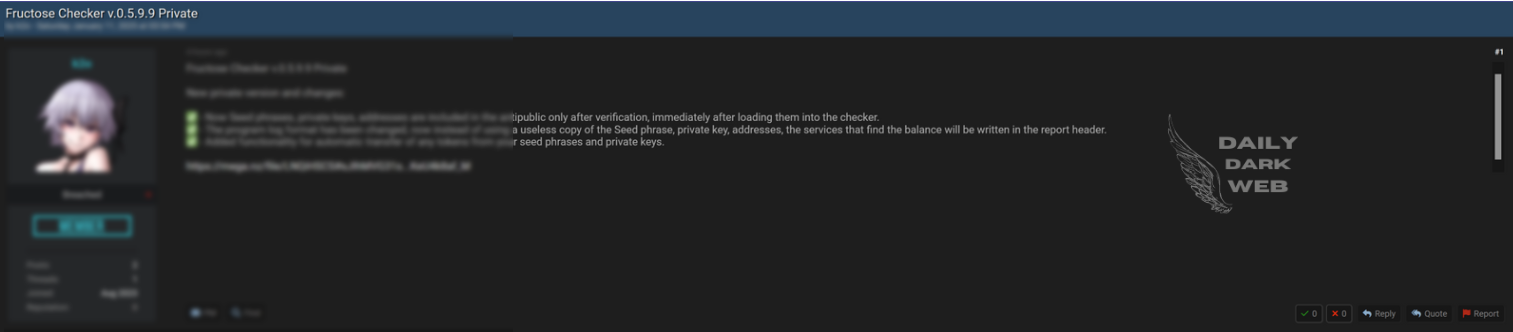
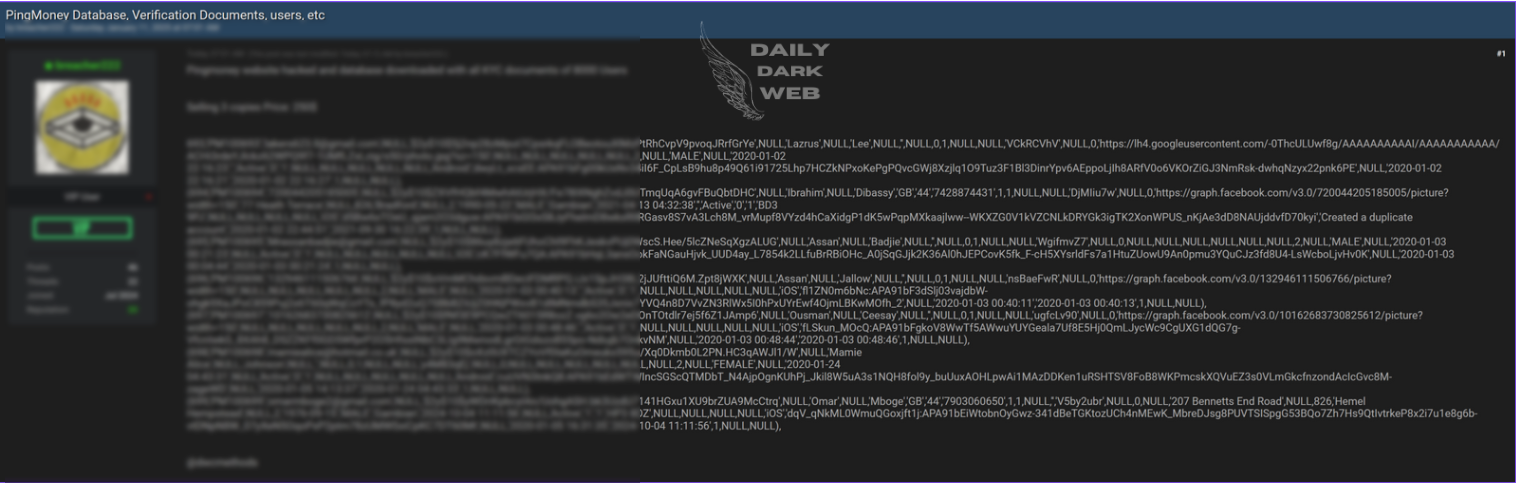
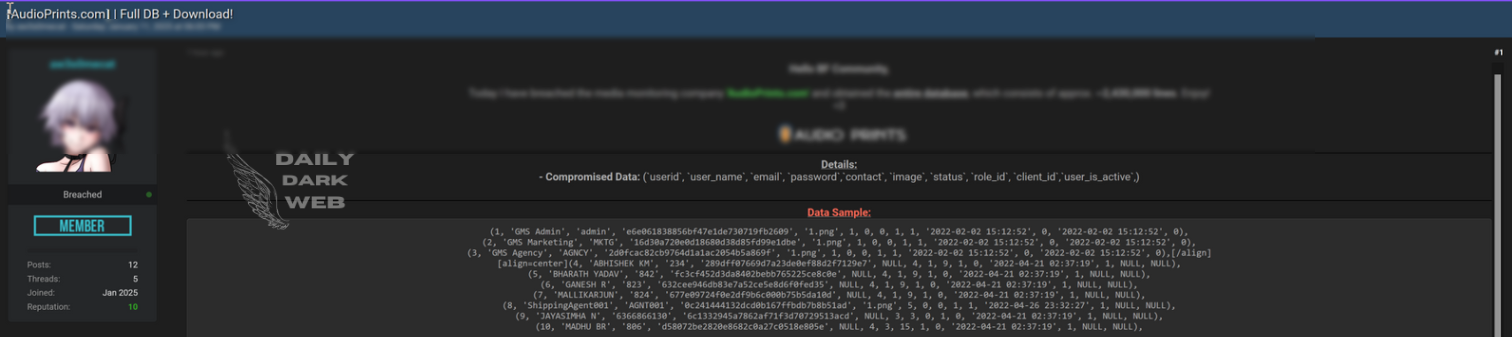
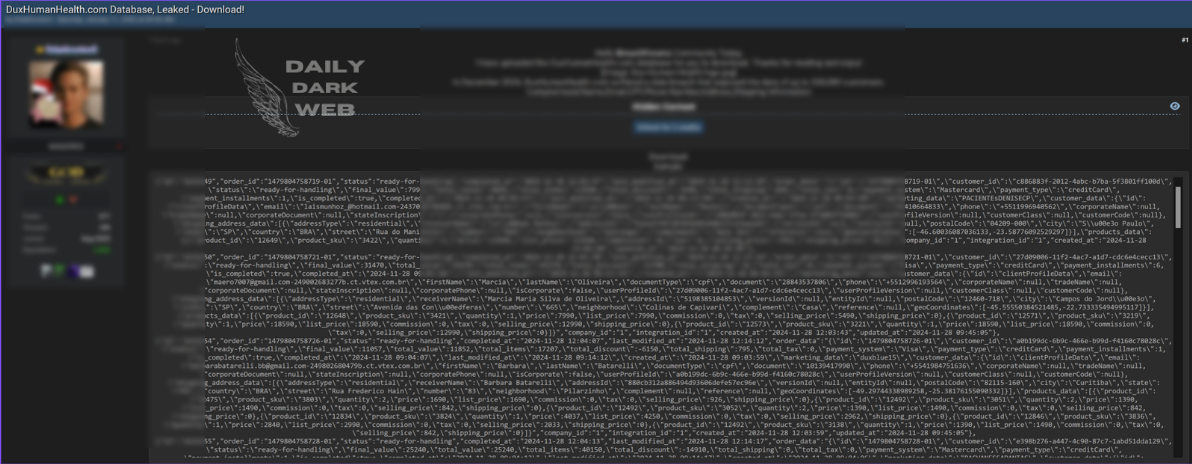
