Threat Actor: Silent Crow | Silent Crow Victim: Rosreestr | Rosreestr
Key Point :
Silent Crow publicly released a portion of a database containing personal information of Russian citizens.…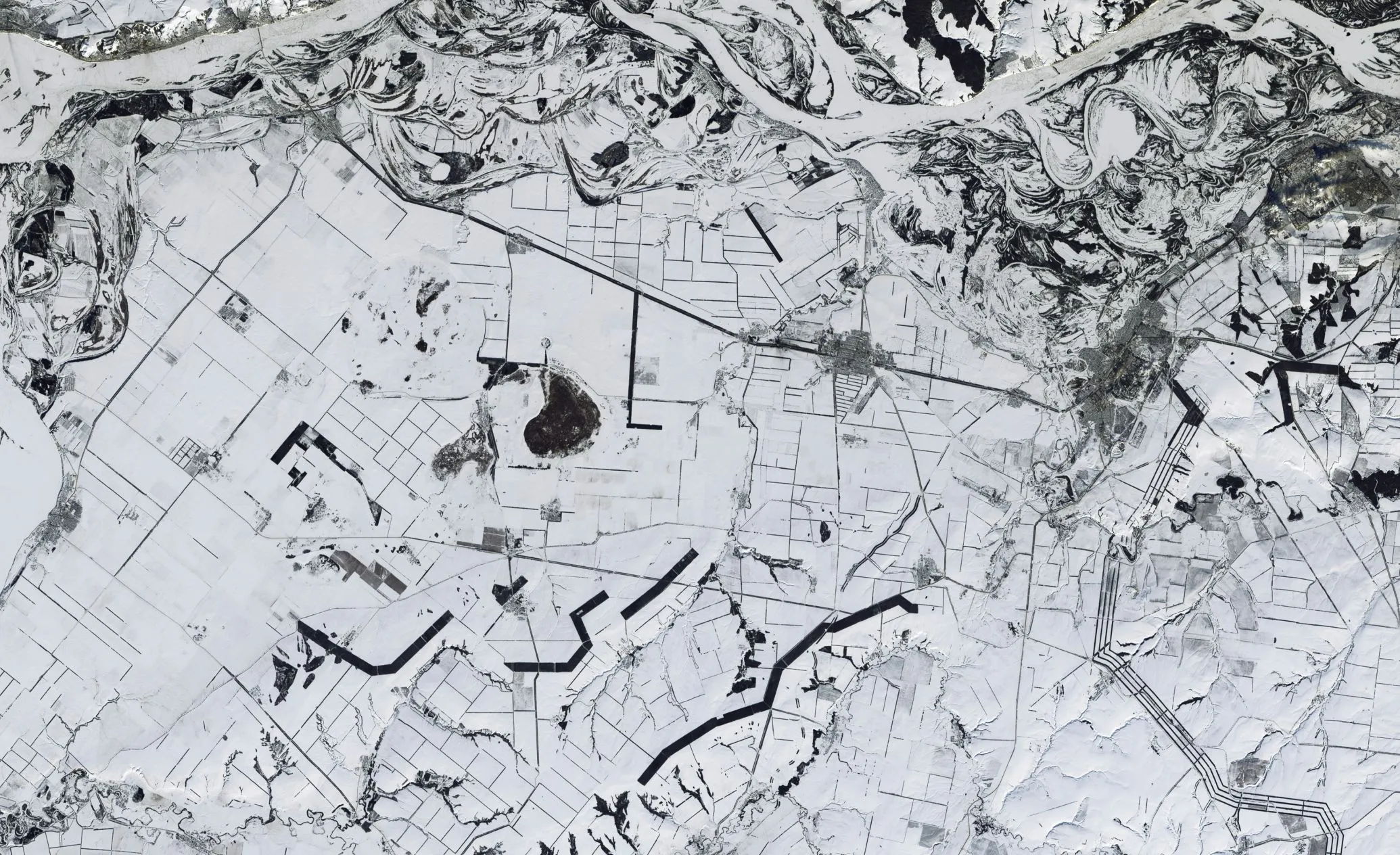
Threat Actor: Silent Crow | Silent Crow Victim: Rosreestr | Rosreestr
Key Point :
Silent Crow publicly released a portion of a database containing personal information of Russian citizens.…

