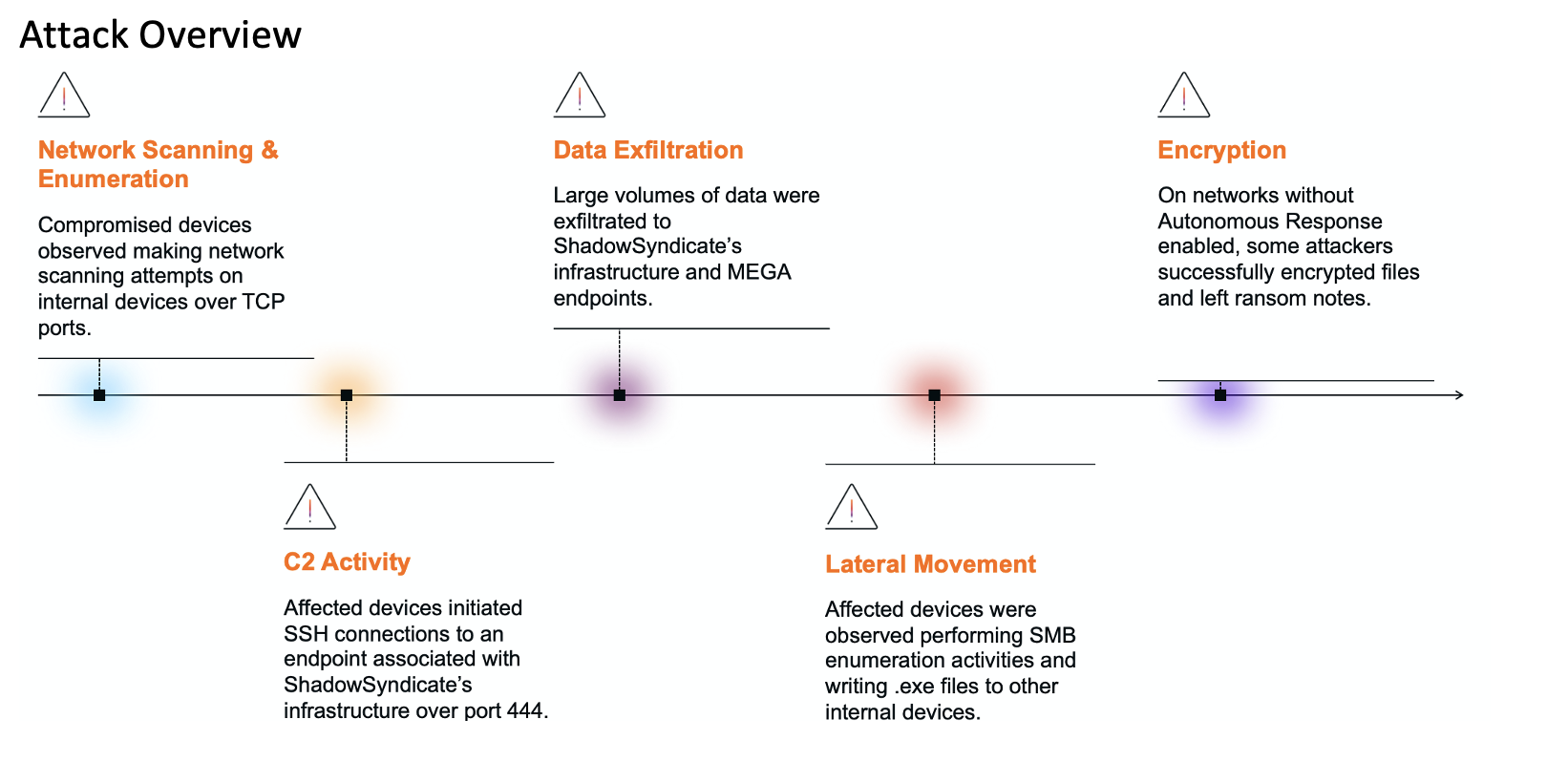
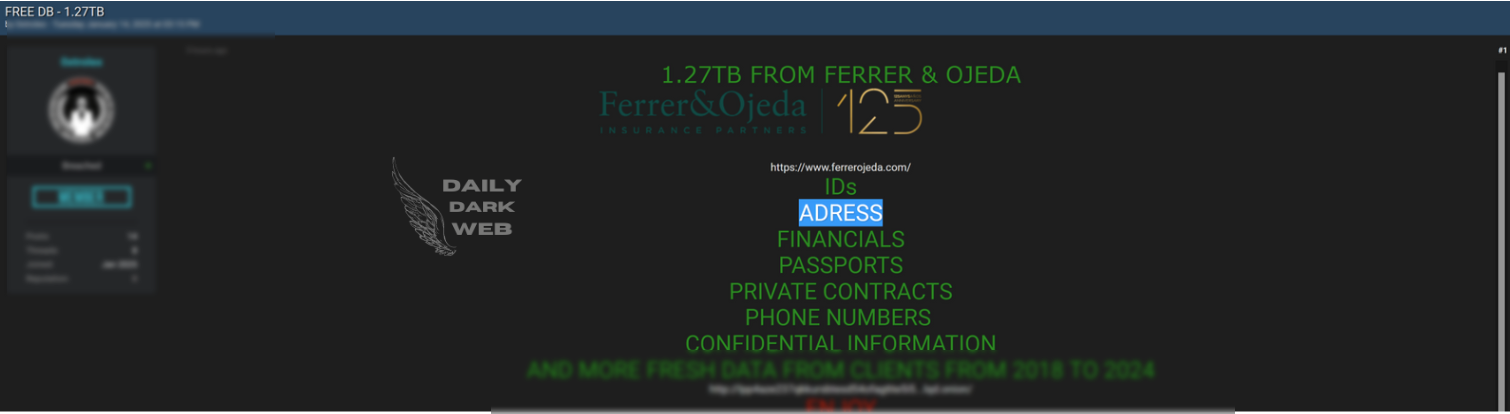
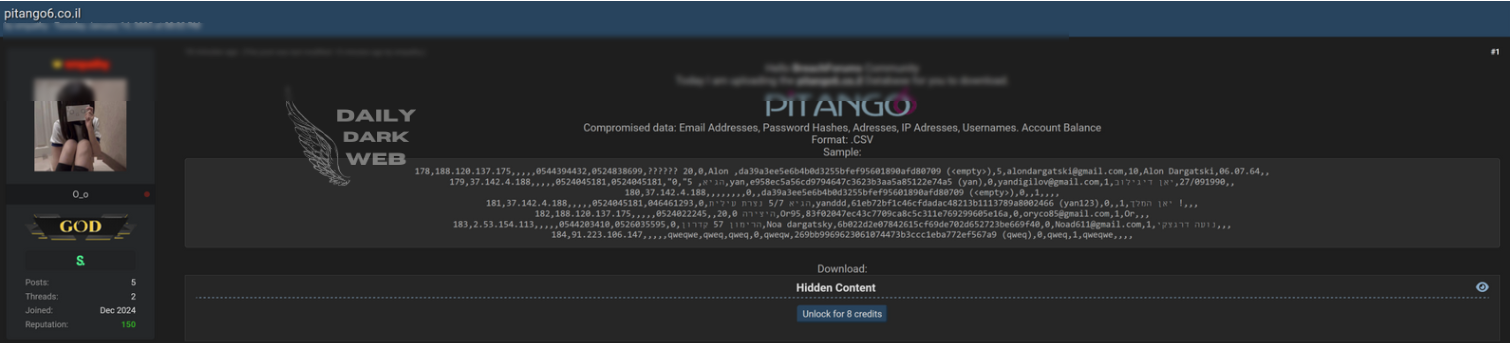
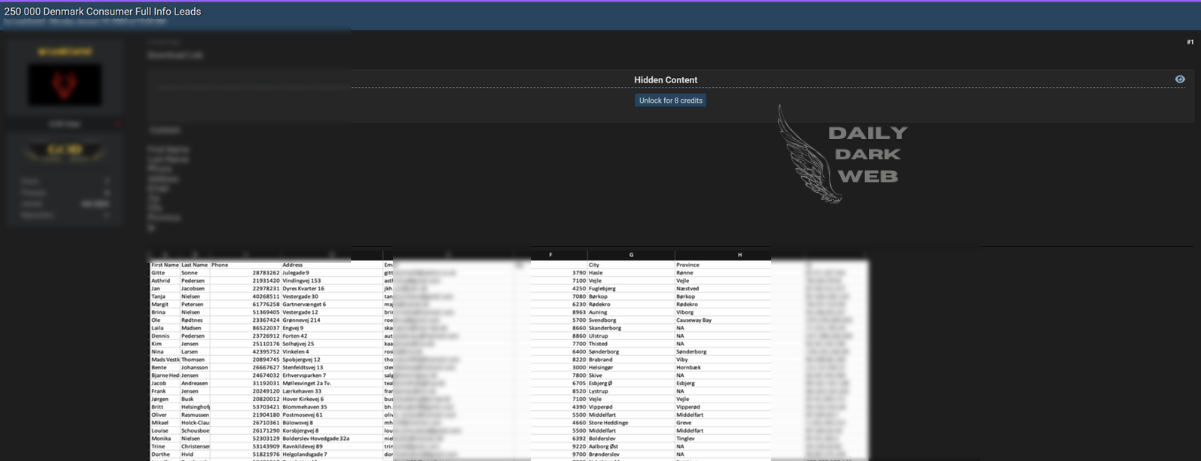
Summary: Ivanti has released patches for multiple critical and high-severity vulnerabilities in its Avalanche, Application Control Engine, and Endpoint Manager (EPM) products, addressing serious security flaws that could be exploited by remote attackers. The most severe issues include absolute path traversal vulnerabilities in EPM, with a CVSS score of 9.8, and several high-severity flaws in Avalanche and Application Control Engine.…
Read More