Summary: Apple released security updates for various operating systems to address two actively exploited vulnerabilities. The flaws pertain to memory corruption in the Core Audio framework and a bypass issue in the RPAC component. Users are urged to update their devices to enhance security and mitigate risks.…
Read More Tag: IOS

Multiple vulnerabilities have been identified affecting various Apple components, including WebKit and system applications, which can lead to unauthorized access to sensitive user data, process crashes, and exploitation of user permissions. The vulnerabilities range from crashing applications due to malicious content to unauthorized data access without user consent.…
Read More 
Summary: Apple has released emergency security updates to address two zero-day vulnerabilities in multiple operating systems that were used in sophisticated attacks on targeted iPhones. The vulnerabilities, CVE-2025-31200 in CoreAudio and CVE-2025-31201 in RPAC, affect a wide range of Apple devices. Users are urged to update their devices immediately to safeguard against potential exploitation.…
Read More
A recent study by SecureList reveals the emergence of a malicious SDK named “SparkCat” found in Android and iOS apps, targeting users by stealing crypto wallet recovery phrases. Infected apps on Google Play have reached over 242,000 downloads, and the SDK has been operational since March 2024.…
Read More 
This newsletter highlights various recent security breaches and critical vulnerabilities affecting major organizations like DBS Group, Oracle, Europcar, and more. It emphasizes the increasing trend of supply chain attacks, challenges posed by legacy systems, and the need for vigilant vendor security assessments. Affected: DBS Group, Bank of China, Oracle Cloud, Europcar Mobility Group, State Bar of Texas, Port of Seattle, Google Gemini, Microsoft Windows, Linux Kernel, Apache Tomcat, reviewdog/action-setup, Chromium, Juniper Junos OS, Apple WebKit
Read More Keypoints :
Multiple significant breaches reported, including ransomware attacks and data exposure.…
The article examines the sophisticated cyber espionage group known as BlackTech, believed to be state-sponsored by the People’s Republic of China. Since at least 2010, they have targeted critical sectors across East Asia and the US, employing advanced tactics, techniques, and procedures (TTPs) to infiltrate networks and steal valuable information.…
Read More 
Microsoft has issued a critical security update addressing 126 vulnerabilities across several products like Windows, Microsoft Office, and Azure, including serious threats such as privilege escalation and remote code execution. Users are urged to apply these patches promptly to mitigate risks. Affected: Windows, Microsoft Office, Azure, Microsoft Edge, Microsoft Visual Studio
Read More Keypoints :
Microsoft released an April security update patch for 126 vulnerabilities.…
Summary: Cybersecurity researchers have discovered deceptive websites impersonating legitimate app stores to distribute SpyNote malware, which targets Android devices. This malware is linked to known threat actors, including state-sponsored groups, and is capable of extensive data theft and control over infected devices. Additionally, intelligence agencies have issued alerts regarding other malware threats like BadBazaar and MOONSHINE, which target specific communities for surveillance.…
Read More 
Summary: A recent analysis by Guy Bruneau reveals the ongoing risks of a seven-year-old Cisco vulnerability, CVE-2018-0171, which still affects over 1,200 devices worldwide. This vulnerability allows attackers to execute arbitrary commands on devices using the Smart Install feature, raising serious security concerns due to its default enabled state and lack of authentication.…
Read More 
Summary: Flipper Devices has introduced Busy Bar, an open-source productivity tool designed to aid individuals with ADHD by minimizing distractions. The device incorporates features such as an LED display, fidget buttons, and smart home integration, optimizing the working environment for users. It aims to enhance productivity through controlled focus periods while managing interruptions effectively.…
Read More 
