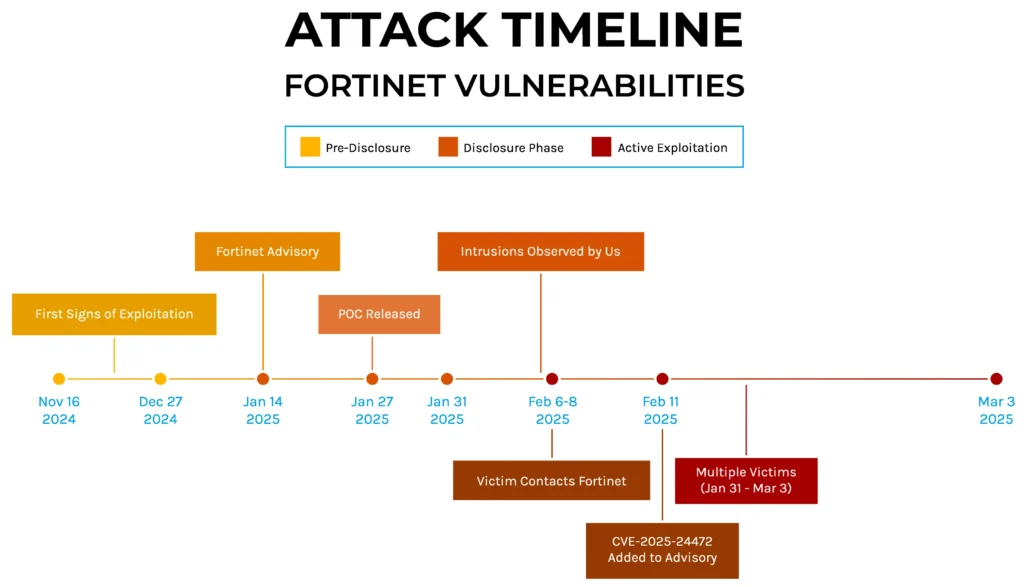
Keypoints :
LockBit ransomware has been operational since 2019, targeting diverse industries.…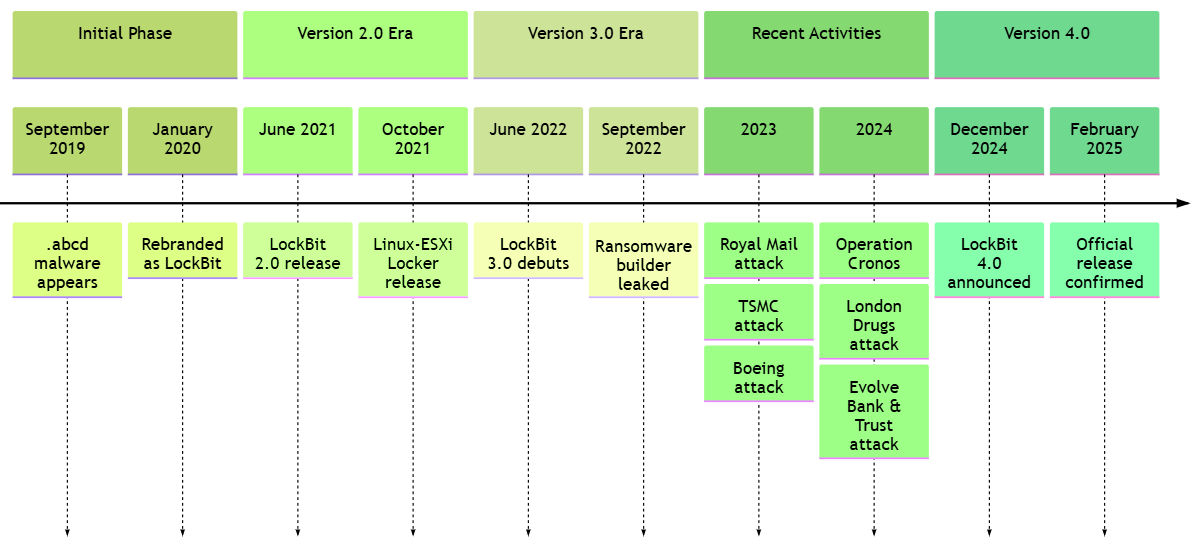
LockBit is a prominent ransomware strain operating since 2019, known for its aggressive tactics and Ransomware-as-a-Service model. The evolution of LockBit has