This week’s threat intelligence report reveals a range of sophisticated cyber threats, including targeted multistage malware attacks, ransomware groups adopting new backconnect malware, and social engineering tactics employed in recruitment scams. Notable threats included a campaign targeting aviation and transport in the UAE, while other malware leveraged social media for distribution.…
Read More Tag: LATERAL MOVEMENT

Summary: The evolving landscape of cyber threats raises critical concerns around cybersecurity resilience, particularly as state-sponsored groups and new ransomware tactics emerge. Notable events this week include charges against Chinese nationals for hacking and the dismantling of Garantex, a cryptocurrency exchange linked to money laundering. This edition explores the complexities of modern cyber threats and ongoing countermeasures by global law enforcement.…
Read More 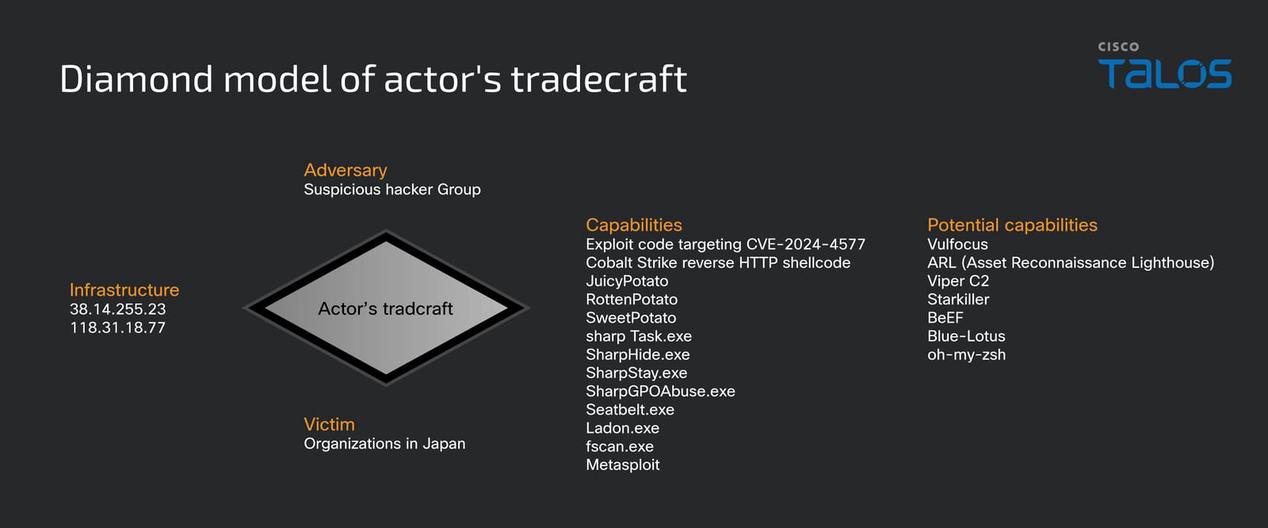
Summary: Cisco Talos has uncovered a sophisticated cyberattack campaign targeting various Japanese industries, actively exploiting a vulnerability in PHP-CGI for remote code execution. The attacks include credential theft, privilege escalation, and deployment of persistent backdoors facilitated by the Cobalt Strike toolkit. Despite similarities to previous hacker group tactics, the attackers’ identities remain unconfirmed.…
Read More 
The SolarWinds hack, a significant supply chain attack discovered in December 2020, compromised numerous Fortune 500 companies and government agencies, resulting in extensive cybersecurity repercussions. Attackers embedded malicious code into SolarWinds’ Orion software updates, infiltrating thousands of networks and highlighting the vulnerabilities in vendor trust. Affected: Fortune 500 companies, US Government agencies, SolarWinds
Read More Keypoints :
The hack was discovered in December 2020, but the infiltration began as early as March 2020.…
In this article, the author details an easy Linux machine exploitation process that begins with gaining foothold through a CVE vulnerability and escalates to root access via another exploit. The author notes the machine’s slow performance and encourages patience during the tests. The walkthrough includes reconnaissance, exploitation of vulnerabilities in the Pymatgen library and Python aiohttp framework, and obtaining root access.…
Read More 
This article provides an overview of pivoting and lateral movement techniques in cybersecurity, focusing particularly on the tool Ligolo-ng. Ligolo-ng is highlighted for its efficiency, user-friendliness, security features, and cross-platform compatibility, making it a valuable asset for penetration testers. The article explains how to set up Ligolo-ng and its advantages compared to other tunneling tools.…
Read More
VulnHub is a platform that offers a safe environment for beginners to practice Vulnerability Assessment and Penetration Testing (VAPT). This guide recommends a variety of machines to enhance skills in network security, web security, and CMS exploitation, moving from beginner to advanced levels. Following this structured approach helps build practical skills and prepares learners for future certifications and career opportunities in cybersecurity.…
