Threat Actor: PRC nation state or commercial/ransomware threat group | PRC nation state Victim: Illumina | Illumina
Key Point :
Vulnerabilities allow attackers to overwrite firmware, potentially disabling the device or enabling persistent access.…
Threat Actor: PRC nation state or commercial/ransomware threat group | PRC nation state Victim: Illumina | Illumina
Key Point :
Vulnerabilities allow attackers to overwrite firmware, potentially disabling the device or enabling persistent access.…
Threat Actor: Cyber attackers | cyber attackers Victim: American consumers | American consumers
Key Point :
The Cyber Trust Mark program allows manufacturers to undergo cybersecurity audits for their smart products.…
Threat Actor: National Cyber Director | National Cyber Director Victim: Federal Agencies | federal agencies
Key Point :
The ONCD and OMB published cybersecurity benchmarks for fiscal 2026 budgets.…Key Points :
No evidence of a data breach has been found at Go Sport in France. The investigation indicates that customer data remains secure. Go Sport continues to monitor its systems for any potential threats.…Key Points :
Customer data from Habib’s Fast-Food Chain has been leaked. The breach may include sensitive information such as names, addresses, and payment details. The threat actor remains unidentified, raising concerns about the security of similar businesses.…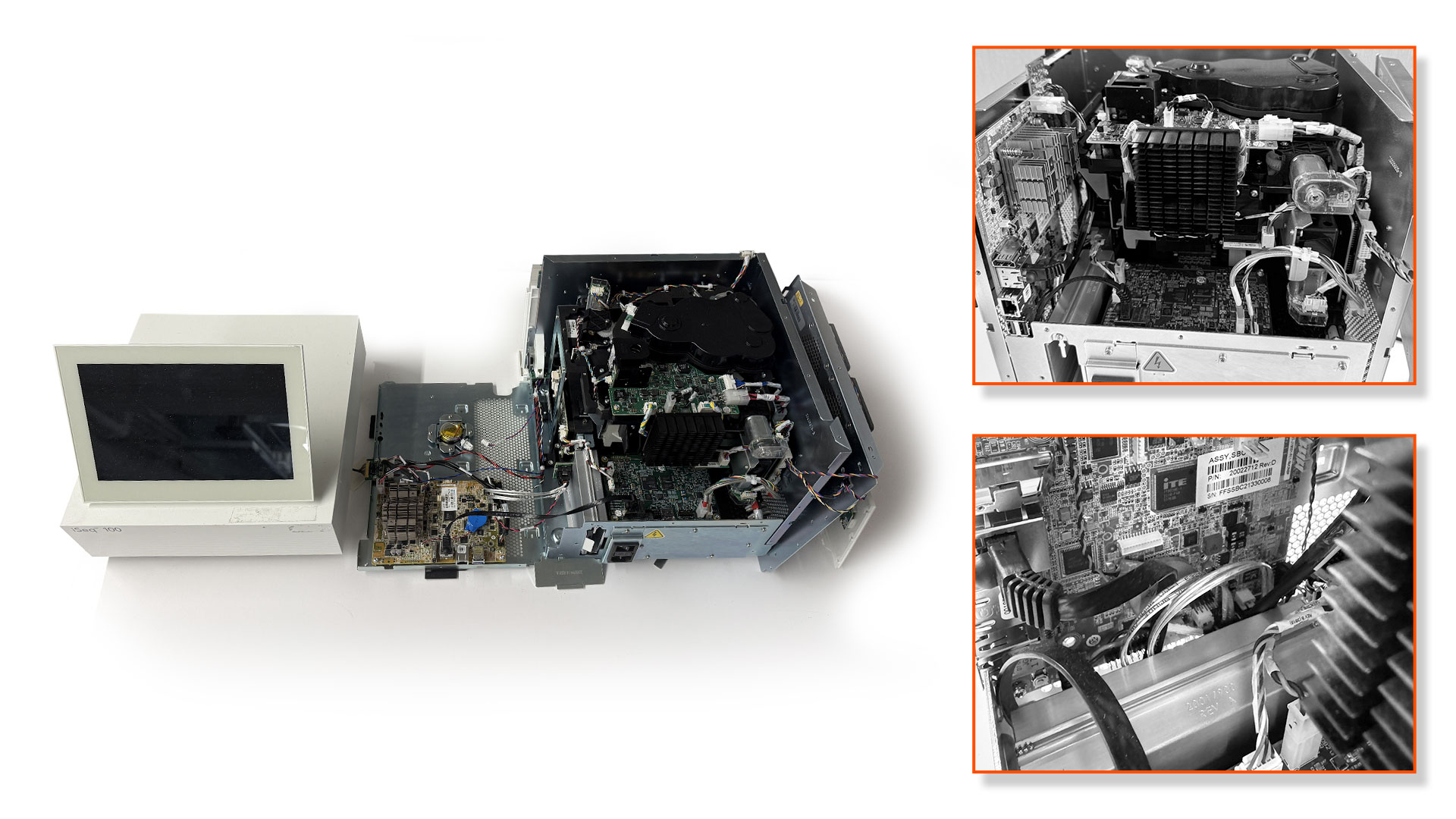
Keypoints :
Illumina iSeq 100 uses outdated BIOS firmware without Secure Boot or write protections.…


Threat Actor: Natohub | Natohub Victim: International Civil Aviation Organization (ICAO) | International Civil Aviation Organization
Key Point :
ICAO is investigating claims of a breach involving personal data of 42,000 individuals.…
Threat Actor: Cybercriminals | cybercriminals Victim: Organizations | organizations
Key Point :
Legacy Multi-Factor Authentication (MFA) became obsolete due to vulnerabilities to modern attack techniques like phishing and SIM swapping.…Keypoints :
The script is a Python-based malware targeting Microsoft Windows.…Keypoints :
Cyberhaven’s breach was due to the compromise of a Chrome Web Store administrative account.…
Threat Actor: Chinese state-backed hackers | Chinese state-backed hackers Victim: U.S.…
The video discusses the significance of bug bounty programs in enhancing cybersecurity practices at Amazon. It emphasizes the importance of ethical and responsible research and how various researchers contribute to continuous learning and improvement within the company. The speaker highlights the collaboration with HackerOne and their commitment to fostering relationships with the security research community.…
Threat Actor: Unknown | unknown Victim: South Portland Public Schools, Rutherford County Schools | South Portland Public Schools, Rutherford County Schools
Key Point :
South Portland Public Schools experienced a cyberattack that compromised their firewall, but no student data was believed to be stolen.…Threat Actor: Russia’s internet regulator | Russia’s internet regulator Victim: Russian online users | Russian online users
Key Point :
Outage affected access to major platforms like Google, Yandex, and VKontakte.…Threat Actor: Tesla | Tesla Victim: Matthew Livelsberger | Matthew Livelsberger
Key Point :
Tesla’s data collection proved crucial for law enforcement in tracking the driver’s movements after a Cybertruck explosion.…