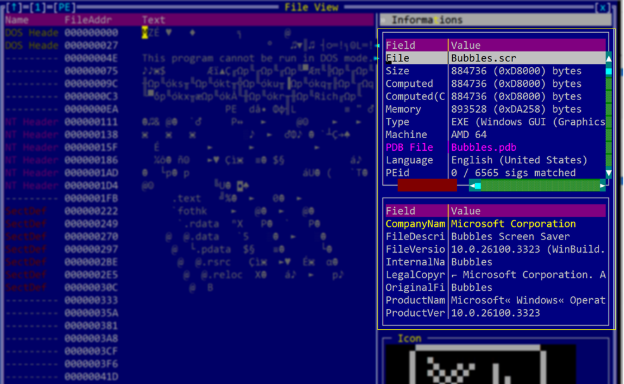
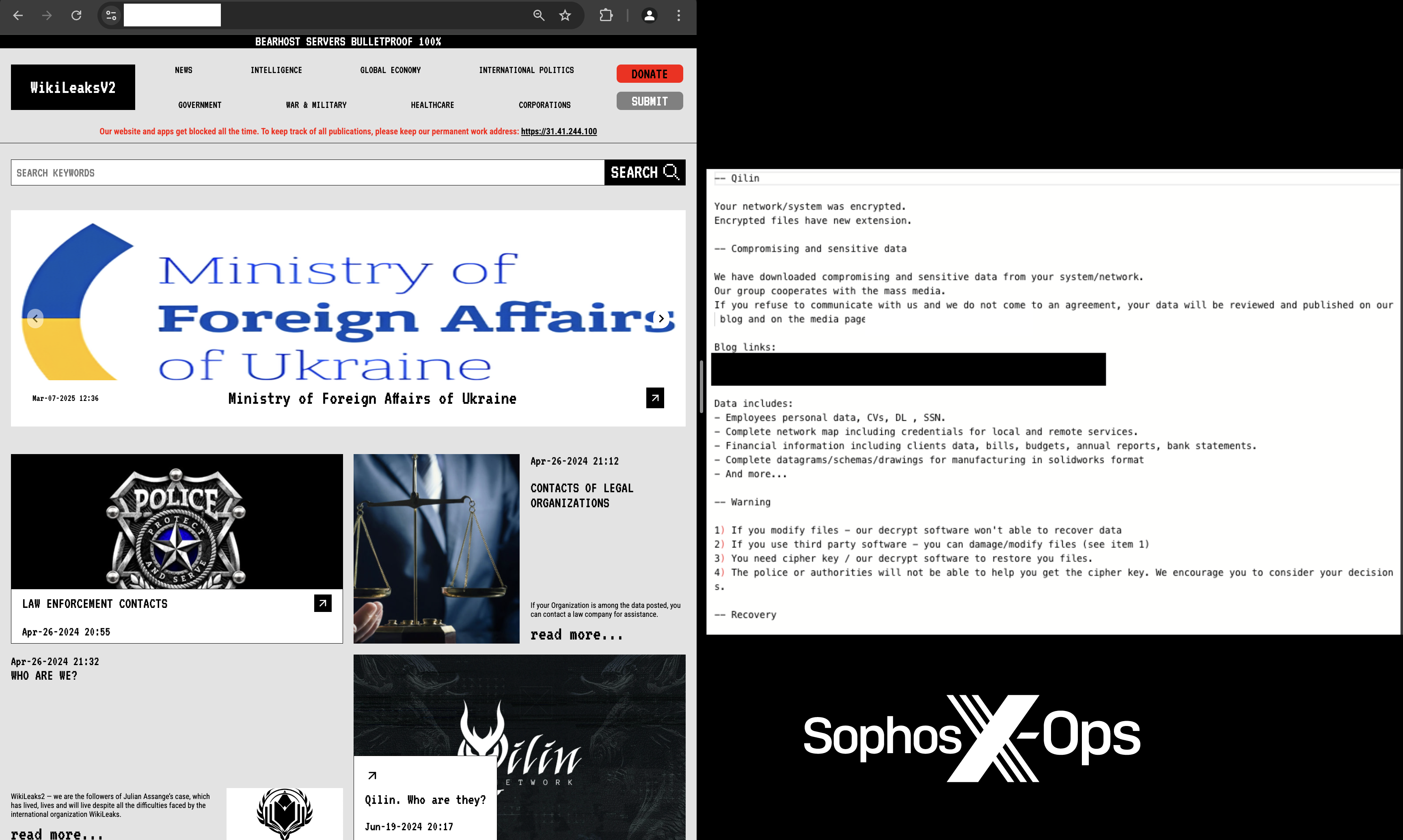
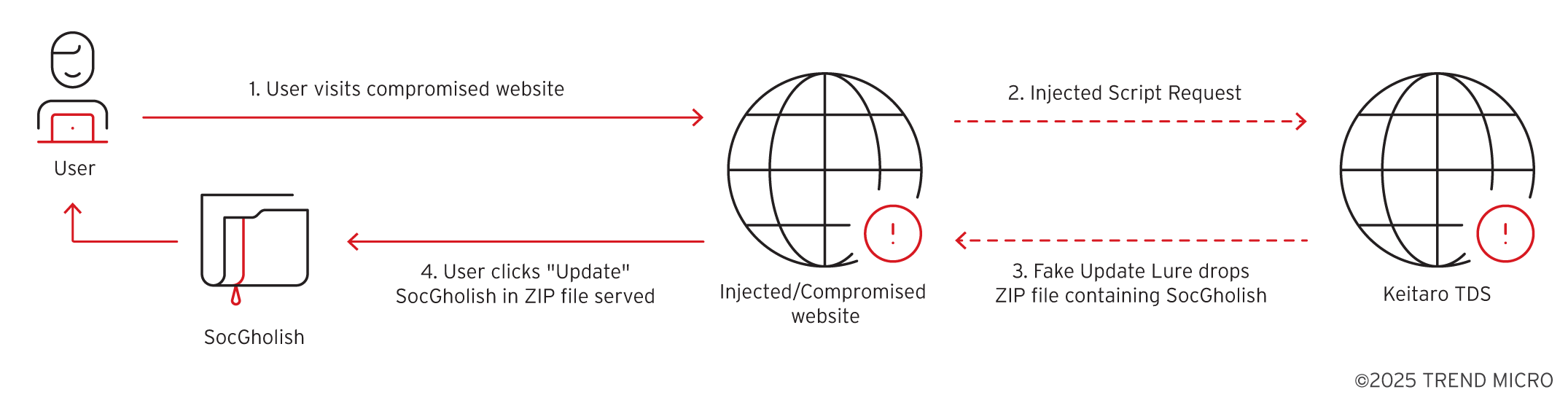
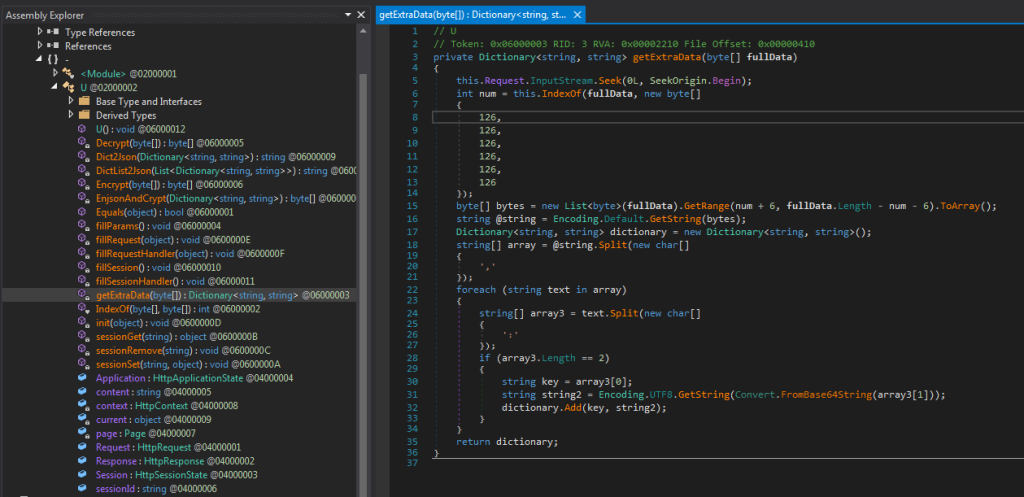
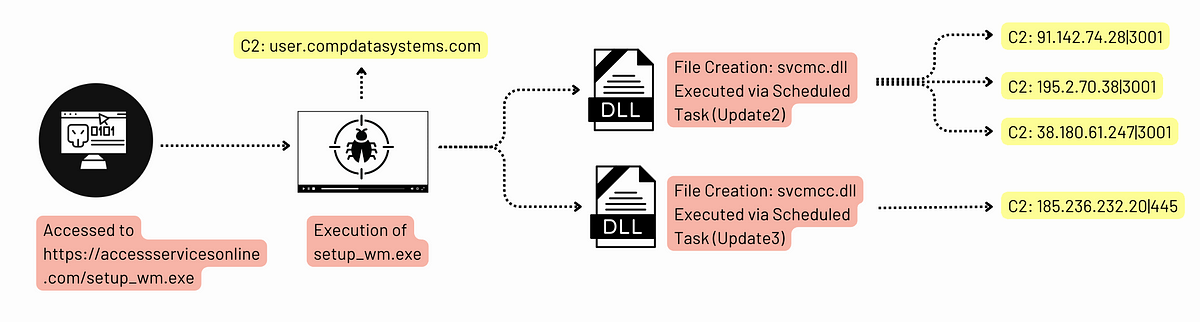
In recent spear-phishing attempts, the Konni APT has impersonated South Korean government entities such as the National Human Rights Commission and the National Police Agency to instigate fear of human rights violations and hacking incidents. The attacks utilize deception tactics to install malicious files, notably LNK shortcuts and AutoIT scripts.…
Read More