This article provides an analysis of the malware sample 875b0cbad25e04a255b13f86ba361b58453b6f3c5cc11aca2db573c656e64e24.exe, attributed to the Lazarus Group, a state-sponsored cyber threat actor. Using tools like ANY.RUN and Hybrid Analysis, the analysis reveals the malware’s behavior, including process injection and registry modifications, targeting primarily Windows systems and expanding to Linux and macOS environments.…
Read More 
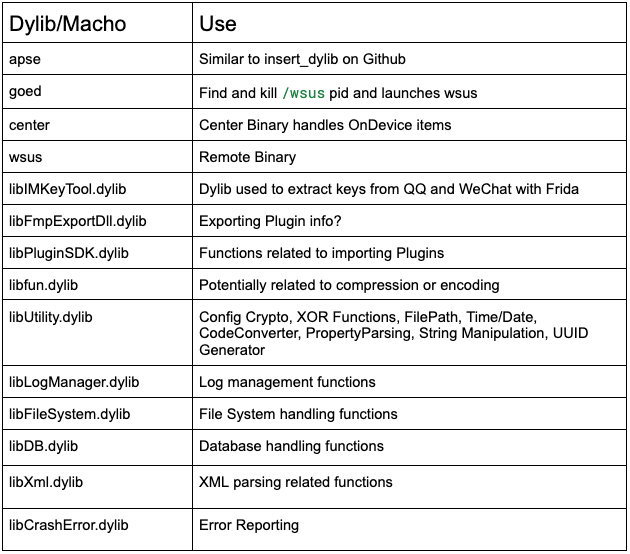

.png)
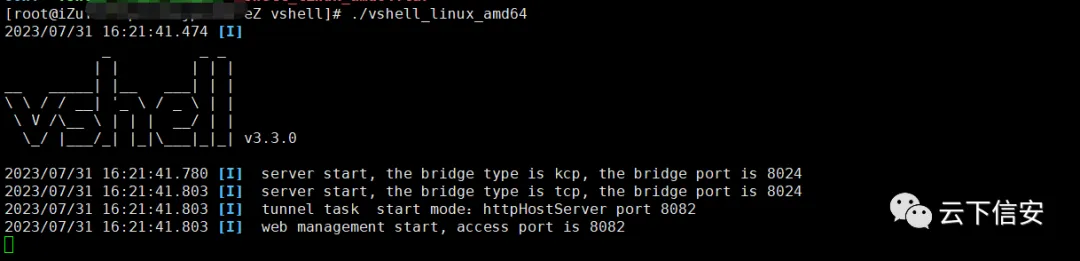



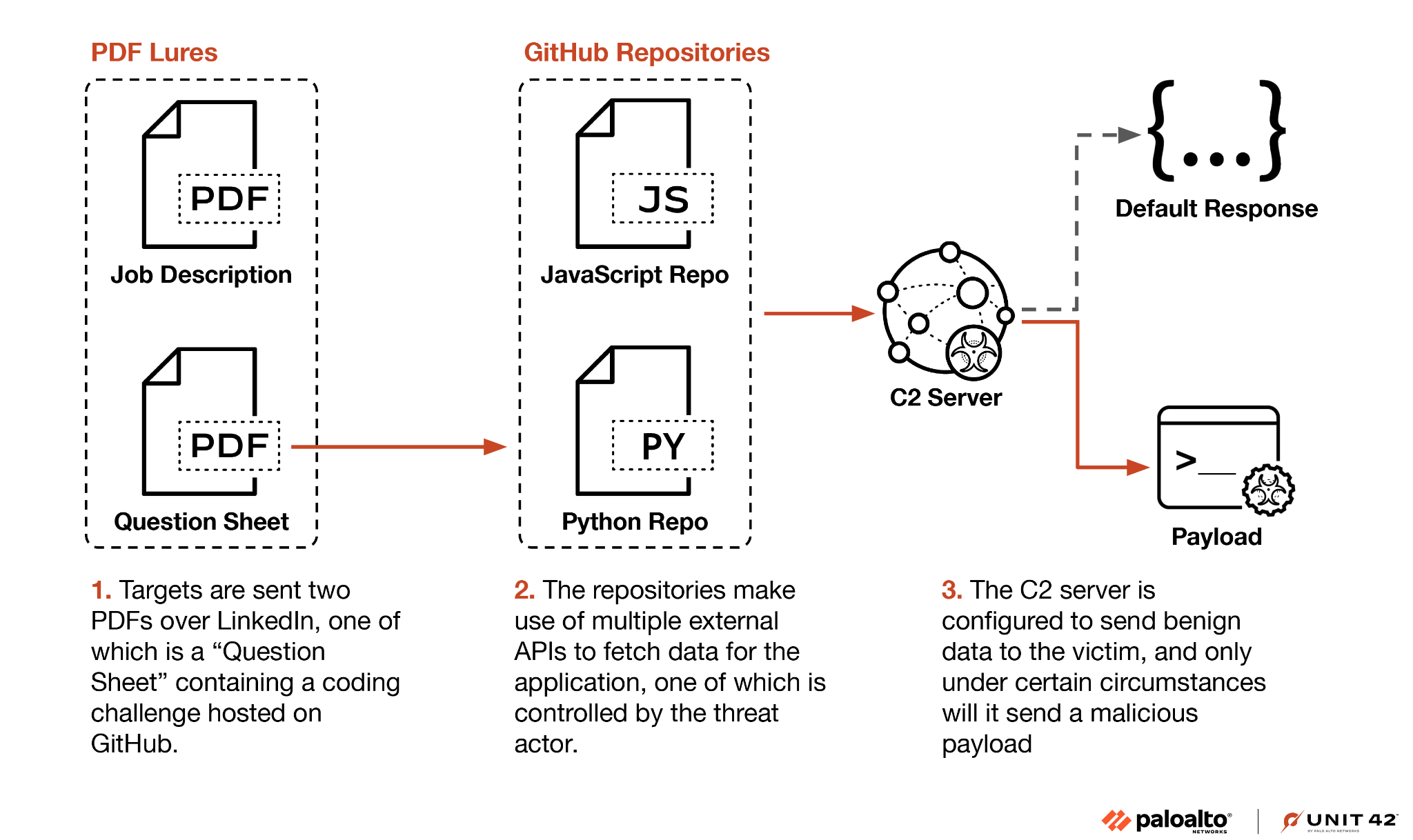

 Cybersecurity And Much More – Vol. 5 2
Cybersecurity And Much More – Vol. 5 2