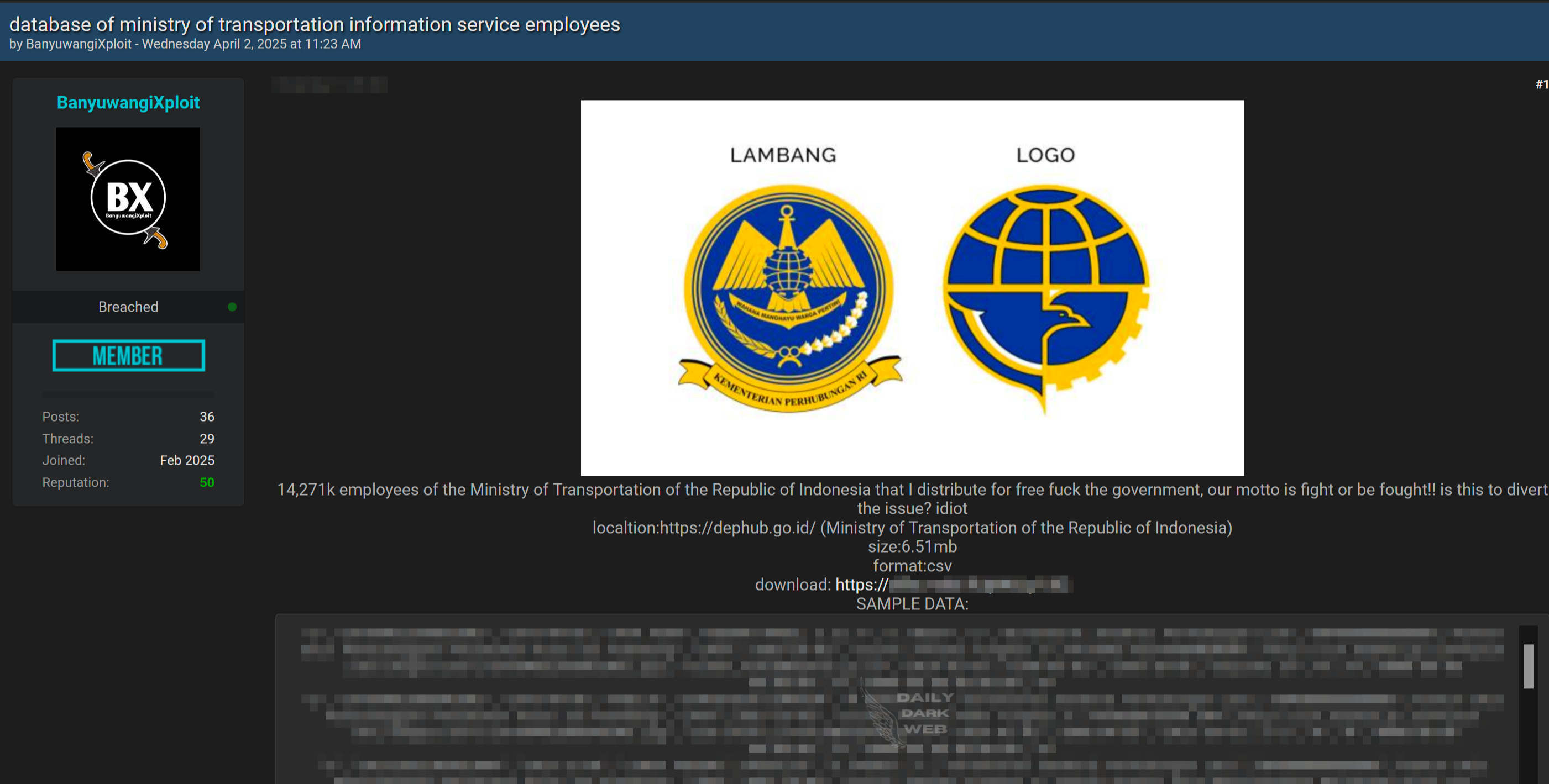
Summary: A dark web forum post claims to have leaked the personal data of 14,271 employees from the Indonesian Ministry of Transportation, providing a downloadable CSV file. The leak is purportedly an act of defiance against the government, coupled with inflammatory remarks indicating a political motive.…
Read More