Summary: A recent report from Unit 42 reveals a new campaign of cyberattacks linked to North Korea, targeting macOS users, particularly in the cryptocurrency sector. The malware RustDoor and Koi Stealer are designed to exfiltrate sensitive data while evading detection through macOS-specific techniques, often luring victims with fake job offers.…
Read More Tag: MACOS
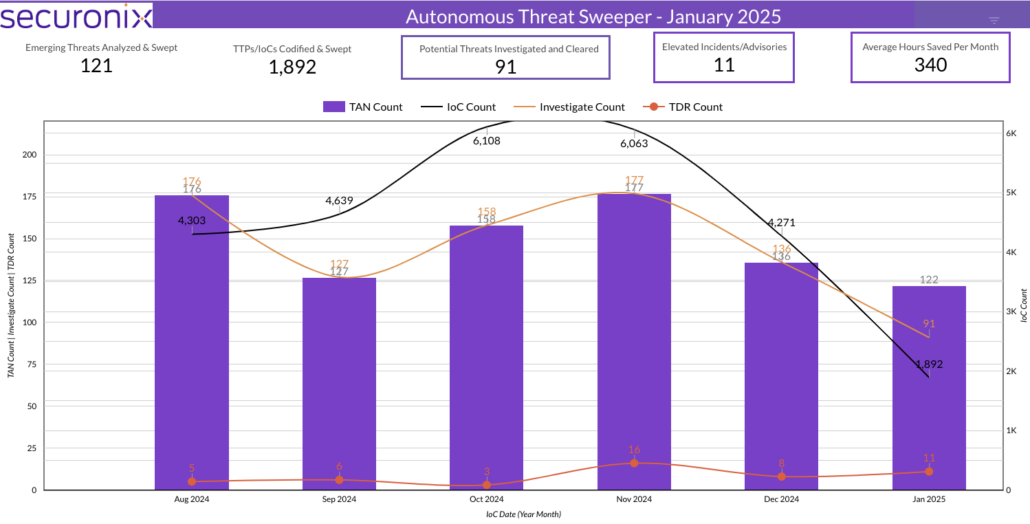
The Monthly Intelligence Insights report for November 2024 by Securonix Threat Labs highlights critical cybersecurity threats, incidents, and responses, including notable breaches involving Cyberhaven and the exploitation of Ivanti vulnerabilities. Organizations are urged to enhance their security measures, such as updating software and implementing more vigilant monitoring systems.…
Read More 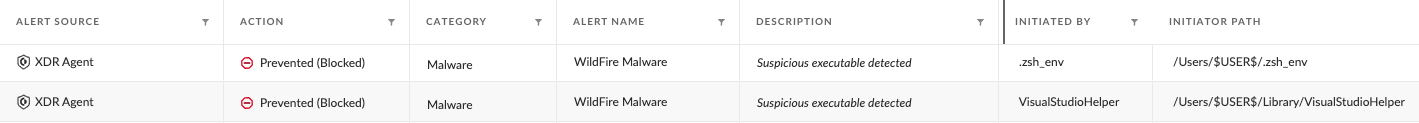
This article discusses the rise of macOS-targeting malware, particularly from North Korean APT groups, focusing on two notable malware samples: RustDoor and Koi Stealer. RustDoor disguises itself as a legitimate software update, while Koi Stealer, which is previously undocumented, primarily aims to steal sensitive data, including cryptocurrency wallet information.…
Read More 
Summary: Palo Alto Networks has reported on a new Linux malware named Auto-Color, which provides threat actors with backdoor access to compromised devices. This malware has primarily targeted universities and government entities in North America and Asia, requiring explicit execution by the victim for activation. Auto-Color employs advanced evasion techniques, making it challenging to detect and remove without specialized software.…
Read More 
This report highlights various cyber threats analyzed over a week, focusing on specific malware, threat actors, and vulnerabilities affecting various sectors. Key threats include targeted malware attacks, vulnerability exploits in popular software, and phishing campaigns. The report emphasizes ongoing cybersecurity challenges and evolving tactics among threat actors.…
Read More 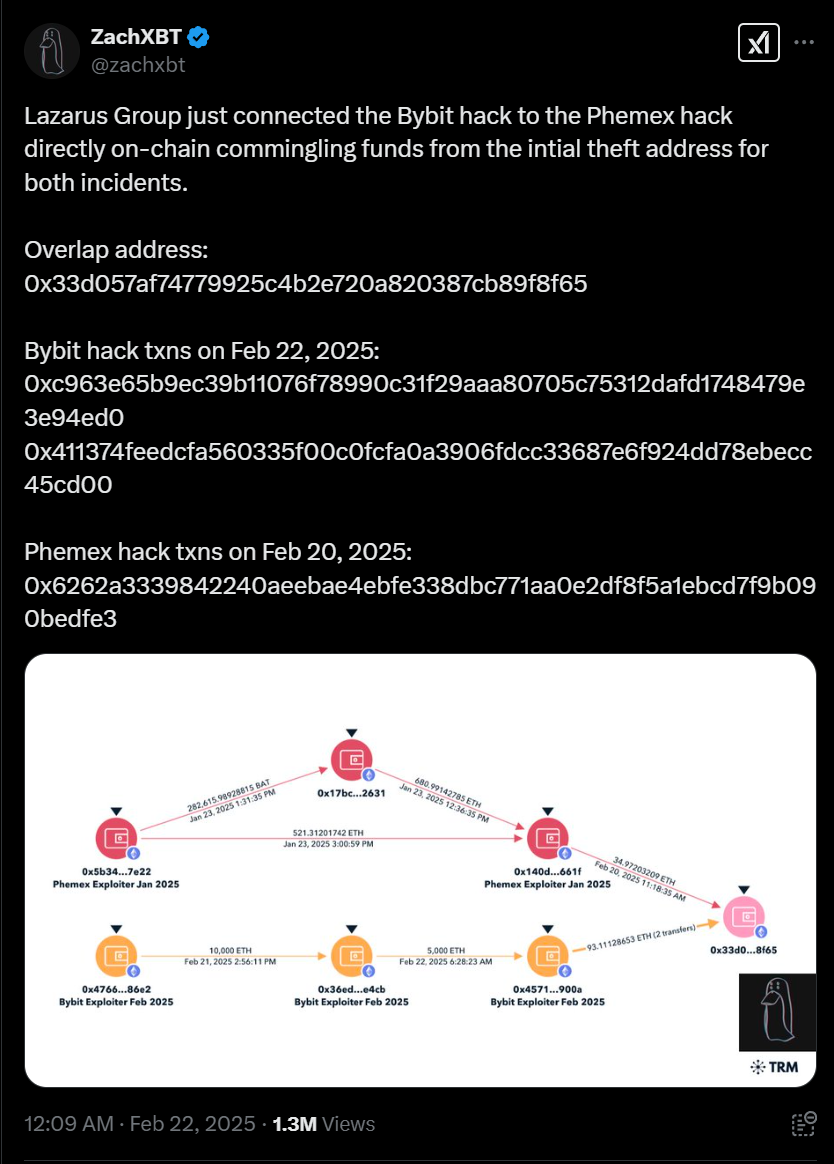
Silent Push analysts uncovered critical infrastructure used by the Lazarus APT Group, linking them to the historic .4 billion Bybit crypto heist through a recently registered domain. They identified an email connected to past attacks and noted the group’s preference for particular VPN IP addresses while exploiting fake job interviews on LinkedIn to deploy malware.…
Read More 
Summary: Cybersecurity researchers have identified updates to the LightSpy implant, a modular spyware with expanded capabilities for data extraction from social media platforms like Facebook and Instagram. This updated version supports an extensive range of commands across multiple operating systems and has introduced new Windows-specific plugins for data collection and surveillance.…
