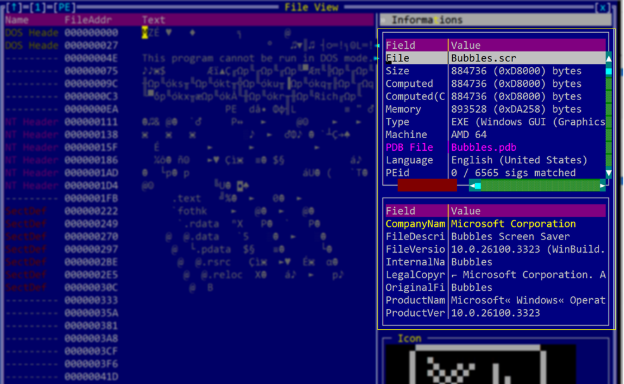
This research by Bitdefender Labs introduces the QWCrypt ransomware campaign, linked to the RedCurl group, marking a significant shift in their tactics from data exfiltration to ransomware. RedCurl has been operating since 2018 but has historically utilized Living-off-the-Land techniques for corporate espionage. Their targeting of specific infrastructures and the use of hypervisor encryption underscores a sophisticated evolution in their operational strategy, raising questions regarding their motivations and business model.…
Read More