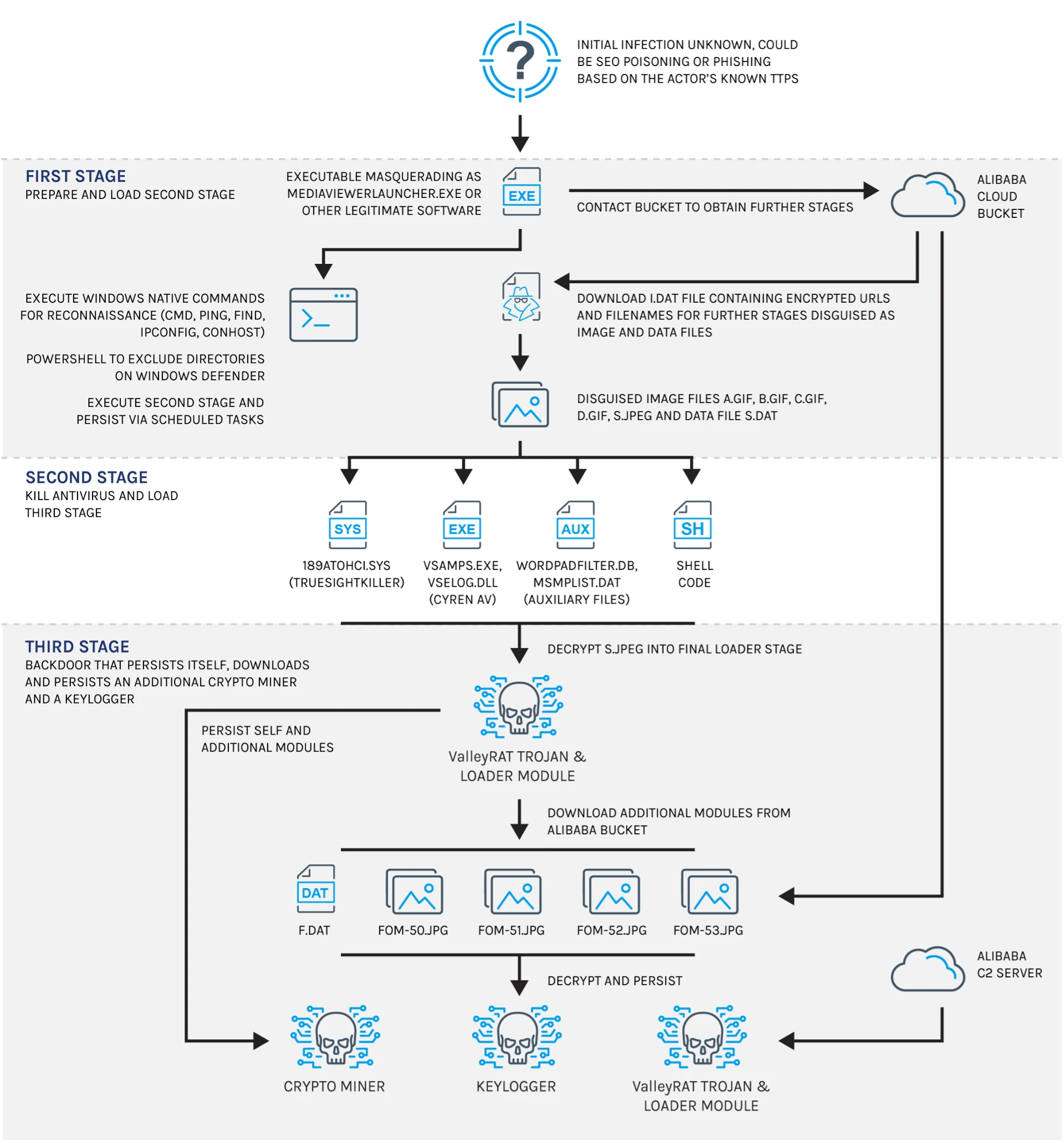
Keypoints :
The hack was discovered in December 2020, but the infiltration began as early as March 2020.…
The SolarWinds hack, a significant supply chain attack discovered in December 2020, compromised numerous Fortune 500 companies and government agencies, resulting in extensive cybersecurity repercussions. Attackers embedded malicious code into SolarWinds’ Orion software updates, infiltrating thousands of networks and highlighting the vulnerabilities in vendor trust. Affected: Fortune 500 companies, US Government agencies, SolarWinds
Read More  Cyber Attack Chronicles
Cyber Attack Chronicles










_Luis_Moreira_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop)