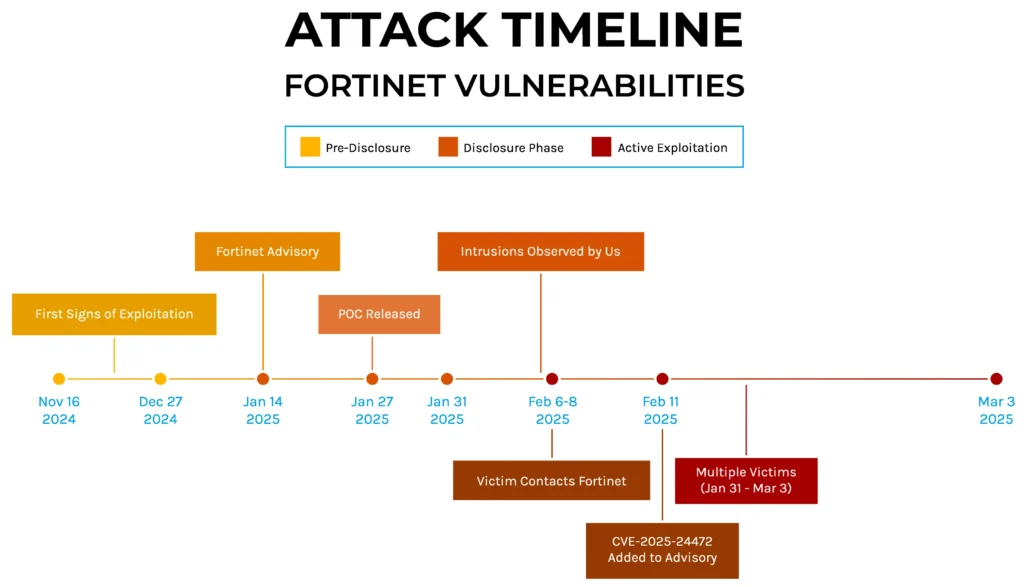
Keypoints :
The term “Lazarus” has evolved from a singular APT group to multiple subgroups.…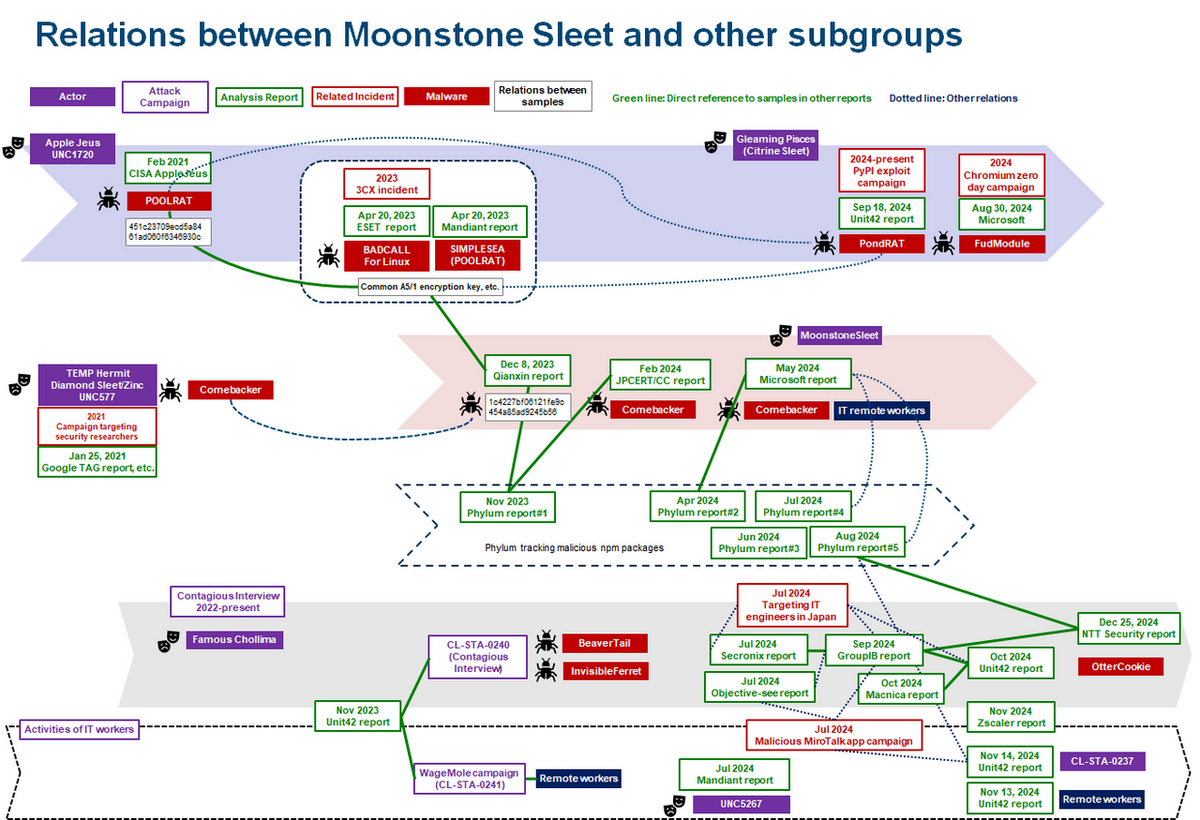
The article discusses the evolution of the Lazarus group, indicating that it has now transformed into a collection of subgroups rather than a single entity. It emphasizes the importance of understanding