Summary: The video discusses the installation and setup of Windows Subsystem for Linux (WSL), specifically focusing on using Ubuntu and Kali Linux distributions. It covers prerequisites, command-line installation, and running graphical applications within these environments, demonstrating how to utilize tools like hashcat for tasks like GPU-based Wi-Fi hash cracking.…
Read More Tag: LINUX
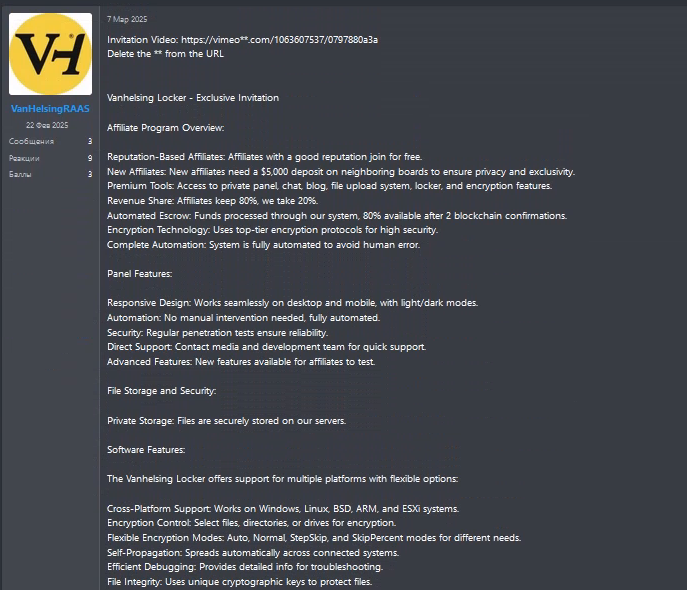
VanHelsingRaaS is an emerging ransomware-as-a-service (RaaS) launched in March 2025, allowing affiliates to initiate ransomware attacks with a low deposit. It targets multiple platforms and has already infected several victims demanding significant ransom payments. The program’s rapid growth and sophisticated capabilities highlight the evolving ransomware threat.…
Read More
This article provides a comprehensive guide on hacking and securing Wi-Fi networks using Aircrack-ng, detailing practical attack techniques and encryption vulnerabilities, as well as prevention strategies. The focus is on educating users about Wi-Fi security to help them protect their networks from potential attacks. Affected: Wi-Fi networks, cybersecurity sector
Read More Keypoints :
Wi-Fi security is critical for protecting against cyber threats.…
Summary: Esri has identified a critical vulnerability in its ArcGIS Enterprise platform that could enable attackers to hijack administrative accounts via a password reset flaw. The vulnerability, CVE-2025-2538, has a CVSS score of 9.8 and affects specific versions of Portal for ArcGIS. Organizations are urged to apply the security patch released by Esri to prevent potential data breaches and service disruptions.…
Read More 
Summary: New variants of the Albabat ransomware have been developed to target multiple operating systems, including Windows, Linux, and macOS. Researchers from Trend Micro have found that version 2.0 incorporates a GitHub account to enhance operational efficiency and track infections, with evidence suggesting a subsequent version, 2.5, is also under development.…
Read More Summary: The video discusses how to run Linux distributions, specifically Kali Linux and Ubuntu, on a Windows laptop using the Windows Subsystem for Linux (WSL). It demonstrates the capabilities this integration provides, such as running GUI applications, performing web security tests with Burp Suite, and utilizing Hashcat for password cracking while accessing GPU resources.…
Read More 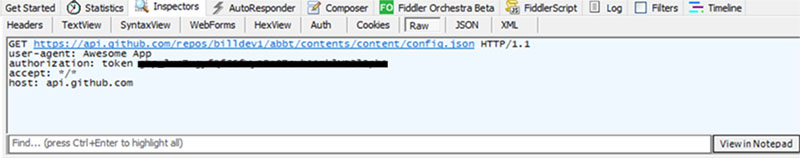
Trend Research has identified new versions of the Albabat ransomware targeting Windows, Linux, and macOS platforms. The group is utilizing GitHub to facilitate their ransomware operations. Organizations are advised to enhance security protocols and implement preventive measures to mitigate potential ransomware attacks. Affected: Windows, Linux, macOS
Read More Keypoints :
New versions of Albabat ransomware have been discovered, indicating a potential expansion of targets.…Summary: The video discusses this week’s security news, covering a variety of topics including compliance localization, a notorious cybersecurity myth, and several notable security incidents and vulnerabilities. Highlights include Microsoft trolling, a GitHub supply chain attack, the significance of proper firmware updates, and recommendations for Linux systems and tools.…
Read More 
Log4Shell is a serious Remote Code Execution vulnerability in the Apache Log4j framework that allows attackers to execute arbitrary code via malicious JNDI lookup strings. Discovered in 2021, the flaw affects versions 2.0-beta9 to 2.14.1 of Log4j, impacting countless Java applications that use this logging tool.…
Read More 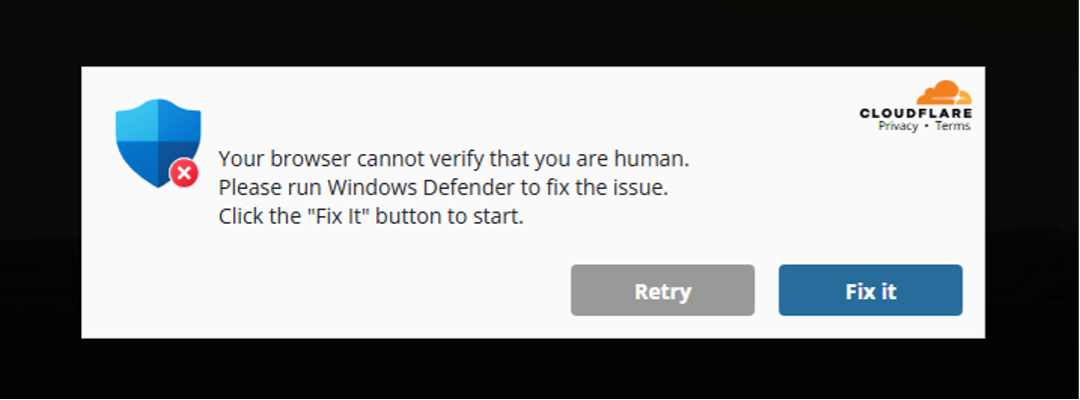
This article describes an ongoing malware campaign utilizing malicious WordPress plugins to spread the LummaStealer trojan. The malware trick users into running harmful PowerShell commands, thus collecting sensitive data from infected PCs. The campaign exploits fake human verification prompts primarily targeting Windows users. Affected: WordPress websites, Windows operating system users
Read More Keypoints :
LummaStealer is an infostealer malware designed to collect sensitive data.…
