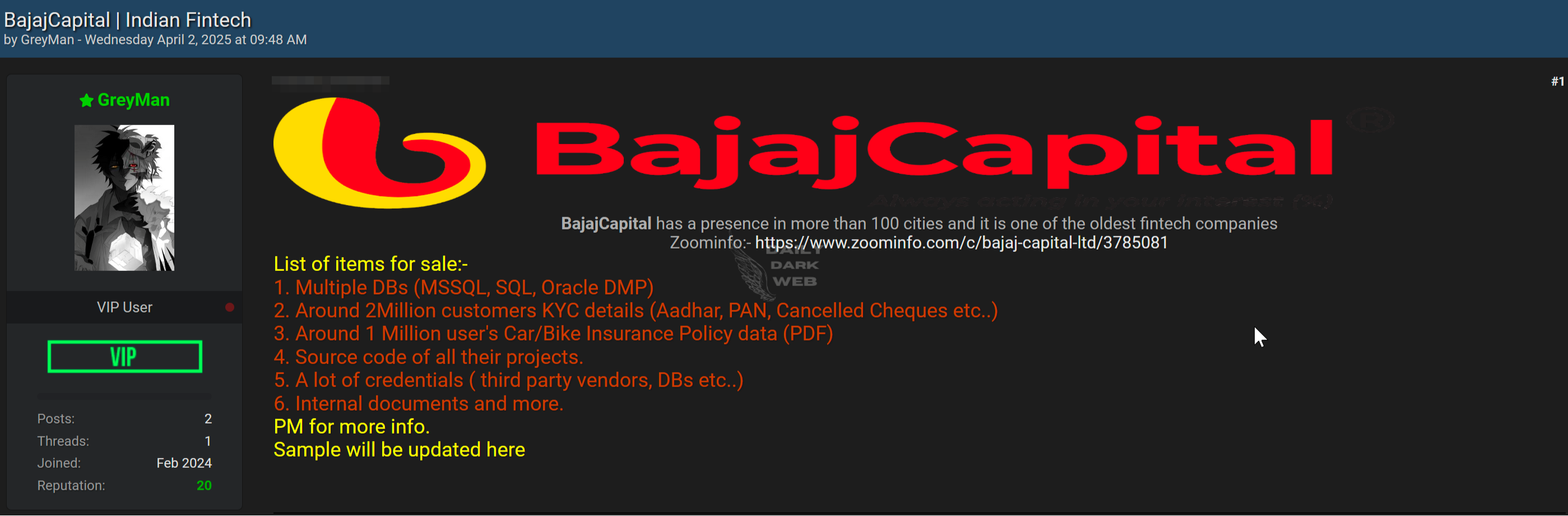
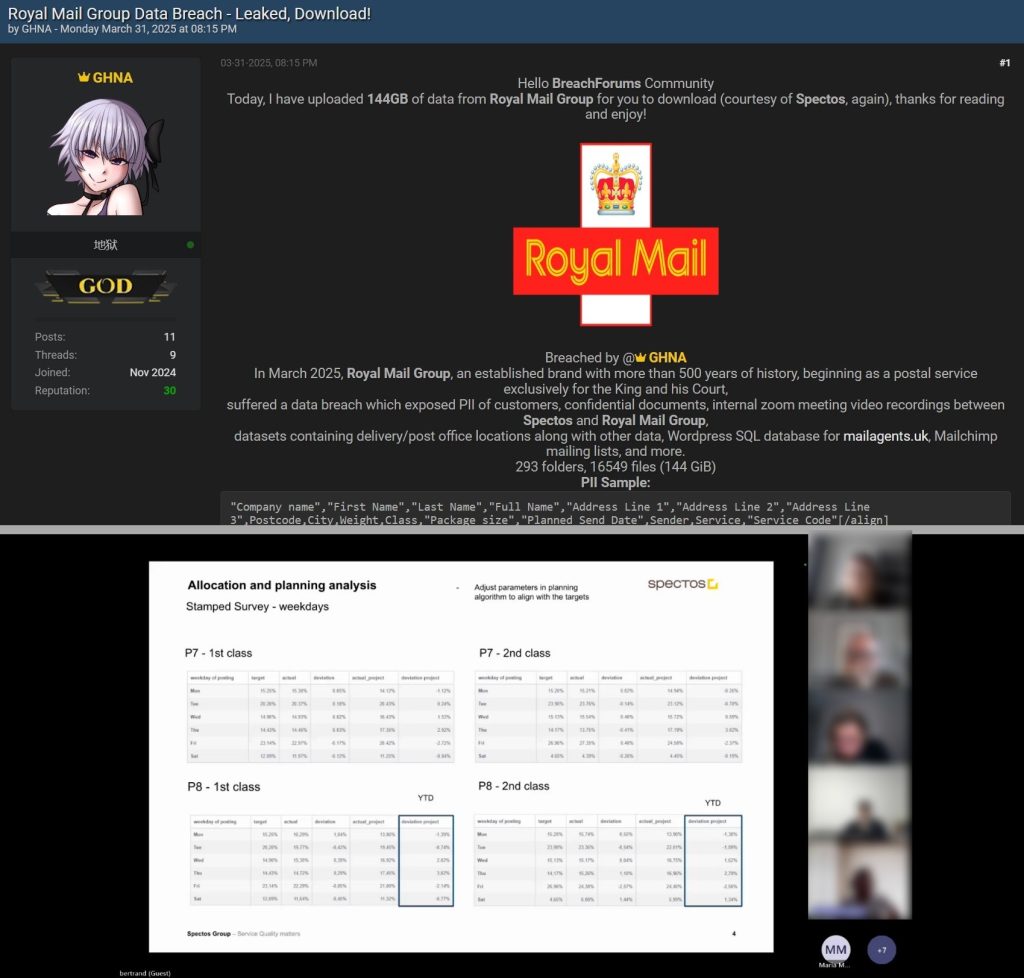
Summary: Oracle has confirmed a data breach involving legacy client credentials after attackers exploited vulnerabilities in 2017 systems, affecting user emails and hashed passwords. Despite Oracle’s claims that the breach did not impact Oracle Cloud, evidence suggests otherwise. Additionally, Oracle Health has also experienced a security incident that compromised patient data from U.S.…
Read More