
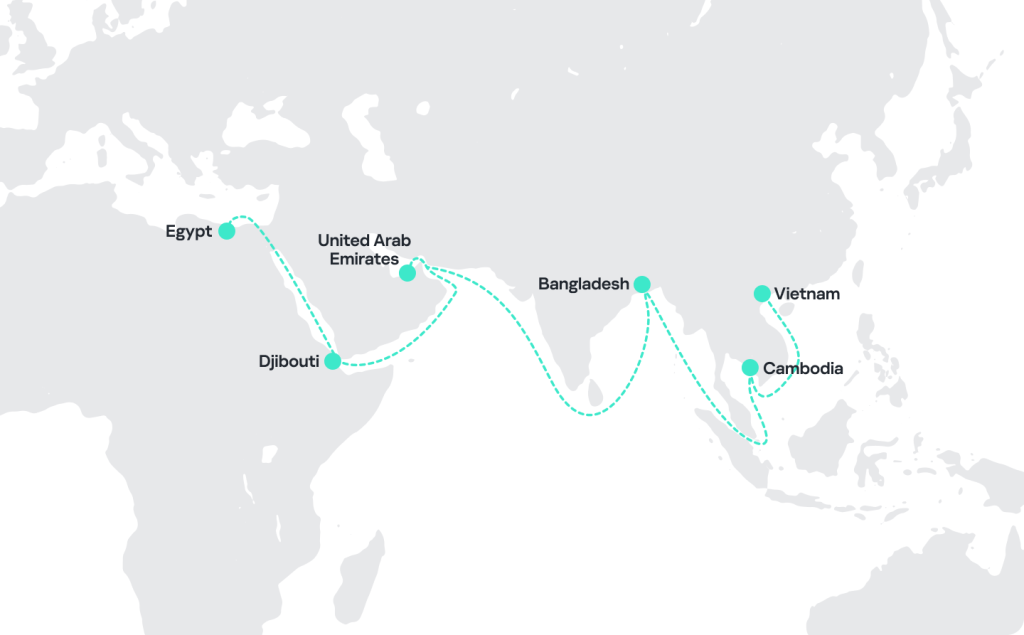
Tag: INDONESIA

Attacker: root./exe – Target: dewanganjbhata.gov.bd – Source: zone-h – Victim Country: Bangladesh – Sector: Government – This website appears to be part of the local government infrastructure, possibly dealing with administrative functions.…
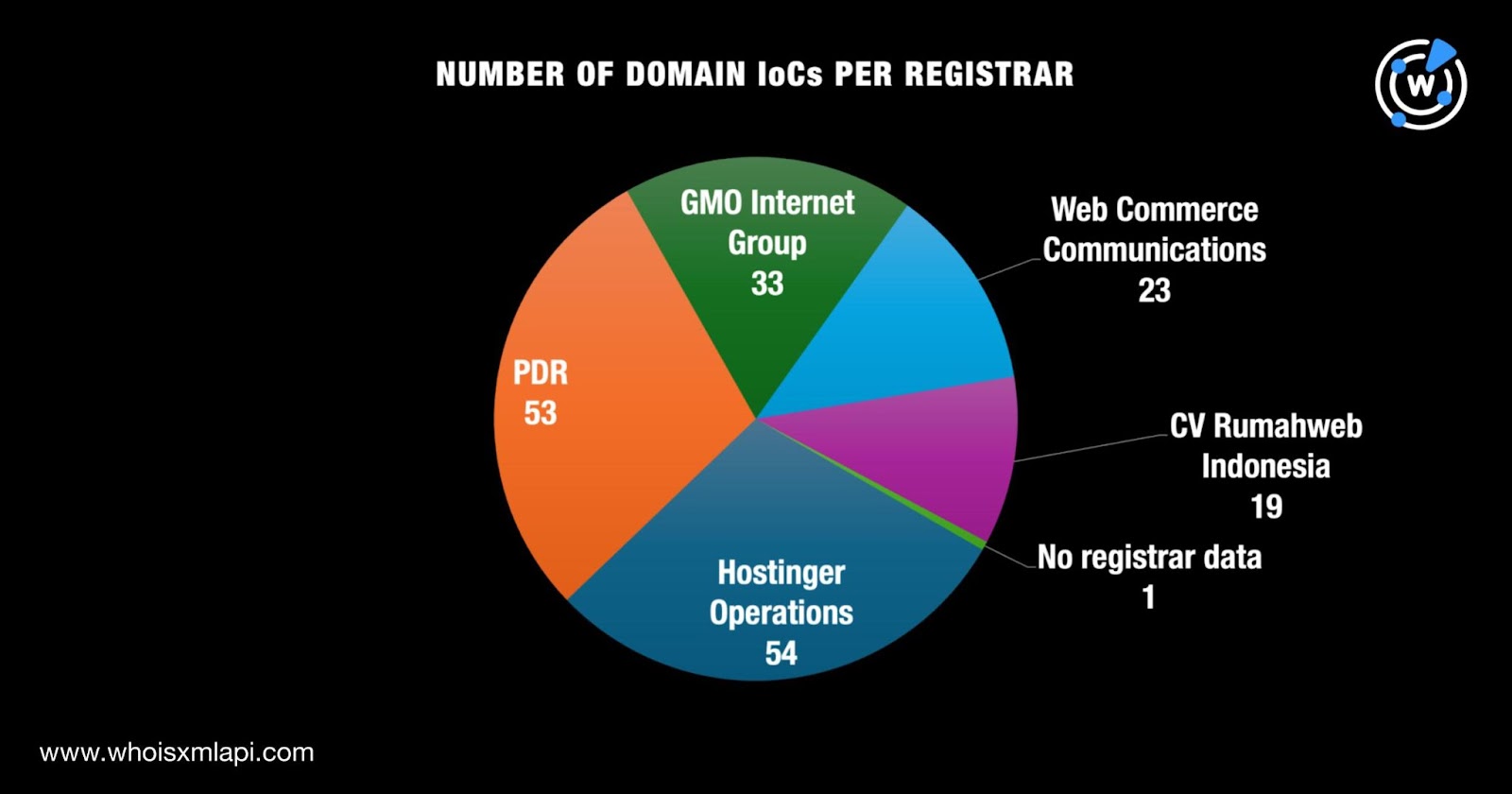
Keypoints :
Phishing-as-a-service (PhaaS) offering called FlowerStorm emerged post-Rockstar2FA disruption.…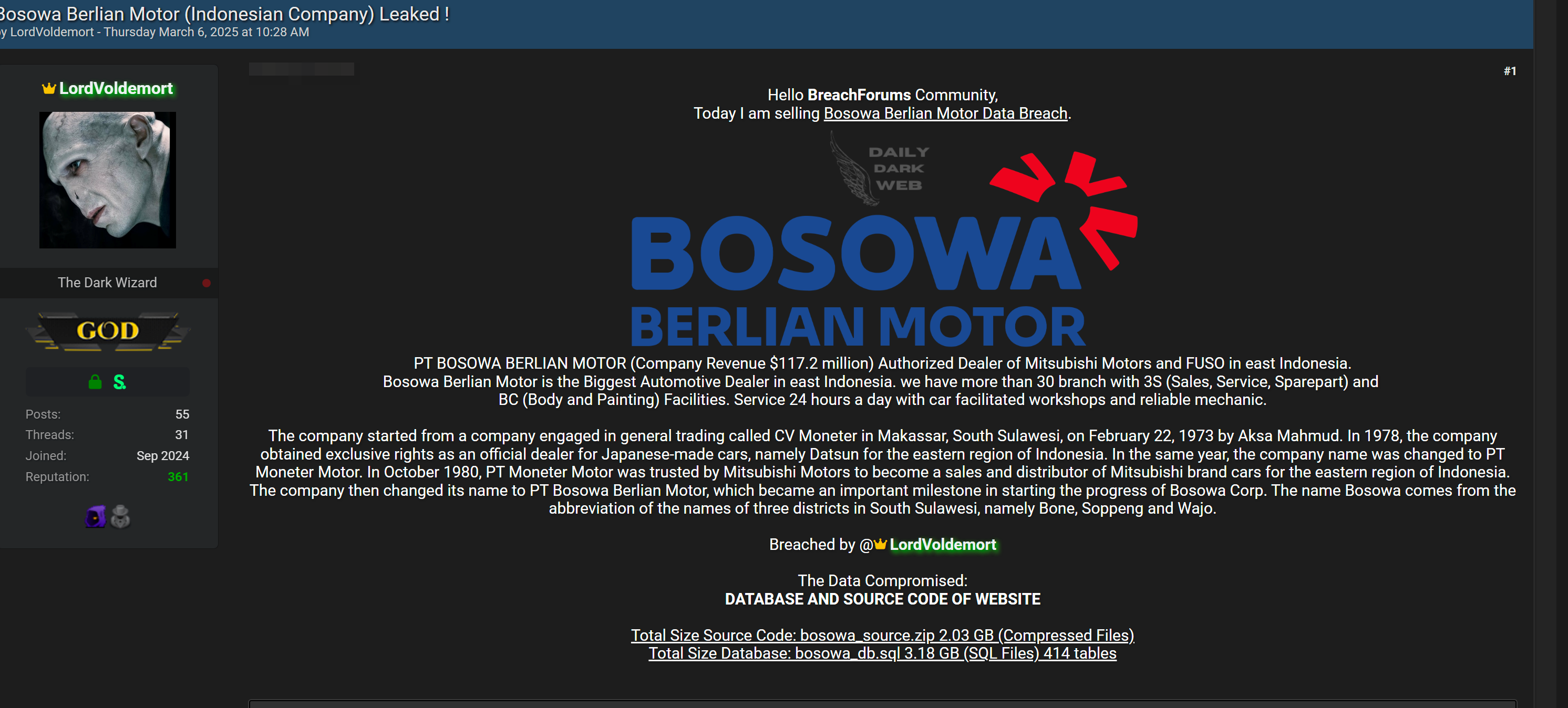
—
SABUNMANDI CYBER TEAMTarget: https://osvitalanmisto.gov.ua/hack.txt Source: zone-h.org Victim Country: Ukraine Sector: Government (local government website targeted) Description: A cyber attack targeting a Ukrainian local government website, compromising government information.…
Target: http://uwc.edostate.gov.ng/kurd.html Source: zone-h.org Victim Country: Nigeria Sector: Education – The targeted URL is associated with the Universal College of Nigeria, indicating a breach in educational resources. Description: An attacker exploited security vulnerabilities in Nigeria’s educational website, compromising resources intended for students and educators.…

—