Threat Actor: Unknown | unknown Victim: Winston-Salem, NC | Winston-Salem, NC
Key Point :
City officials confirmed the cyberattack on December 30, following issues discovered one day after Christmas.…
Threat Actor: Shadow AI Users | shadow AI users Victim: Organizations | organizations
Key Point :
Shadow AI refers to unauthorized use of AI tools within organizations, increasing data security risks.…
Threat Actor: Cybercriminals | cybercriminals Victim: Organizations | organizations
Key Point :
10.3% increase in encrypted attacks over the past year.…The curated list of free cybersecurity courses includes essential topics such as ‘Introduction to Cybersecurity,’ which lays the groundwork for understanding digital security threats. For those looking to deepen their knowledge, ‘Cybersecurity Essentials’ and ‘Networking Essentials’ provide critical insights into protective measures and network configurations. Advanced courses like ‘Ethical Hacking Essentials’ and ‘Digital Forensics Essentials’ equip learners with practical skills to combat cyber threats and investigate incidents.…

Threat Actor: Malicious Actors | malicious actors Victim: Enterprises | enterprises
Key Point :
Collaboration combines Trend Micro’s AI-powered security with Intel’s Threat Detection Technology for enhanced protection.…

Threat Actor: U.S.…

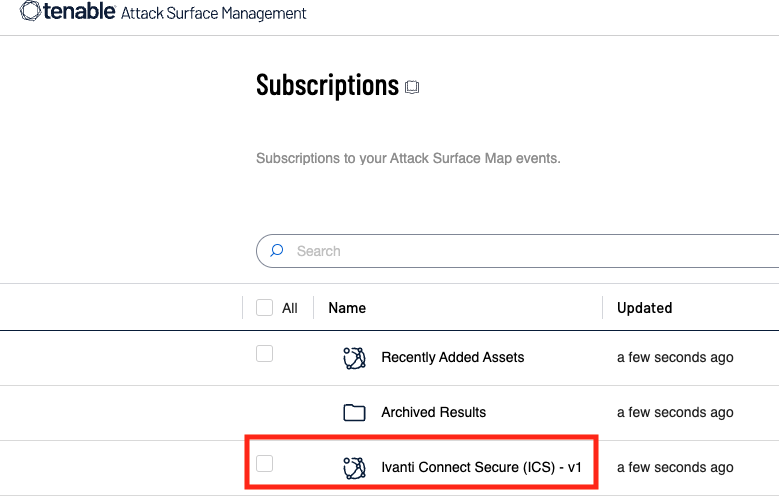
Threat Actor: Unknown | unknown Victim: Ivanti customers | Ivanti customers
Key Point :
Two vulnerabilities, CVE-2025-0282 and CVE-2025-0283, have been identified in Ivanti’s products.…
Threat Actor: Unknown | unknown Victim: Green Bay Packers | Green Bay Packers
Key Point :
Malicious code allowed unauthorized access to customer payment information during checkout.…
Threat Actor: U.S. Military | U.S. Military Victim: National Defense | National Defense
Key Point :
Rep.…
Threat Actor: Unknown | unknown Victim: PowerSchool | PowerSchool
Key Point :
PowerSchool experienced unauthorized access to its customer portal, PowerSource, on December 28.…
Threat Actor: European Commission | European Commission Victim: German citizen | German citizen
Key Point :
The court fined the European Commission €400 for violating GDPR.…
Threat Actor: Ukrainian Cyber Alliance | Ukrainian Cyber Alliance Victim: Nodex | Nodex
Key Point :
Nodex’s network was reportedly “destroyed” in a planned cyberattack.…
Threat Actor: Natohub | Natohub Victim: International Civil Aviation Organization | International Civil Aviation Organization
Key Point :
ICAO confirmed the breach involved approximately 42,000 recruitment application data records from April 2016 to July 2024.…

Keypoints:
Backstage offers a catalog that consolidates all resources in a repository.…