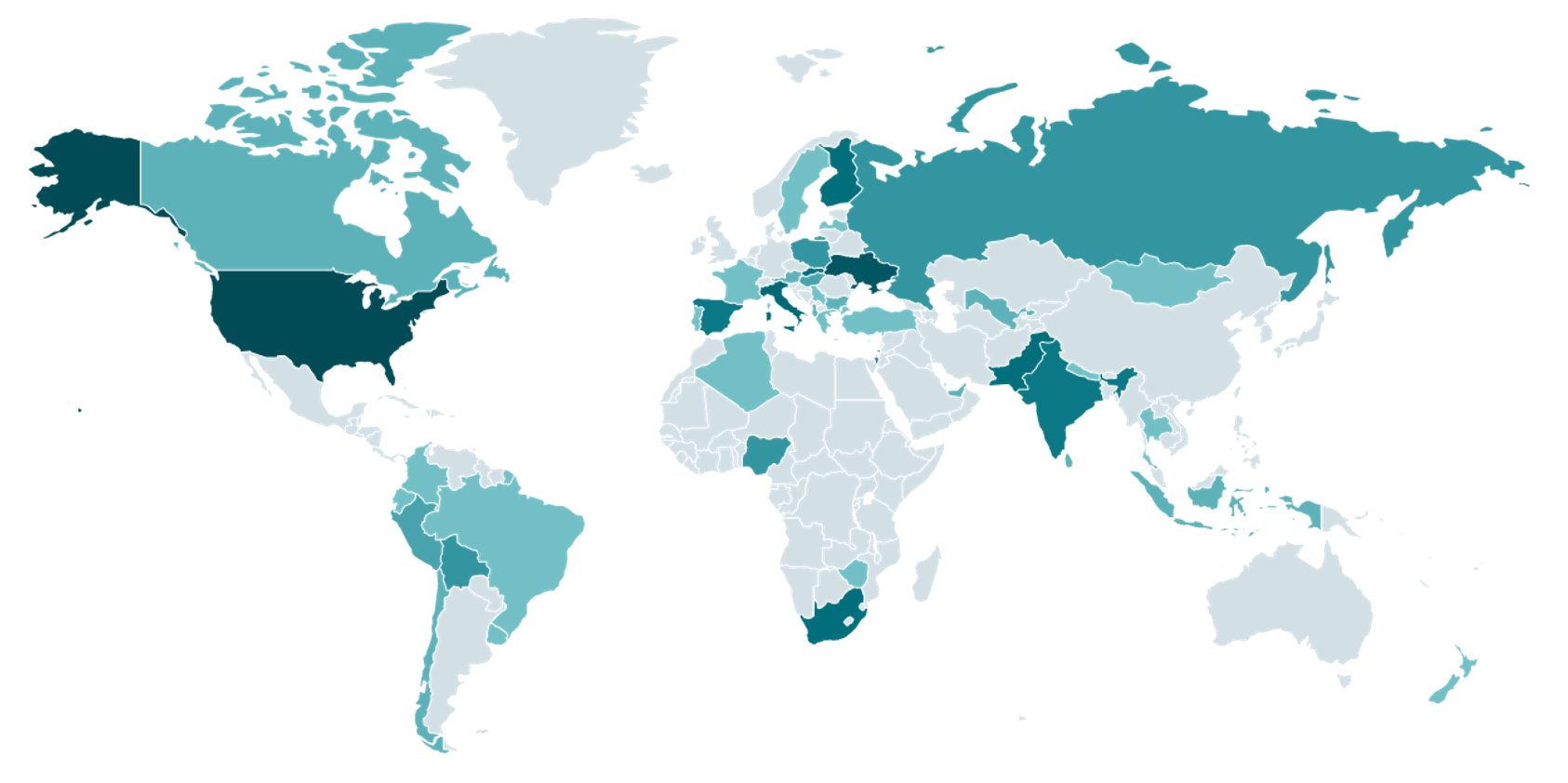
Summary: Cybersecurity researchers have identified updates to the LightSpy implant, a modular spyware with expanded capabilities for data extraction from social media platforms like Facebook and Instagram. This updated version supports an extensive range of commands across multiple operating systems and has introduced new Windows-specific plugins for data collection and surveillance.…
Read More 






 THN Weekly Recap: From $1.5B Crypto Heist to AI Misuse & Apple’s Data Dilemma
THN Weekly Recap: From $1.5B Crypto Heist to AI Misuse & Apple’s Data Dilemma