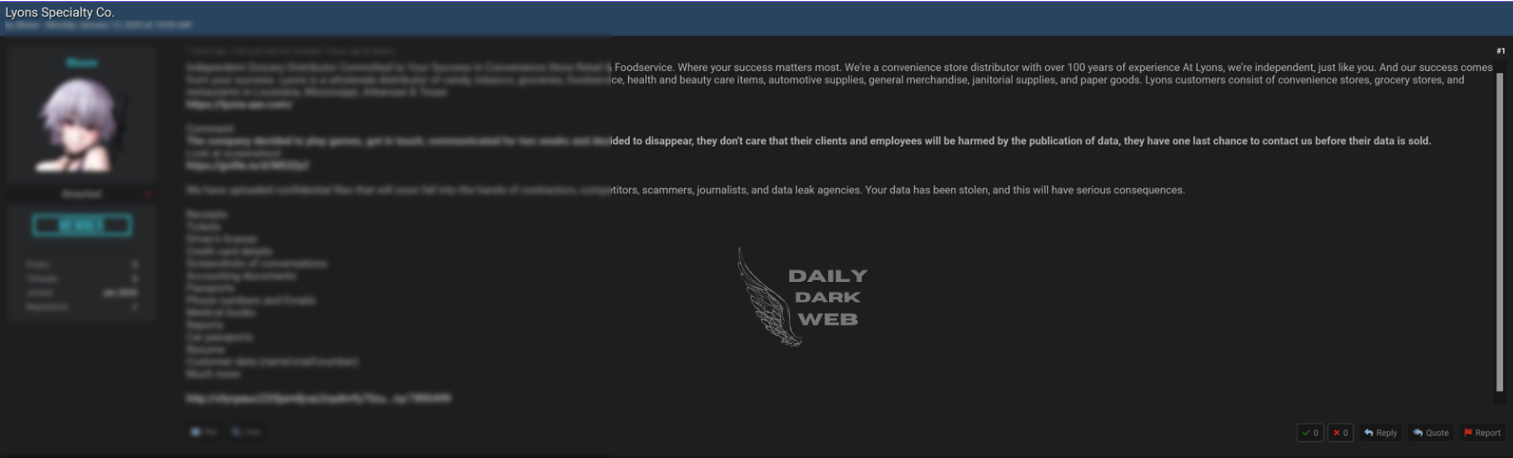
Key Points :
Massive data breach involving a leak of 1.27TB of data. Exposed data may include sensitive personal and corporate information. Highlights ongoing risks associated with large-scale data storage.…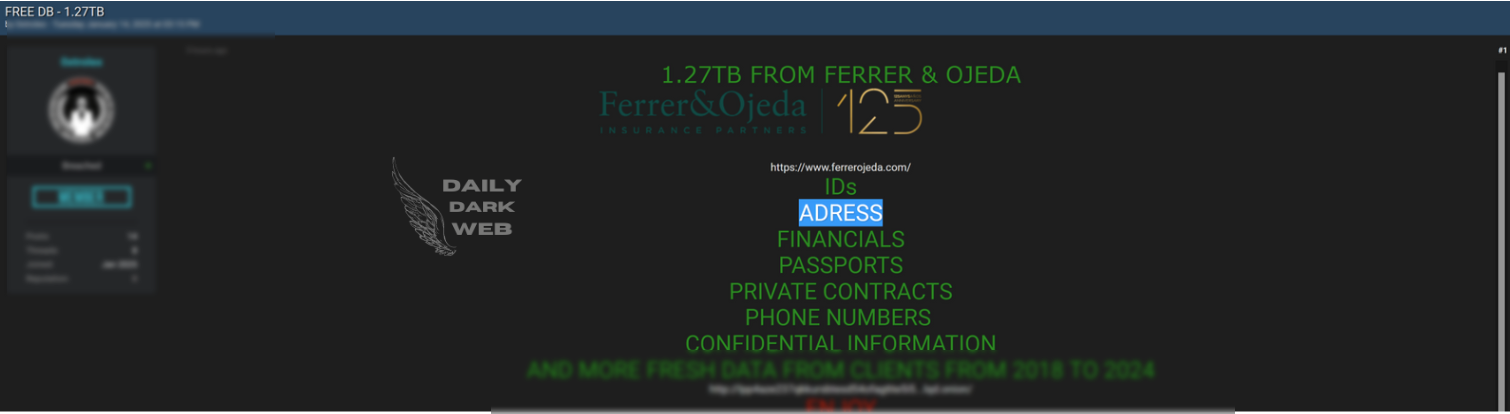
Victim: Unknown | Global Data Breach
Price: Not disclosed
Exfiltrated Data Type: Sensitive personal and corporate information
Read More





_Vladimir_Badaev_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)

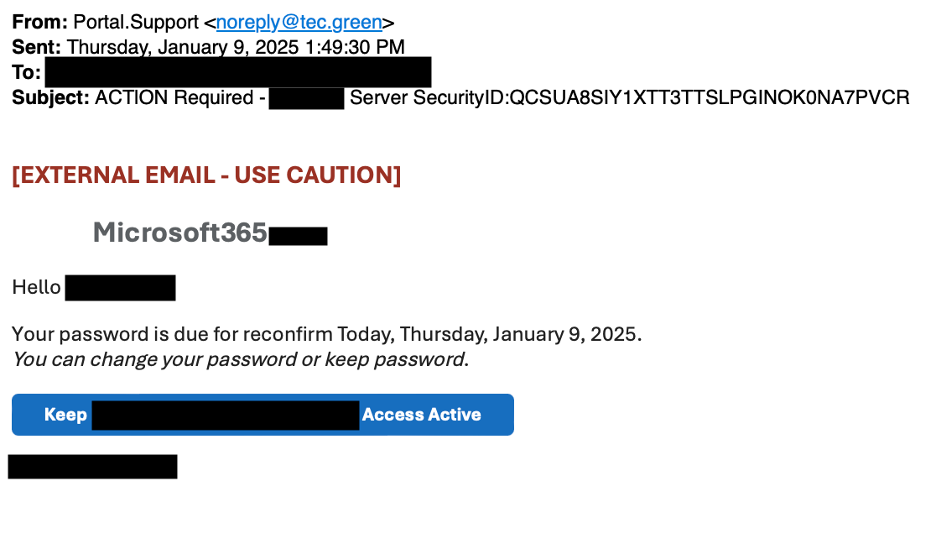
![⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [13 January] ⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [13 January]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh-GVBzJbXbnB628INcZeeGpxnFqxVpcaOaQnUH-g2FpiUGHCsUnPnPNYeuEKDvxOqHzeiB2fZWoNTOO81_P4b77zyyyuaSpWTBjahKirJJMtMXCEIvVUiqsIojlnyGL9pPkB8Dv5-wviS5poLJ_CIYdbkSxjPE4Psyh6mppkjg0M4rWF22fNSR9IgRUqwh/s728-rw-e365/recap.png)