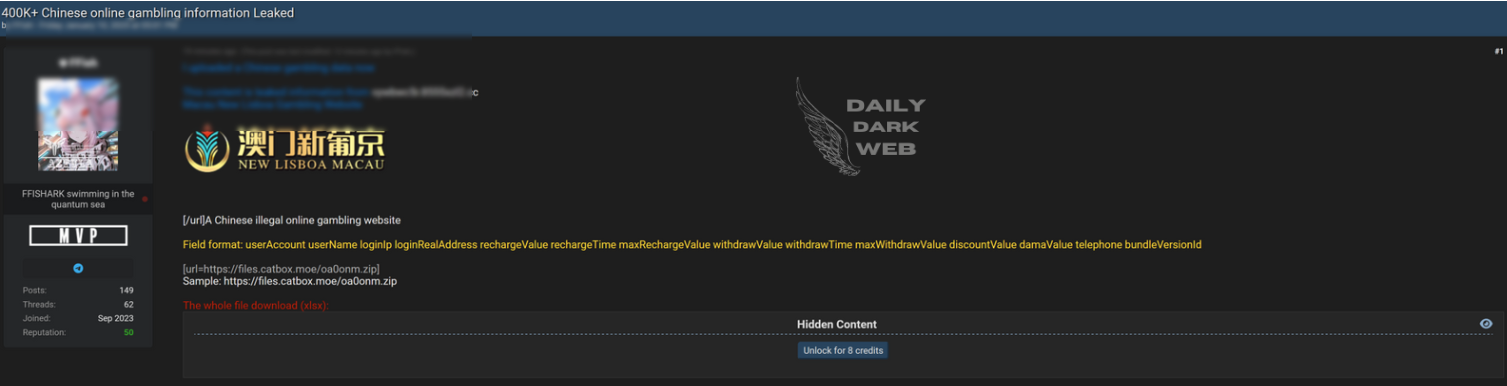
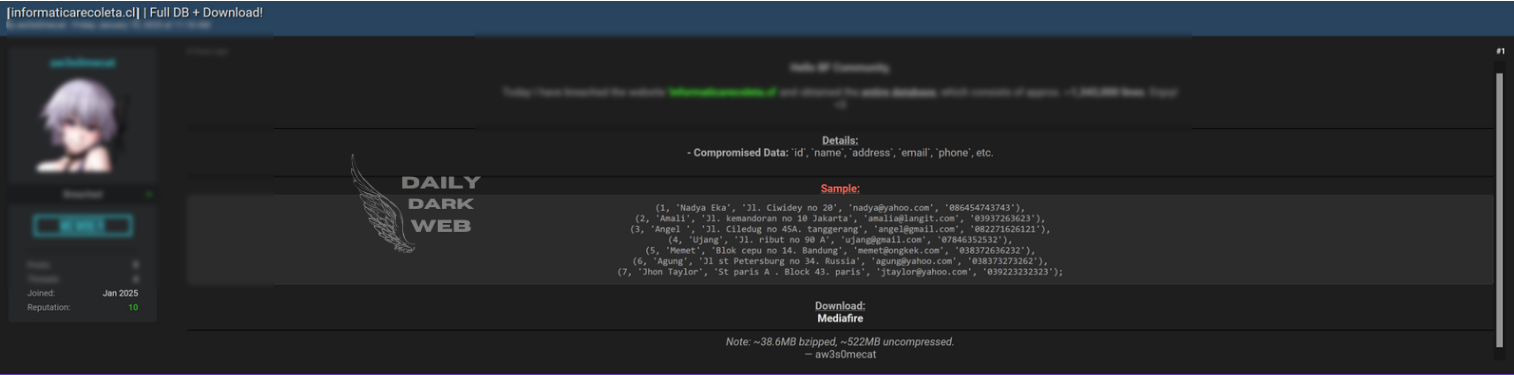
Key Points :
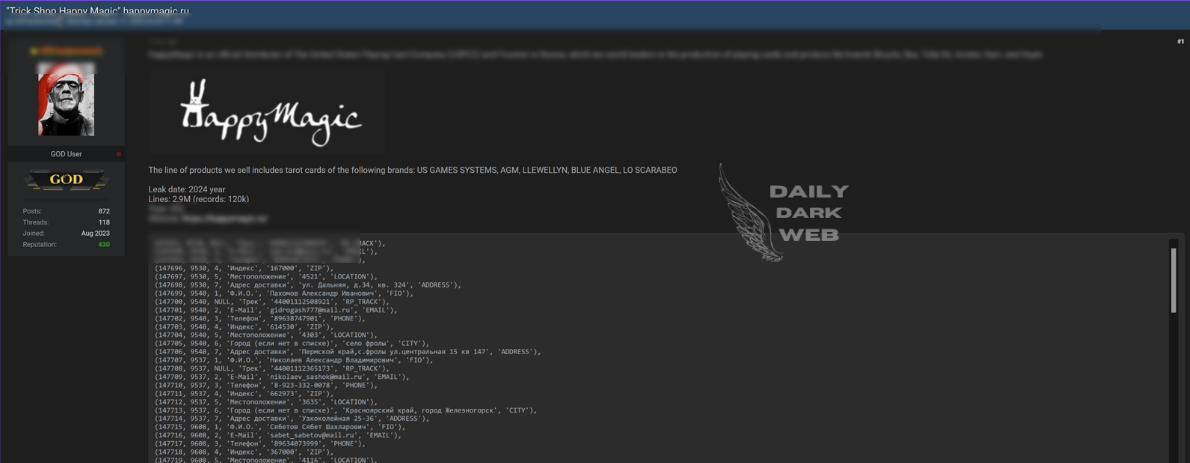
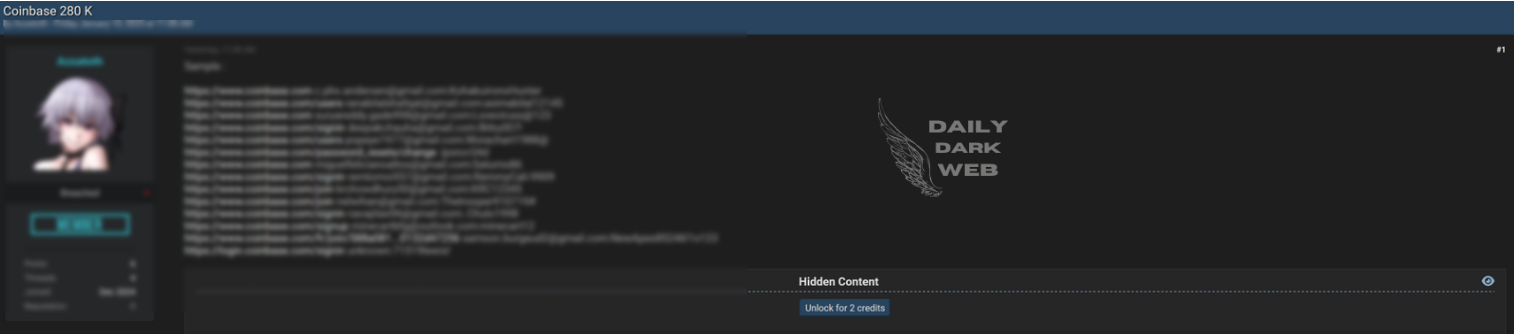
