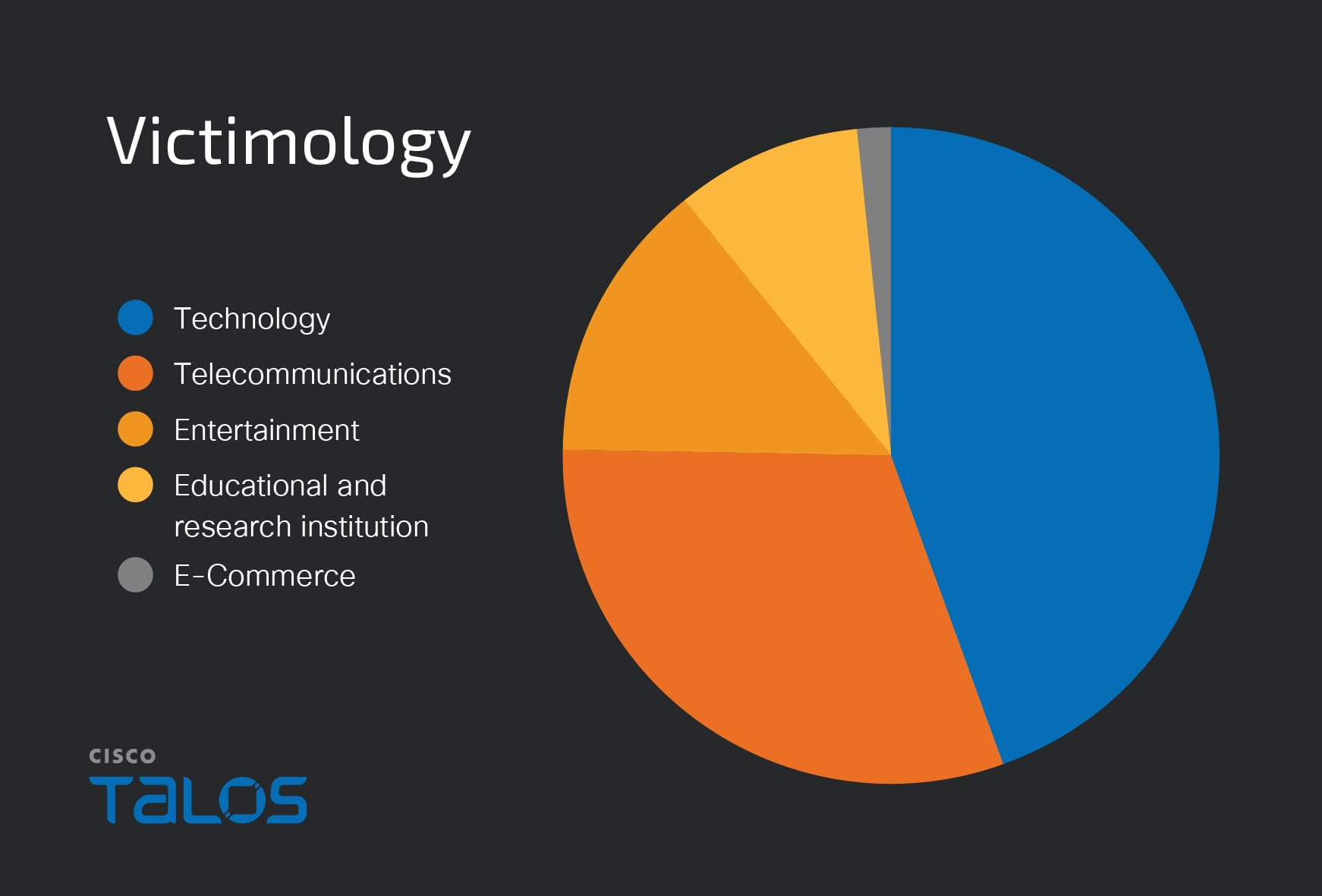
Summary: Apple has released iOS 18.3.2 and iPadOS 18.3.2 to address a serious WebKit vulnerability, CVE-2025-24201, which has reportedly been exploited in advanced attacks against targeted individuals. This fix is crucial as it protects users from a vulnerability that allows attackers to escape the Web Content sandbox, potentially leading to unauthorized actions.…
Read More