Read More 
Stuxnet, introduced in 2010, is recognized as the first digital weapon designed to disrupt Iran’s nuclear enrichment program. Developed through a collaboration between the United States and Israel, it utilized sophisticated malware to compromise industrial control systems, causing physical damage without detection. This cyber weapon dramatically illustrated the potential for malware to affect real-world systems, heralding a new era of cyber warfare.…
Read More 
The latest cybersecurity newsletter highlights vulnerabilities and attacks involving multiple platforms including VMware, Microsoft, Google, and more. Key updates include the patching of critical zero-day vulnerabilities, ransomware attacks, and the rise of sophisticated malware targeting various industries. The report emphasizes the importance of cybersecurity measures to protect sensitive data and infrastructure.…
Read More 
Summary: The Medusa ransomware has emerged as a prominent tool for the threat group known as “Spearwing,” which has targeted nearly 400 victims since 2023. Their ransom demands can range from 0,000 to million, and they employ tactics such as double extortion to pressure victims. The group exploits unpatched vulnerabilities, particularly in Microsoft Exchange Servers, to gain access to networks and conduct attacks.…
Read More 
In response to increasing threats, the Chinese cyber-espionage group Silk Typhoon has adjusted its tactics, focusing on IT supply chains, remote management tools, and cloud services. The group targets Managed Service Providers to gain access to multiple organizations, exploiting unpatched applications and zero-day vulnerabilities. The article outlines recommendations for organizations to enhance their defenses against these evolving threats.…
Read More 
Summary: Researchers have identified Ragnar Loader, a sophisticated malware toolkit utilized by cybercrime groups such as Ragnar Locker and FIN8. Its modular design and advanced features enable long-term access to compromised systems while evading detection. The malware has evolved since its first documentation in 2021, showcasing enhanced capabilities to facilitate illicit operations and communications with attackers.…
Read More 
Summary: NTT Communications Corporation has alerted nearly 18,000 corporate customers that their data was compromised in a cybersecurity incident, discovered on February 5, 2025. The breach specifically impacted the ‘Order Information Distribution System’ and involved sensitive information like customer names, contact details, and service usage data.…
Read More 
This article provides a thorough analysis of the security vulnerabilities associated with low-code/no-code (LCNC) platforms, exposing architectural flaws and real-world breaches. It outlines case studies involving significant breaches such as Microsoft Power Apps and Airtable, highlighting the negligence of platform providers. A call to action for stronger security practices and vendor accountability concludes the report.…