Read More 
A critical remote code execution (RCE) vulnerability (CVE-2025-27364) in MITRE Caldera poses significant risks of system compromise, potentially allowing unauthenticated attackers full control over affected systems. This vulnerability can be combined with another flaw in Parallels Desktop (CVE-2024-34331) to elevate the risks further. Security teams are urged to prioritize immediate threat detection and mitigation strategies in light of the increased prevalence of weaponized vulnerabilities.…
Read More 
The recent analysis by Forrester on the MITRE ATT&CK Evaluations highlights the advancements made in product performance evaluation against real adversary behavior and notes challenges like high alert volumes and lack of alert correlation. The Need for customized evaluation approaches emphasizes the importance of understanding specific user environments to make informed security decisions.…
Read More 
Summary: OpenAI has blocked several North Korean hacking groups from utilizing its ChatGPT platform for cyber espionage and attacks. The banned activities included researching vulnerabilities, coding assistance for cyber tools, and developing phishing strategies to target cryptocurrency investors. Additional efforts were identified, including a scheme to employ North Korean workers to exploit ChatGPT for corporate tasks under false pretenses.…
Read More 
Summary: A security vulnerability in Parallels Desktop allows attackers to gain root access on Mac devices due to a failure in code signature verification. Security researcher Mickey Jin publicly disclosed two exploits following the vendor’s inability to address the flaw for over seven months. Users are urged to take proactive measures as the vulnerability remains unpatched across all known versions of the software.…
Read More 
Summary: NinjaOne, an automated endpoint management startup based in Texas, has raised 0 million in Series C extensions, valuing the company at billion. The funding, from ICONIQ Growth and CapitalG, will support the company’s research and development and facilitate its acquisition of Dropsuite for 2 million.…
Read More
Summary: Libxml2, a widely used XML parsing library, has multiple vulnerabilities (CVE-2024-56171, CVE-2025-24928, CVE-2025-27113) that could lead to denial of service and arbitrary code execution. These vulnerabilities have been addressed in recent releases (2.12.10 and 2.13.6), and users are advised to update immediately. Failure to update may leave systems exposed to significant security risks.…
Read More 
Summary: A newly disclosed 0-day vulnerability in Parallels Desktop allows for root privilege escalation, bypassing a previous patch. The flaw emanates from the repack_osx_install_app.sh script and has been unaddressed by Parallels for over seven months despite multiple responsible disclosure attempts. Independent researcher Mickey Jin has shared proof-of-concept exploits demonstrating how attackers could gain root access.…
Read More 
Summary: This week’s cyber news highlights a record-breaking .5 billion crypto theft linked to the Lazarus Group, the banning of ChatGPT accounts for malicious activities by OpenAI, and Apple’s withdrawal of its Advanced Data Protection feature in the UK. These incidents underscore the evolving landscape of cyber threats and their impact on organizations and users alike.…
Read More
Summary: A recent investigation has uncovered a cyber-espionage campaign linked to North Korean actors, utilizing malware disguised as job interview applications to harvest sensitive data from macOS users. The malware, identified as ‘DriverEasy’ and ‘ChromeUpdate’, employs social engineering tactics to deceive victims into providing their credentials.…
Read More
This article discusses vulnerabilities in macOS’s storagekitd daemon that allowed privilege escalation to root and bypassing of Transparency, Consent, and Control (TCC) protections. Despite Apple’s attempts to patch these vulnerabilities with CVE-2024-27848 and CVE-2024-44210, the issues showcased the complexity and risks associated with system daemons in macOS.…
Read More 
This week’s cybersecurity updates reveal critical vulnerabilities in several platforms like OpenSSH, Atlassian products, and Palo Alto Networks firewalls. There are also reports of new phishing techniques, malware campaigns targeting sensitive data, and alarming data breaches affecting healthcare organizations. Affected: OpenSSH, Atlassian (Confluence, Bamboo, Bitbucket, Jira, Crowd), Palo Alto Networks, Signal Messenger, Australian Infrastructure, HCRG Care Group, DM Clinical Research
Read More Keypoints :
Two critical vulnerabilities in OpenSSH could lead to man-in-the-middle and denial-of-service attacks.…
Summary: A report by ESET reveals that freelance software developers, particularly in the cryptocurrency sector, have been targeted by North Korean hackers through a campaign known as DeceptiveDevelopment. The attackers employed fake job offers to distribute malware that enables them to exfiltrate sensitive data, including cryptocurrency information.…
Read More
Summary: Cybercriminals TA2726 and TA2727 have been identified exploiting fake browser update scams to distribute malware across various platforms, notably introducing the FrigidStealer information-stealing malware targeting MacOS. The landscape of these scams has seen an increase in copycat threat actors, complicating the tracking for cybersecurity analysts.…
Read More  THN Weekly Recap: From $1.5B Crypto Heist to AI Misuse & Apple’s Data Dilemma
THN Weekly Recap: From $1.5B Crypto Heist to AI Misuse & Apple’s Data Dilemma