these subgroups, their tactics, and their individual characteristics for effective cyber defense strategies. Affected: Japan, cryptocurrency sector, defense industry, aviation industry
Read More 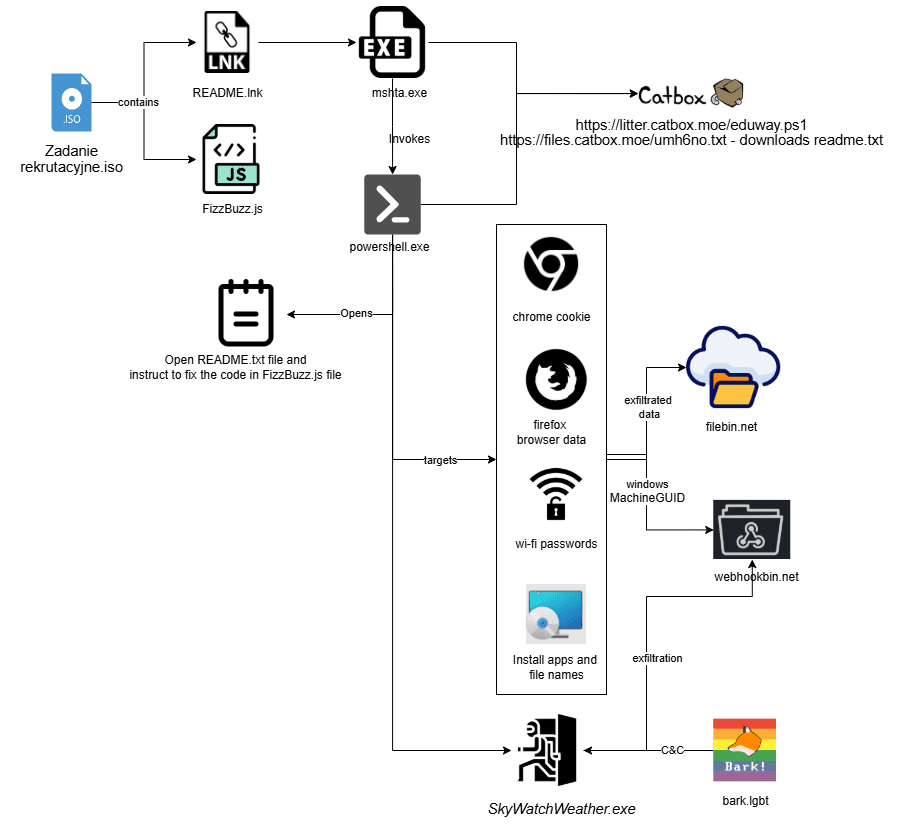


 THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More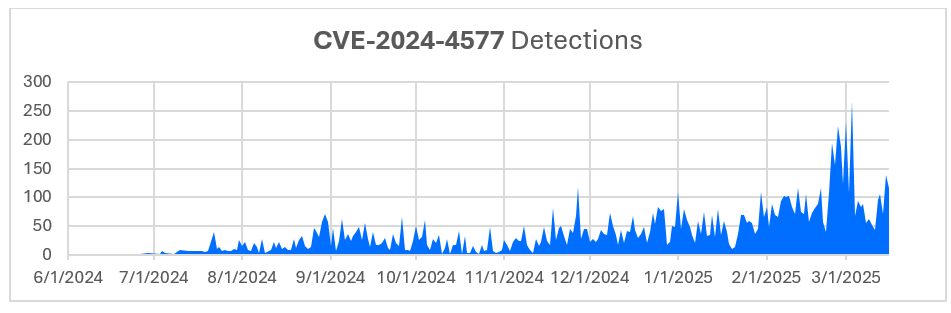
 RECONNAISSANCE:
RECONNAISSANCE: