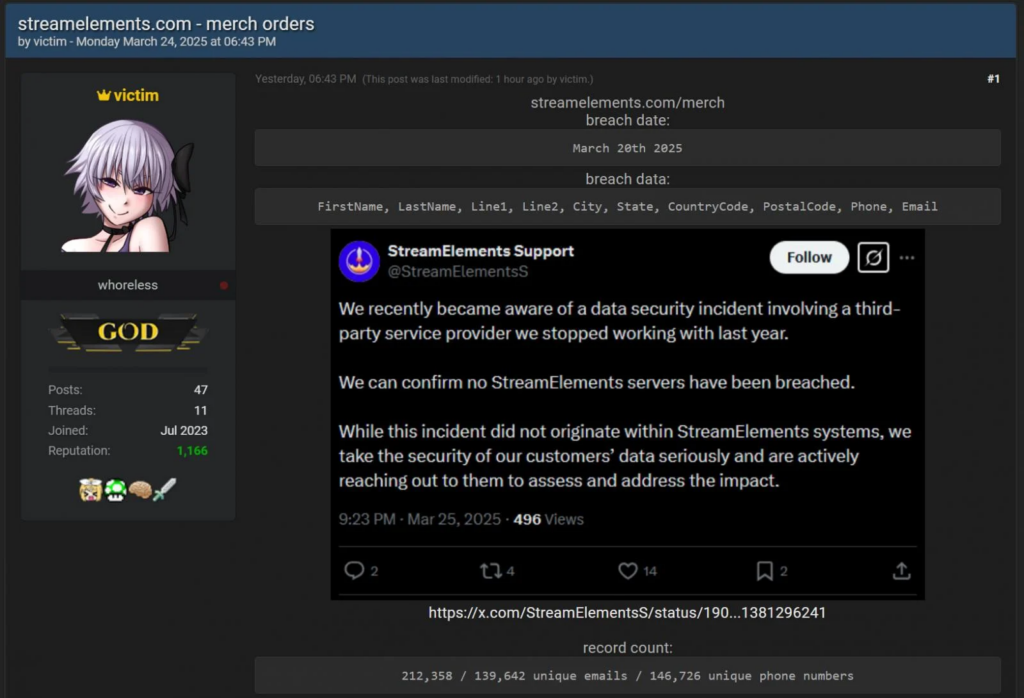
The article provides a detailed analysis of ValleyRAT, a remote access Trojan used by the Silver Fox threat organization. The malware employs various techniques, including deploying both a Trojan and a decoy PDF, to deceive victims while establishing a connection to a command and control server.…
Read More