Read More 
A Russian-speaking threat actor has been identified impersonating the Electronic Frontier Foundation (EFF) to target Albion Online players through sophisticated phishing tactics and malware deployment. The campaign employs Stealc and Pyramid C2 malware to steal credentials and compromise player accounts, posing risks such as unauthorized access and loss of in-game assets.…
Read More 
The article discusses the tools and tactics utilized by the Medusa ransomware group, Spearwing. It highlights various software and methods employed for data exfiltration, credential dumping, and maintaining persistence within victim networks. The consistency of their tactics suggests an organized operation, potentially indicating that Spearwing operates more as an individual group rather than a traditional Ransomware-as-a-Service (RaaS).…
Read More 
Threat analysts have identified a sophisticated cyber-intrusion campaign targeting various sectors in Japan, including technology and e-commerce. The attackers exploited a remote code execution flaw in PHP-CGI to gain initial access, followed by deploying PowerShell scripts for persistence and executing other malicious tactics such as credential theft and lateral movement.…
Read More 
Summary: A malicious campaign targeting various sectors in Japan has been attributed to unknown threat actors exploiting the CVE-2024-4577 vulnerability in PHP. The attackers utilize Cobalt Strike plugins for post-exploitation, establishing persistent access and conducting reconnaissance to steal credentials and sensitive data. Their operations utilizing tools hosted on Alibaba cloud servers suggest that their motives may extend beyond credential harvesting, indicating potential future threats.…
Read More 
The Ghost (Cring) ransomware is a critical cybersecurity threat primarily targeting organizations with vulnerable systems, including healthcare, finance, government, and education sectors. This ransomware employs sophisticated techniques such as exploiting vulnerabilities, lateral movement, and advanced evasion methods to encrypt sensitive data and demand ransom payments. Affected: healthcare, financial services, government, critical infrastructure, manufacturing, education, professional services, retail, e-commerce
Read More Keypoints :
Ghost (Cring) ransomware has been active since at least 2021, targeting vulnerable internet-facing systems.…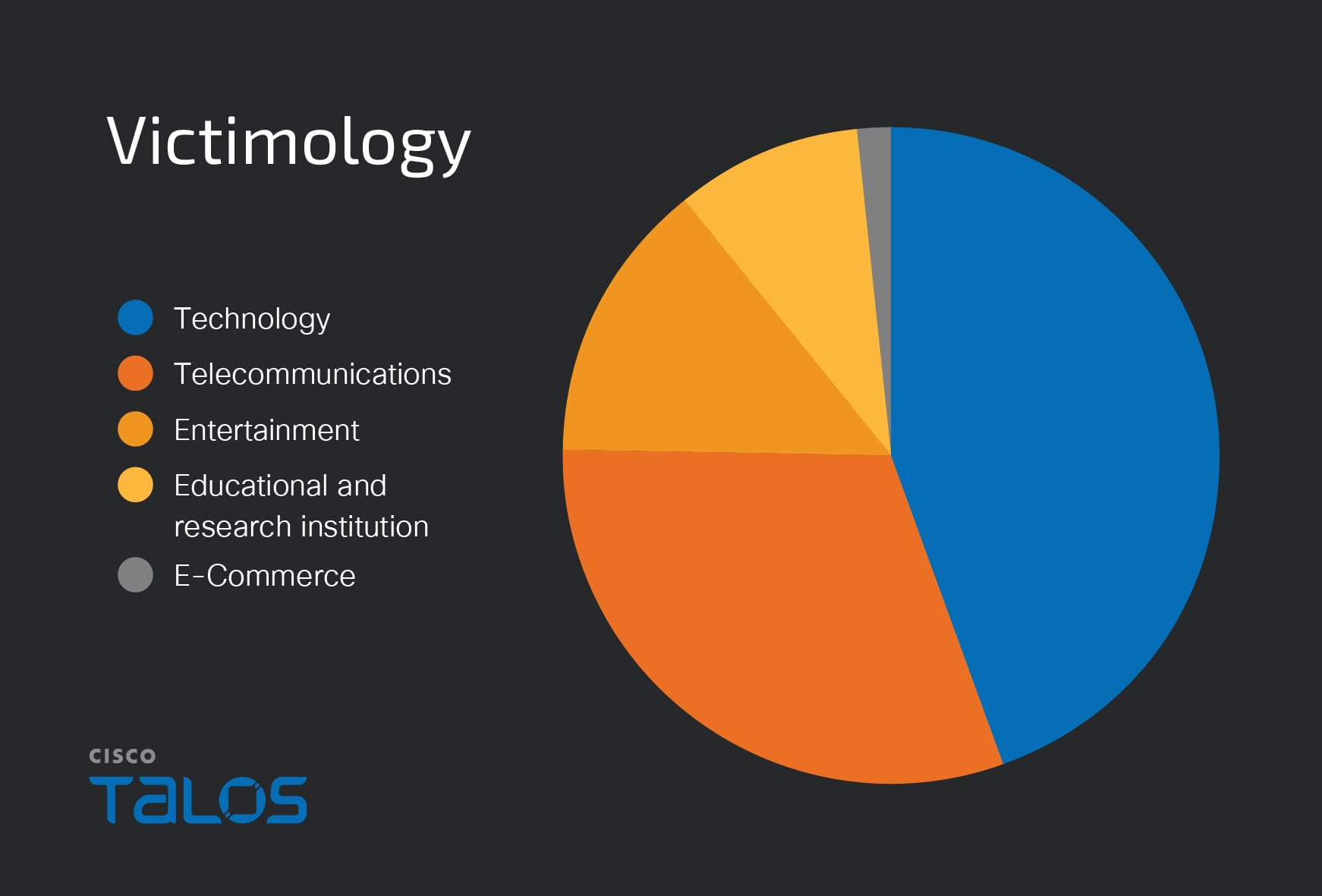
Cisco Talos discovered a malicious campaign attributed to an unknown attacker targeting organizations in Japan since January 2025, primarily exploiting the CVE-2024-4577 vulnerability to gain initial access and deploy advanced adversarial tools via Cobalt Strike. The attacker’s activities entail credential theft, system compromise, and potential lateral movement which could impact various industries.…
Read More  THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact
THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact Cyber Attack Chronicles
Cyber Attack Chronicles