Keypoints :
Critical vulnerability allows full remote control of CentOS systems.…

Keypoints :
Critical vulnerability allows full remote control of CentOS systems.…


Threat Actor: GRU | GRU Victim: Poland | Poland
Key Point :
Russia is actively attempting to influence Polish politics and elections, marking a significant escalation in foreign interference.…

Threat Actor: Unspecified | threat actor Victim: GiveWP users | GiveWP
Key Point :
Vulnerability tracked as CVE-2025-22777 allows unauthenticated PHP Object Injection.…
Keypoints :
The box “Escape” is rated Medium and is the author’s first Active Directory machine.…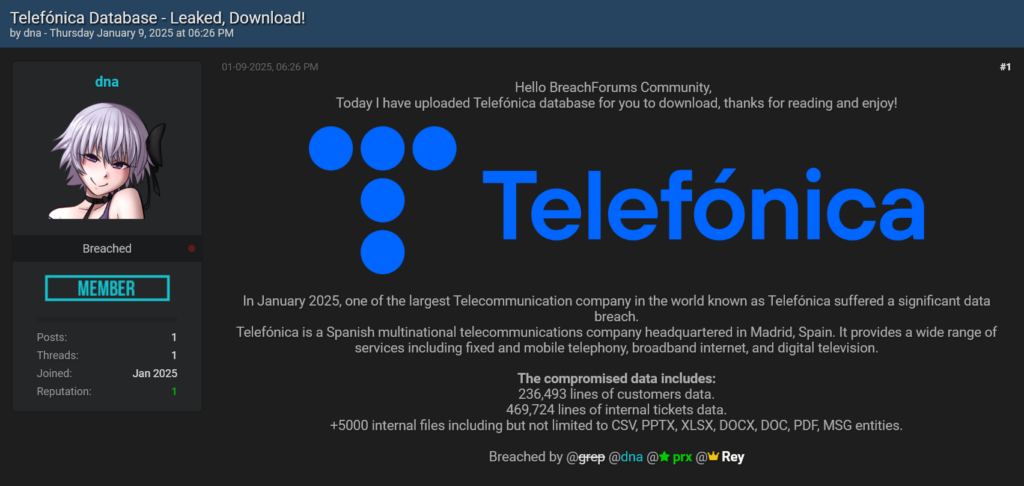



Keypoints :
IoCs are crucial for identifying traces of cyberattacks.…
Threat Actor: Everest cybercrime gang | Everest cybercrime gang Victim: STIIIZY | STIIIZY
Key Point :
Data breach exposed personal information of customers, including drivers’ license and passport numbers.…
Threat Actor: Unknown | unknown Victim: Slovakian Geodesy, Cartography and Cadastre Office (UGKK) | Slovakian Geodesy, Cartography and Cadastre Office (UGKK)
Key Point :
The attack is the largest in Slovakia’s history, with attackers demanding millions in ransom.…

Threat Actor: Pro-Russian Bot Networks | Pro-Russian Bot Networks Victim: Croatian Presidential Election | Croatian Presidential Election
Key Point :
Bot networks are promoting Zoran Milanović while undermining his opponent, Dragon Primorac.…
Threat Actor: Cybercriminals | cybercriminals Victim: Healthcare Organizations | healthcare organizations
Key Point :
Elisity’s Virtual Edge allows for microsegmentation without new hardware, using lightweight virtual connectors.…
Threat Actor: UNC5221 | UNC5221 Victim: Ivanti | Ivanti
Key Point :
Mandiant identified exploitation of CVE-2025-0282 by Chinese hackers, linked to previous attacks on Ivanti products.…
Threat Actor: N/A | Proton Victim: Proton users | Proton users
Key Point :
Outage began around 10:00 AM ET, affecting all major Proton services.…
Threat Actor: N/A | N/A Victim: iPhone owners | iPhone owners
Key Point :
Apple confirms that Siri data has never been used for marketing profiles or advertising.…