seen the transition from version 3.0 to 4.0, introducing enhanced evasion techniques and impacting various organizations worldwide. Affected: organizations, cybersecurity sector
Read More 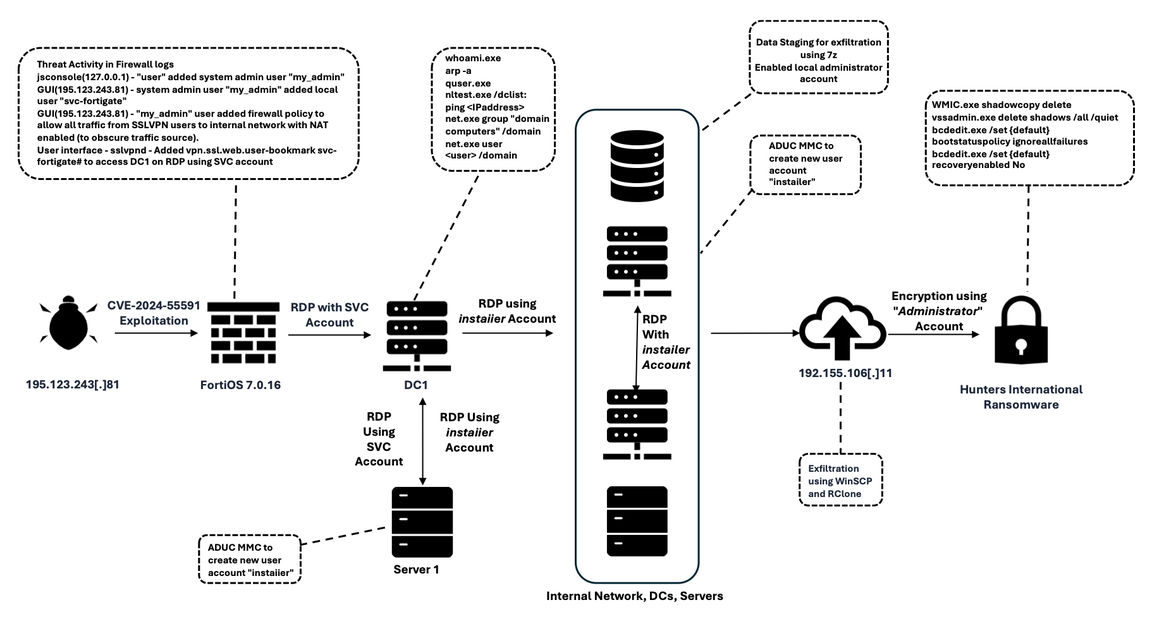

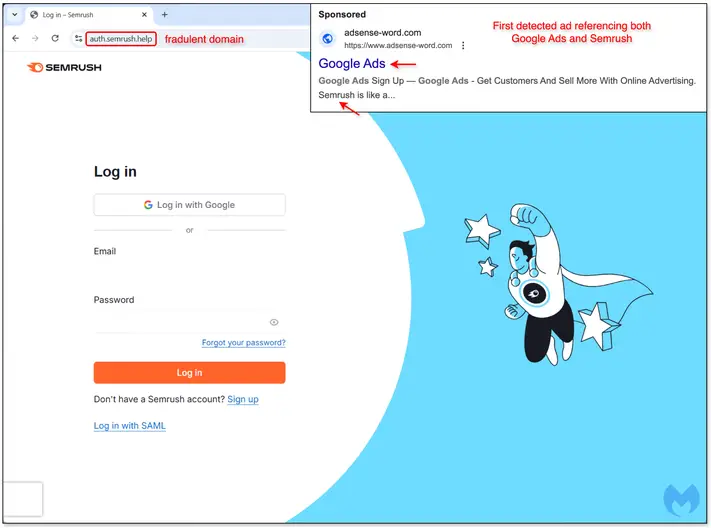




 THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More