Summary: The UK’s National Cyber Security Centre, in collaboration with cybersecurity agencies from five countries, has issued a joint advisory on two spyware variants, BADBAZAAR and MOONSHINE, which are actively targeting Uyghur, Tibetan, and Taiwanese communities. This spyware campaign seeks to monitor and intimidate these groups perceived as threats by the Chinese state.…
Read More 
Summary: The U.K.’s National Cyber Security Centre highlights the deployment of two spyware types, MOONSHINE and BADBAZAAR, targeting Uyghur, Tibetan, and Taiwanese individuals and organizations. These spyware apps can access sensitive information without the victims’ knowledge, leveraging popular platform designs to lure users. The NCSC warns at-risk populations to be vigilant regarding app usage and permissions to mitigate the risks of surveillance.…
Read More 
Summary: Microsoft’s April 2025 Patch Tuesday addresses 134 vulnerabilities, including one actively exploited zero-day and multiple critical flaws that enable remote code execution. The updates are currently available for Windows Server and Windows 11, with Windows 10 updates expected shortly. Affected organizations should prioritize these updates to protect their systems from potential exploits.…
Read More 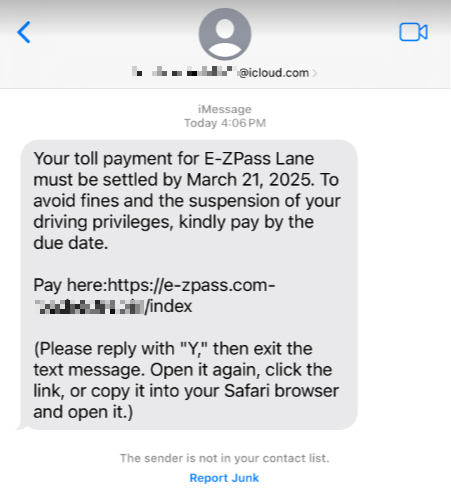
This article discusses a new wave of SMS phishing scams targeting toll fee payments in the US. Scammers send urgent text messages that link to fake toll agency websites, aiming to steal personal and payment information. State departments are alerting the public about these phishing attempts and emphasizing vigilance and verification.…
Read More 
Summary: The cybersecurity landscape is plagued by persistent threats stemming from unpatched systems, oversights, and social engineering tactics that facilitate breaches. This report highlights significant vulnerabilities and recent breaches linked to well-known organizations and emerging threat actors. The trends illustrate a critical need for companies to prioritize security measures against increasingly sophisticated attacks.…
Read More 
This week’s edition of Malloc Privacy Weekly highlights significant cybersecurity threats including the misuse of free VPN apps owned by Chinese companies, a new phishing-as-a-service platform called Lucid, and various malware threats targeting Android devices. The report emphasizes the need for users to be aware of privacy risks and consider enhanced protective measures when using technology.…
Read More 
The article discusses the utilization of XPC (Cross-Process Communication) in macOS applications, highlighting its vulnerabilities and the significance of using tools like Frida for dynamic analysis. As macOS transitions to ARM architecture, the article explores changes in how XPC operates and mentions that tools like IPSW offer enhanced capabilities over traditional ones like class-dump.…
Read More 
Summary: A vulnerability in the Verizon Call Filter application could have been exploited to access the call records of millions of American users. Discovered by cybersecurity researcher Evan Connelly, the flaw allowed attackers to potentially retrieve call metadata by exploiting a lack of verification on user phone numbers.…
Read More 
Summary: A hacker breached the GitLab repositories of Europcar Mobility Group, stealing source code for mobile applications and personal data of up to 200,000 customers. The attacker threatened to release 37GB of sensitive data, which reportedly includes backups and internal details. Europcar is currently assessing the damage and notifying affected customers.…
Read More 
This week’s newsletter covers significant cyber threats, including a surge in scanning for PAN GlobalProtect VPNs, ongoing attacks targeting Apache Tomcat, a critical vulnerability in Apache Parquet, and multiple breaches affecting organizations such as Oracle and the State Bar of Texas. Recommendations for mitigation and security measures are emphasized throughout the article.…
Read More  Cybersecurity And Much More – Vol. 5 2
Cybersecurity And Much More – Vol. 5 2 Weekly Recap: VPN Exploits, Oracle’s Silent Breach, ClickFix Surge and More
Weekly Recap: VPN Exploits, Oracle’s Silent Breach, ClickFix Surge and More