Attacker: -1 Target: https://periodicooficial.michoacan.gob.mx Source: zone-h.org Victim Country: Mexico Sector: Government – Official publication platform for state announcements and legal documents. Description: This website serves as a platform for disseminating official state information and legislation in Michoacán, Mexico.…
1. Target: https://ccomp.ufsj.edu.br/media/n2/indi.html Source: Zone-H Link Victim Country: Brazil Sector: Education (Targeting a local university’s computing department) Description: This incident involved unauthorized access to a local university’s computing department, highlighting vulnerabilities within educational institutions in Brazil.…
—
Attacker: KeyzNet Target: https://ayuntamientocotija.gob.mx Source: zone-h.org Victim Country: Mexico Sector: Local Government (The website is associated with a municipal government in Mexico, representing local governance and public administration.) Description: This hack targets the official municipal website of Cotija, Mexico, indicating potential disruptions in local governance and public services during the breach.…
—
Attacker: KeyzNet Target: ayuntamientocotija.gob.mx Source: zone-h.org Victim Country: Mexico Sector: Local Government – The site represents the local government of Cotija, indicating targeting of municipal services. Description: The website of the municipal government in Cotija, Mexico, was compromised, potentially affecting local governance and communication with residents.…

– Target: www.s291066.brambling.cdu.edu.au/Image%20Upload… – Source: Defacer ID – Victim Country: Australia – Sector: Education (University or educational institution website likely containing student or academic-related data) – Description: An attack on an Australian educational website aimed at compromising student data or disrupting academic services.…
![[Law] Hacker behind over 90 data breaches arrested in Thailand [Law] Hacker behind over 90 data breaches arrested in Thailand](https://www.hendryadrian.com/tweet/image/cybersecuritynews.png)



—
Attacker: -1 Target: https://dikbud.kolutkab.go.id Source: zone-h Victim Country: Indonesia Sector: Cultural Affairs – Targeting a governmental website related to education and cultural affairs, which may hold important information about education policies in the region.…