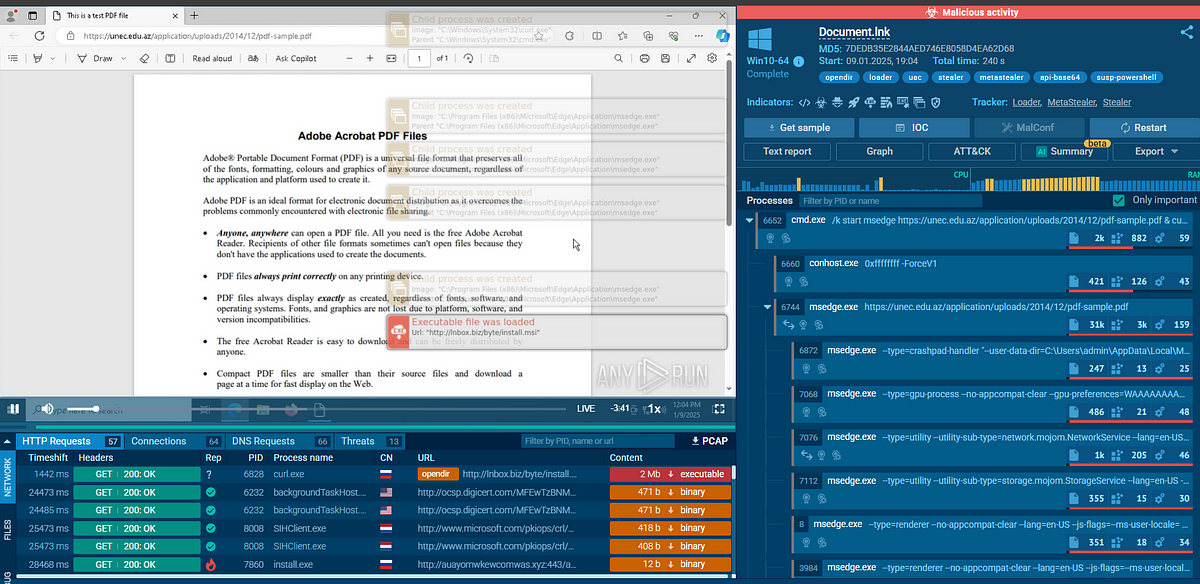
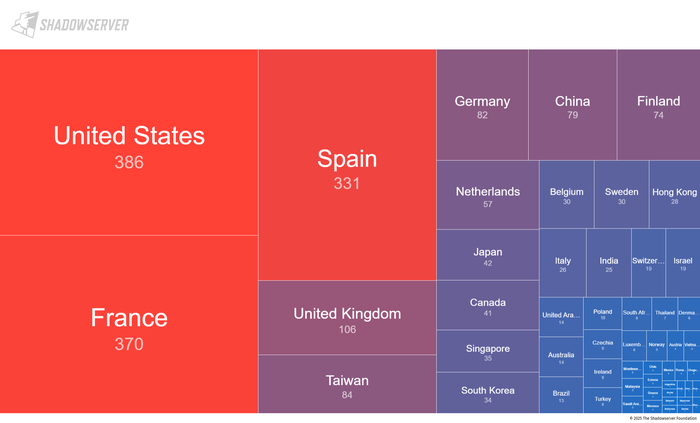
Leaked database made available in an online thread titled “FREE take it