Summary: Kali Linux has launched version 2025.1a, introducing a new tool, desktop updates, and a refreshed theme. This version emphasizes visual upgrades, including new wallpapers and improvements to the user interface. Additionally, the release includes updates to the Kernel and introduces new keyboard shortcuts for enhanced navigation.…
Read More Summary: The video discusses the usage of the tail command in Linux to view the last few lines of a file, demonstrating how to customize the number of lines displayed while reading output from manual (man) pages or text files.
Read More Keypoints:
The tail command in Linux is used to display the last part of files.…
This article recounts an individual’s challenging experience with the Paller Cybersecurity Scholarship application process, highlighting communication breakdowns, delays in credential validation by partner organizations, and unexpected financial burdens. Despite the scholarship’s promise of substantial professional development in cybersecurity, the author expresses frustration over a lack of accountability and support from SANS Institute, ultimately resulting in an unsuccessful application.…
Read More Summary: The video discusses the Linux `head` command, which is used to display the first few lines of a specified file. It explains how to customize the number of lines shown and emphasizes the importance of using manual pages for further information about command options.
Read More Keypoints:
The `head` command displays the first 10 lines of a file by default.…Summary: The video discusses the misconceptions surrounding mainframes, highlighting their evolution into modern, powerful, and sustainable platforms. It emphasizes their capabilities, including running multiple Linux systems on a single chip and their compatibility with contemporary tools, all while being cost-effective and energy-efficient.
Read More Keypoints:
Mainframes are not old or outdated; they have evolved into modern platforms.…Summary: The video discusses the command and control infrastructure dubbed “Convo C2,” which enables red teamers to execute system commands on compromised hosts via Microsoft Teams. Released in November 2024, this tool cleverly hides data within HTML tags and utilizes Microsoft servers for communication, making detection by security solutions challenging.…
Read More 
Ghost in the Router: China-Nexus Espionage Actor UNC3886 Targets Juniper Routers | Google Cloud Blog
Mandiant’s discovery in mid-2024 revealed that the China-nexus espionage group, UNC3886, deployed custom backdoors on Juniper Networks’ Junos OS routers, utilizing various capabilities to maintain long-term access while circumventing security protections. Mandiant urges organizations to upgrade their Juniper devices to mitigate these vulnerabilities and recommends security measures.…
Read More 
A new variant of XCSSET malware has been discovered, which is specifically designed to infect macOS Xcode projects. This sophisticated malware utilizes advanced obfuscation, updated persistence techniques, and novel infection strategies to exfiltrate sensitive information, including digital wallet data. It operates in a stealthy manner, often remaining fileless, which complicates detection and removal efforts.…
Read More
Summary: A security researcher, Yohanes Nugroho, has developed a brute-force decryptor for Akira ransomware victims that allows recovery of encrypted data without paying a ransom. The decryptor leverages Nvidia GPUs and overcomes complex encryption methods used by the ransomware, providing hope for over 250 victims impacted by the attacks.…
Read More 
Summary: This week’s cybersecurity report highlights the evolving landscape of cyber threats, including advanced techniques used by threat groups and rising supply chain vulnerabilities. Law enforcement efforts against cybercriminal networks show promise, while new exploits and vulnerabilities demand prompt attention from organizations. The report includes notable incidents, emerging attack methods, and critical vulnerabilities that security teams should prioritize.…
Read More  THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More