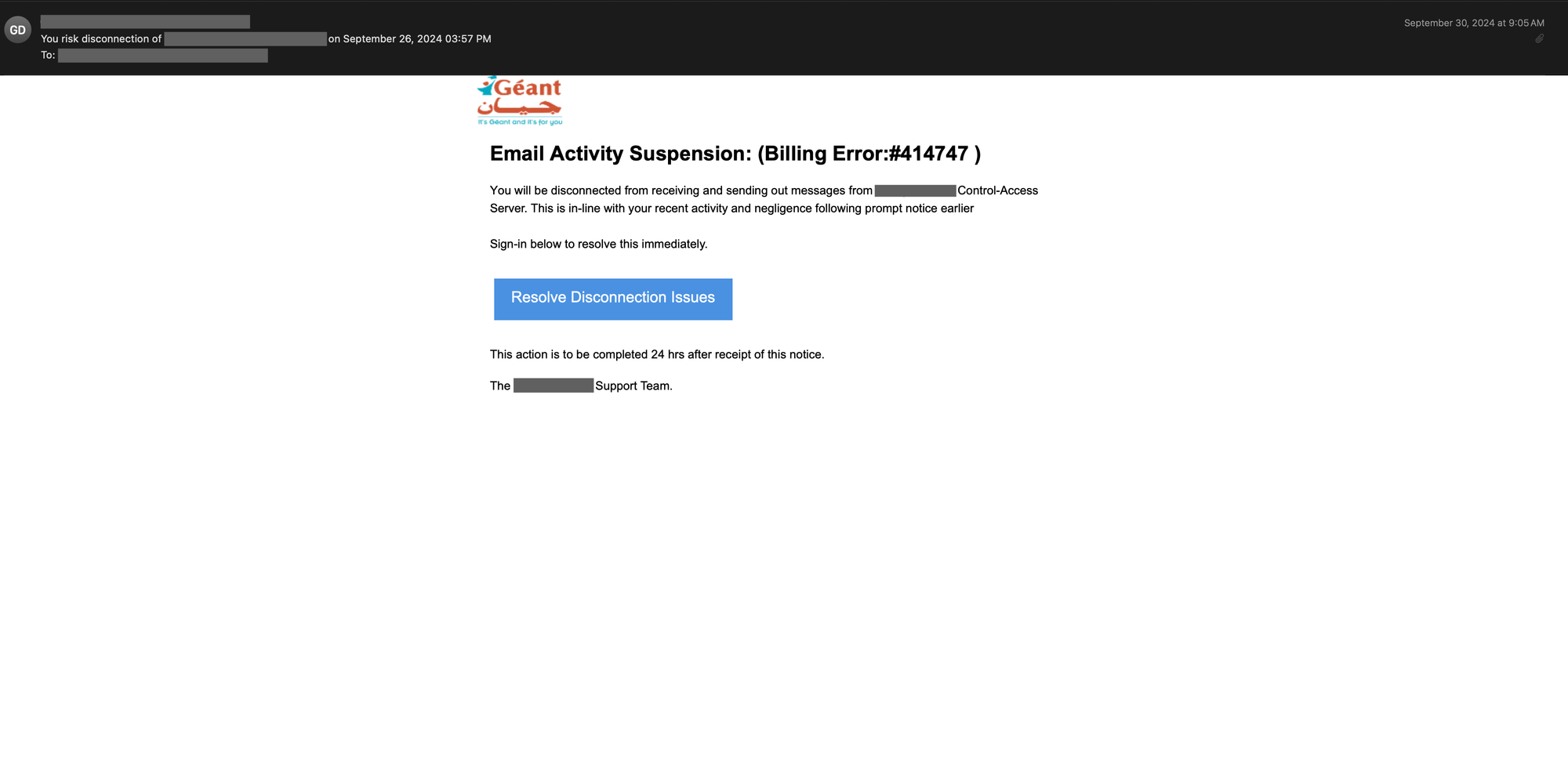
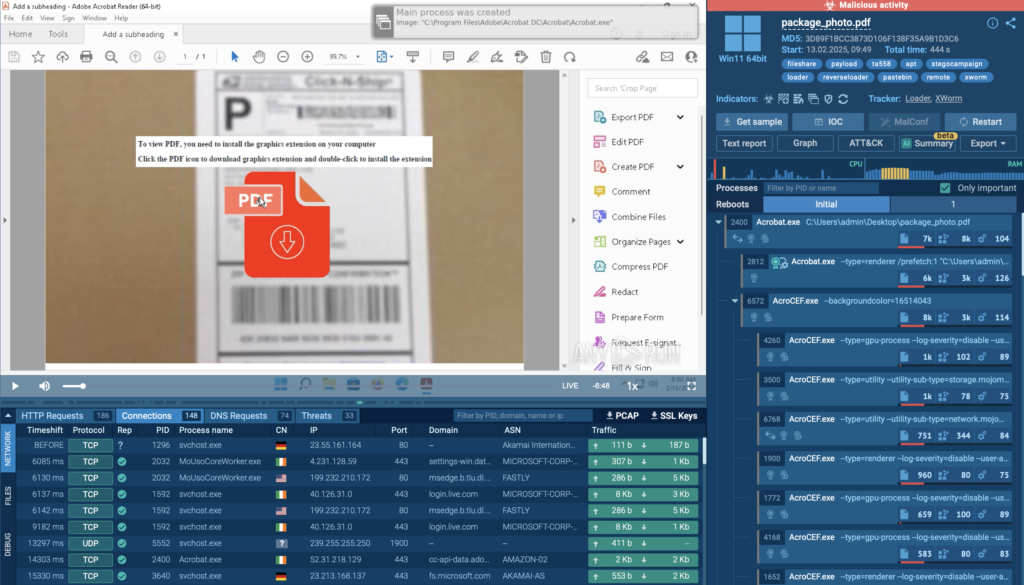
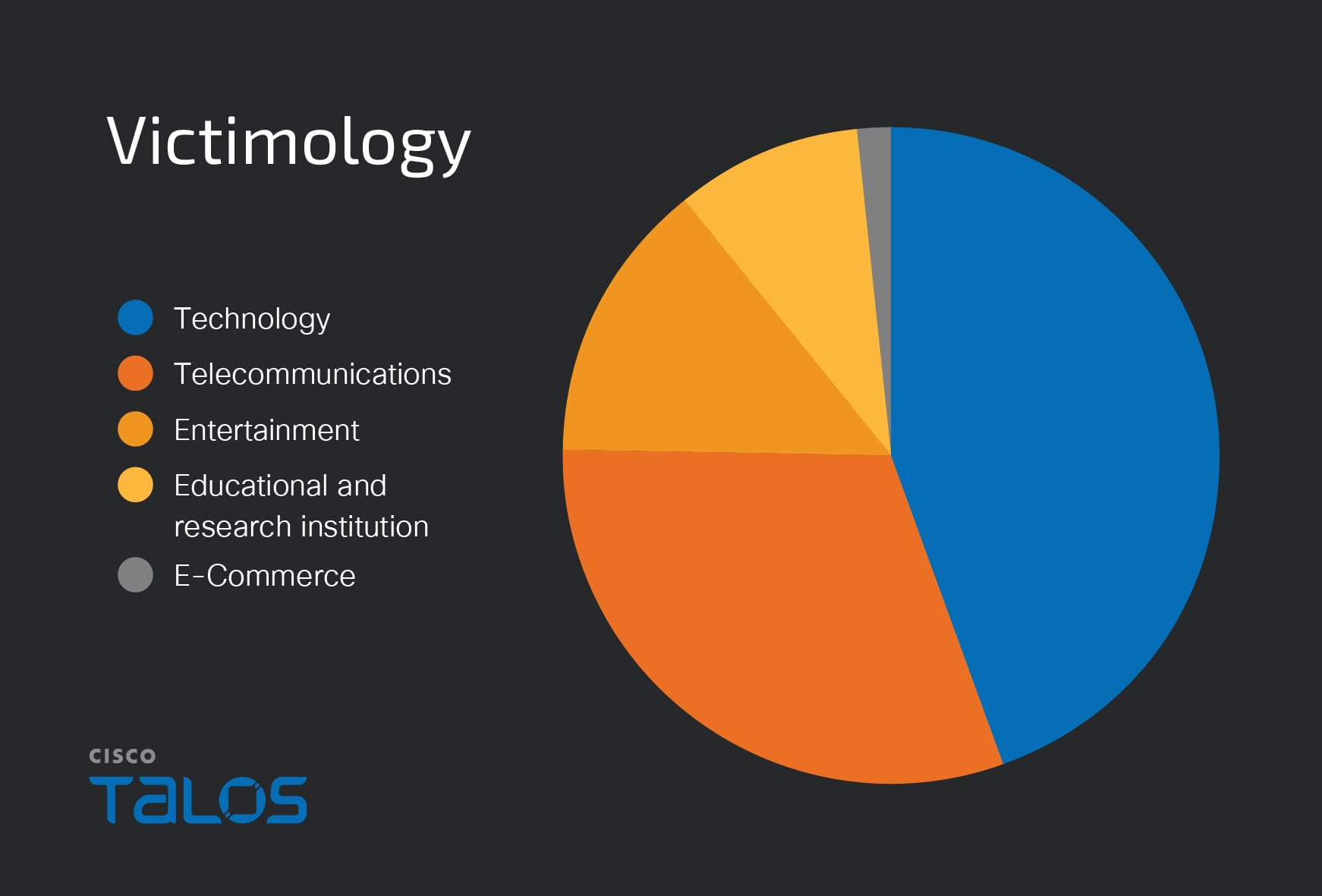
Summary: Since August 2024, state-sponsored hackers and cybercriminals have been using a technique called ClickFix to deploy information stealer malware. This method involves social engineering through malicious JavaScript that manipulates users into executing harmful commands. Group-IB reports an increase in this attack vector, particularly targeting users on various platforms that offer free content or software.…
Read More