or go away lol.” Exact contents and extent of the data remain unclear. Raises concerns about unauthorized data sharing and risks to privacy and cybersecurity.…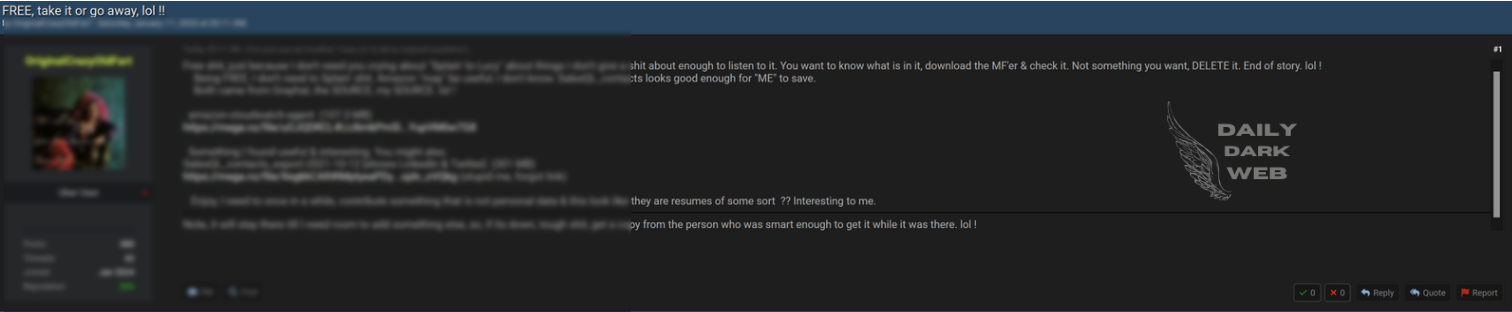
Victim: Unknown | unknown
Price: Free
Exfiltrated Data Type: Potentially personal, financial, or corporate information
Read More