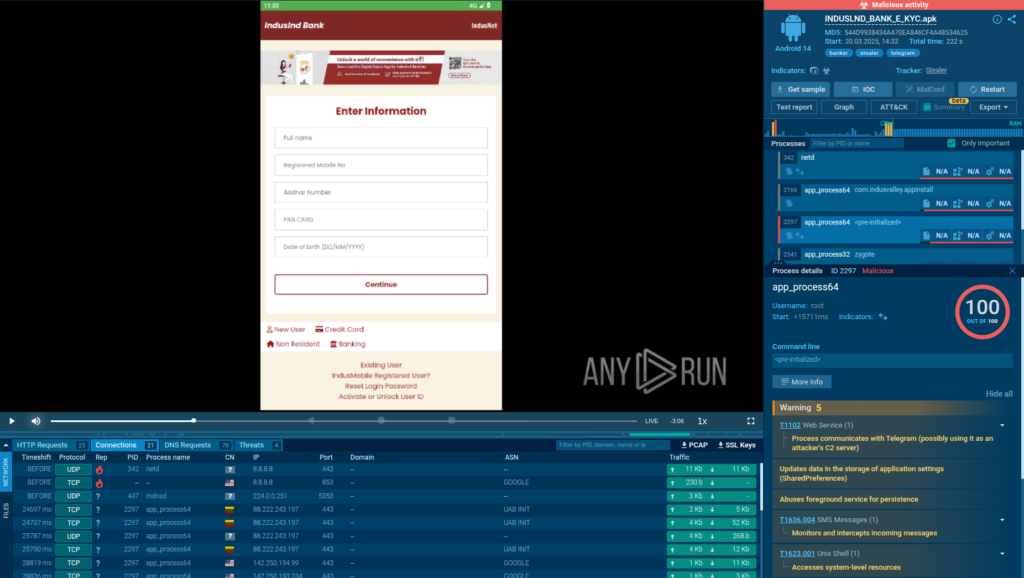
Summary: This content discusses the critical importance of properly configuring SSL certificates to mitigate cybersecurity risks, particularly focusing on the vulnerabilities presented by SSL misconfigurations. It highlights that many organizations fail to address these configurations properly, exposing themselves to various cyber threats. The article suggests that using a robust External Attack Surface Management (EASM) solution can significantly enhance an organization’s security posture.…
Read More 


 Ep.157: Grifter
Ep.157: Grifter