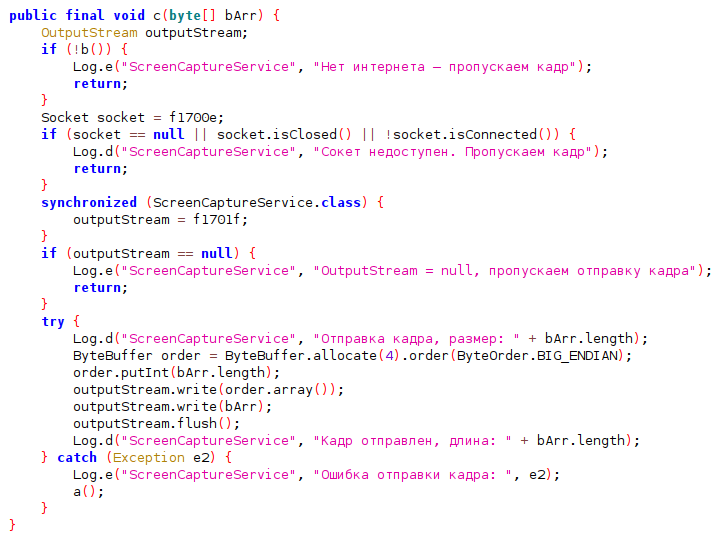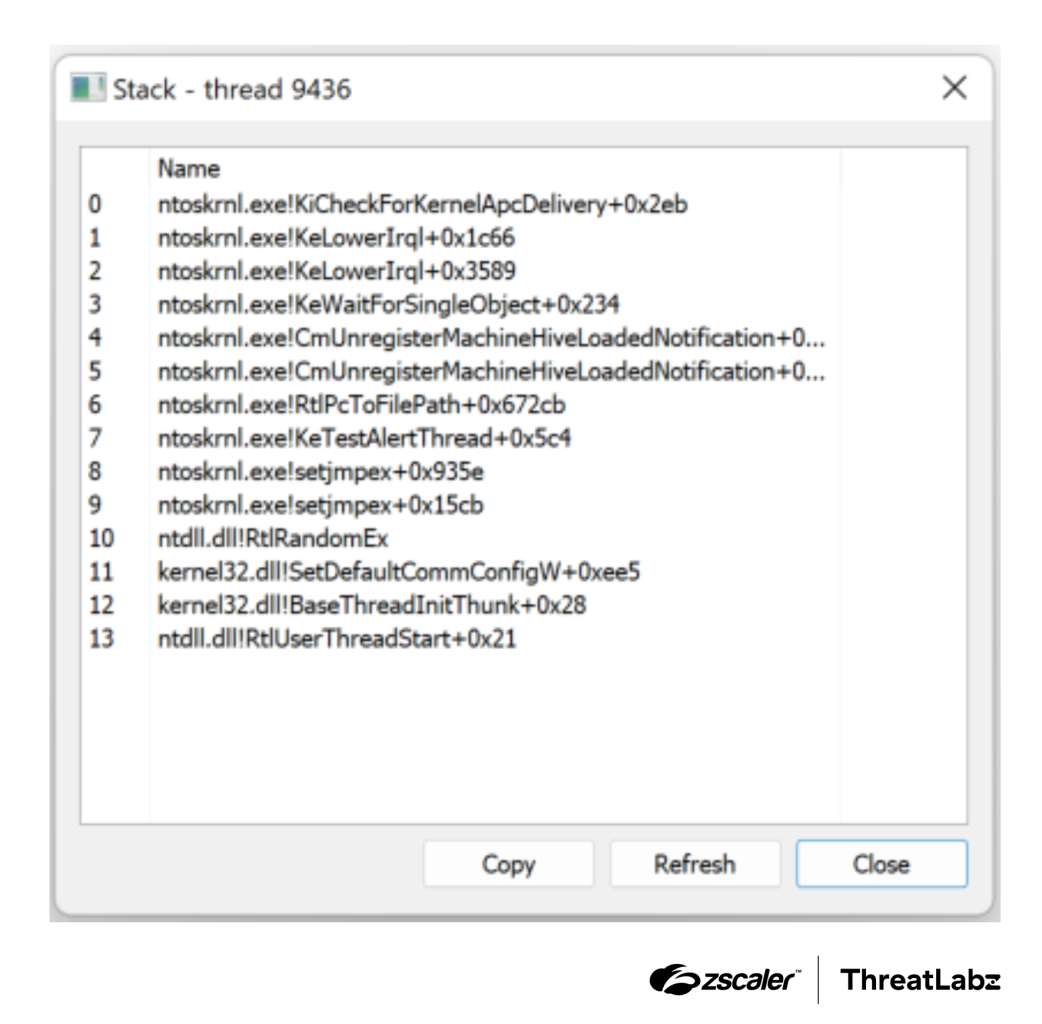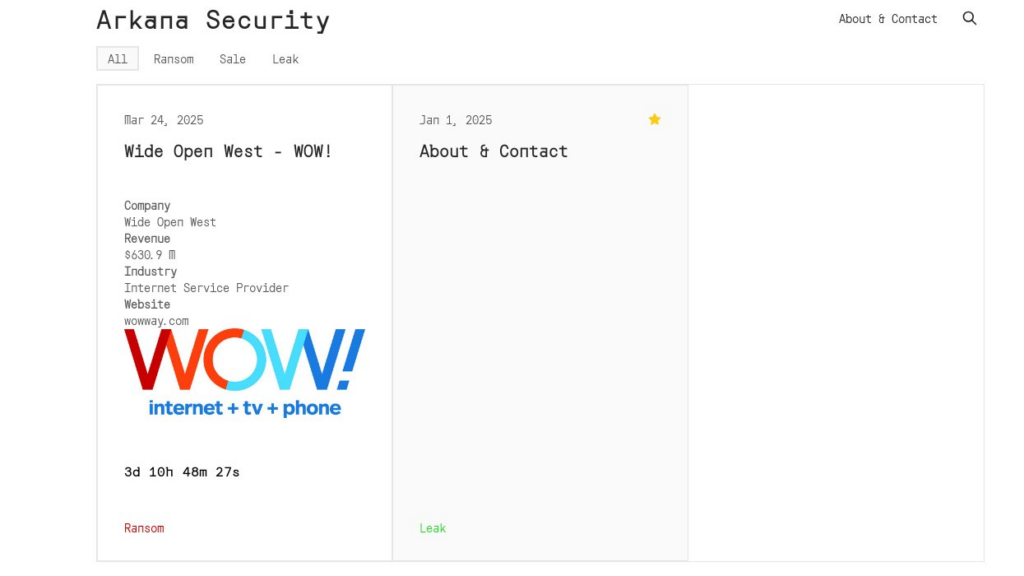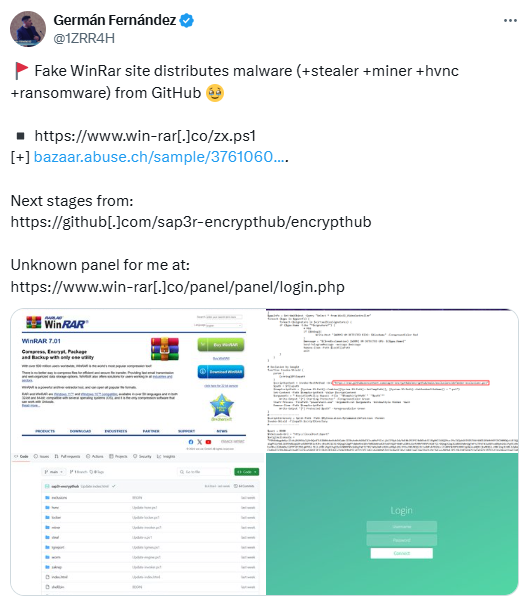
Trend Research reveals the exploits of Water Gamayun, a suspected Russian threat actor leveraging a zero-day vulnerability (CVE-2025-26633) in Microsoft Management Console to deploy malware. Their methods include custom payloads, data exfiltration techniques, and the use of backdoor malware. This campaign poses severe risks to organizations, including data theft and operational disruption.…
Read More