Tag: IOT




Threat Actor: Various | threat actors Victim: Organizations globally | organizations globally
Key Point :
CTI is essential for understanding the nature of cyber threats and enabling proactive defense strategies.…![⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [13 January] ⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [13 January]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh-GVBzJbXbnB628INcZeeGpxnFqxVpcaOaQnUH-g2FpiUGHCsUnPnPNYeuEKDvxOqHzeiB2fZWoNTOO81_P4b77zyyyuaSpWTBjahKirJJMtMXCEIvVUiqsIojlnyGL9pPkB8Dv5-wviS5poLJ_CIYdbkSxjPE4Psyh6mppkjg0M4rWF22fNSR9IgRUqwh/s728-rw-e365/recap.png)
Threat Actor: UNC5337 | UNC5337 Victim: Ivanti | Ivanti
Key Point :
A critical vulnerability in Ivanti Connect Secure appliances has been exploited as a zero-day, allowing for remote code execution.…Keypoints :
Proton Mail experienced a worldwide outage due to a surge in database connections during infrastructure migration.…

Threat Actor: Natohub, Silk Typhoon | Natohub, Silk Typhoon Victim: International Civil Aviation Organization, Bank of America, Green Bay Packers | International Civil Aviation Organization, Bank of America, Green Bay Packers
Key Point :
The US Defense Department has linked Tencent and CATL to the Chinese military.…
Threat Actor: Cybercriminals | cybercriminals Victim: Healthcare Organizations | healthcare organizations
Key Point :
Elisity’s Virtual Edge allows for microsegmentation without new hardware, using lightweight virtual connectors.…



Threat Actor: N/A | N/A Victim: U.S.…

Threat Actor: Cyber attackers | cyber attackers Victim: American consumers | American consumers
Key Point :
The Cyber Trust Mark program allows manufacturers to undergo cybersecurity audits for their smart products.…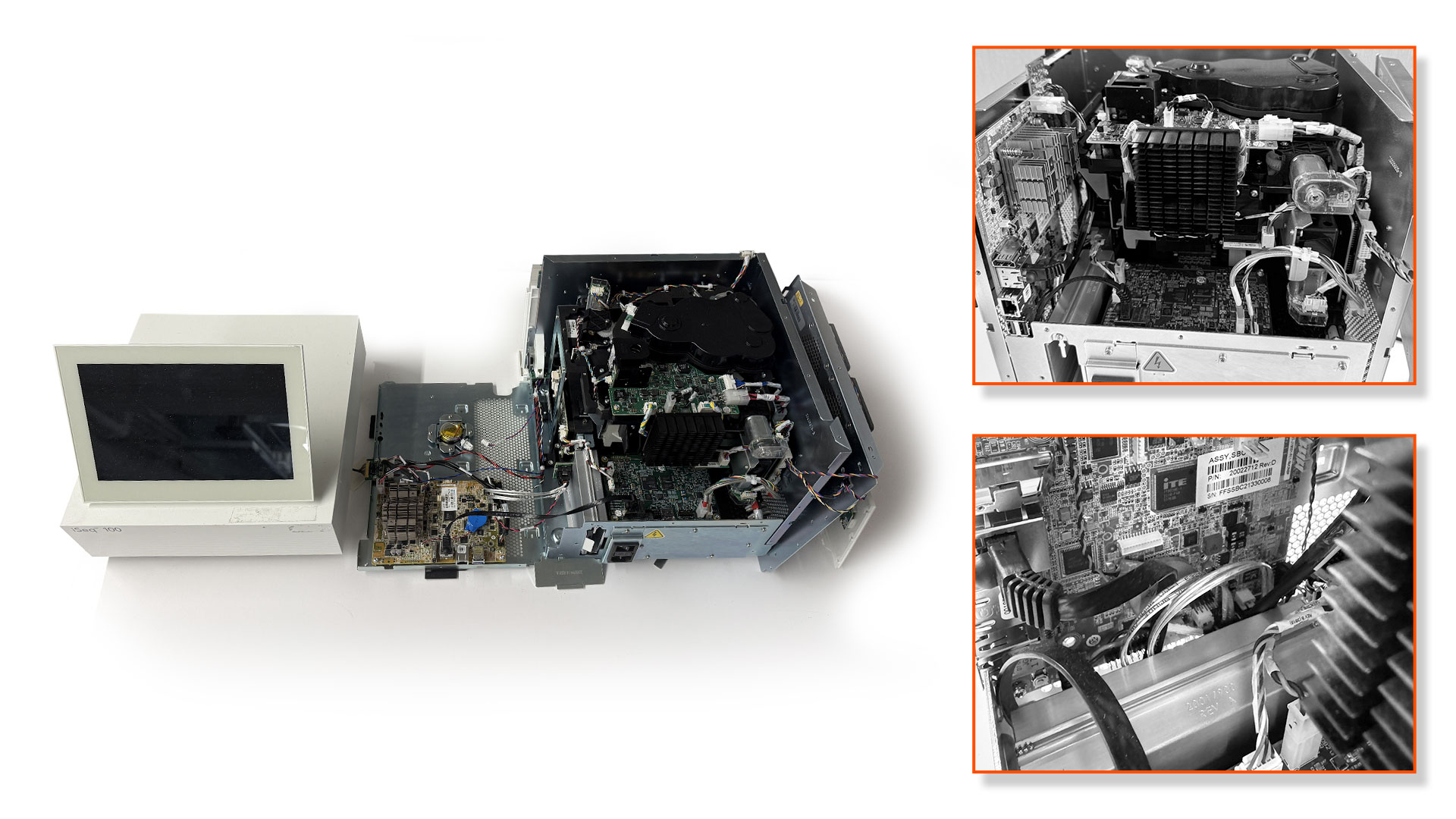
Keypoints :
Illumina iSeq 100 uses outdated BIOS firmware without Secure Boot or write protections.…
Threat Actor: Unknown | unknown Victim: MediaTek | MediaTek
Key Point :
Critical vulnerability CVE-2024-20154 allows remote code execution via rogue base stations.…Keypoints :
The cyber threat landscape is becoming increasingly sophisticated and hazardous.…