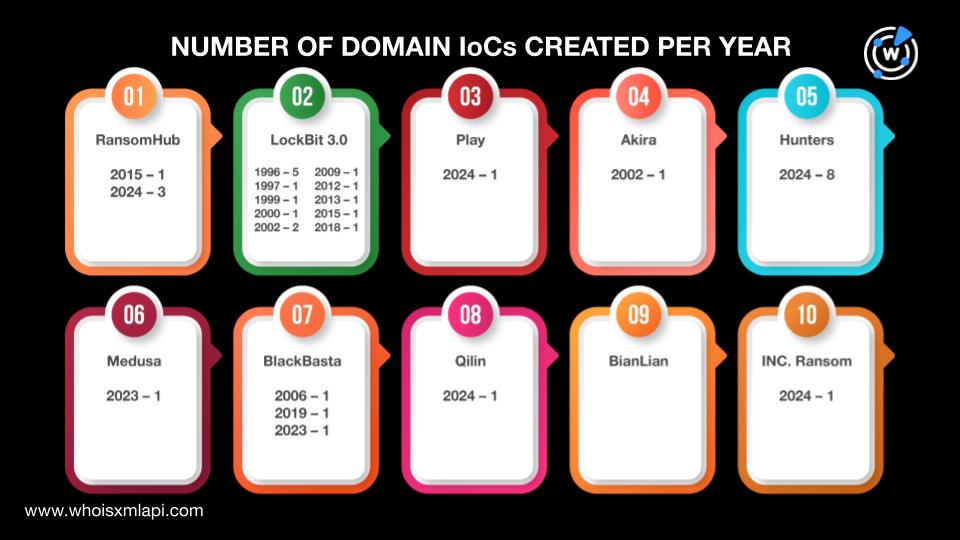
Keypoints :
User Account Control (UAC) was introduced in Windows Vista to prevent unauthorized system changes.…
This article discusses bypassing User Account Control (UAC) in Windows using the UACMe tool, developed by @hfire0x. It explains UAC’s purpose in Windows security and details the steps to exploit its vulnerabilities, specifically for educational purposes. Affected: Windows Operating System
Read More