Victim: nadra.gov.pk – NADRA official Of Pakistan Army & (Andhra Pradesh)
Country : PK
Actor: babuk2
Source: http:/bxwu33iefqfc3rxigynn3ghvq4gdw3gxgxna5m4aa3o4vscdeeqhiqad.onion/blog/a3ddb365f1307e9df5b9e0c16ceaf025b9af209f95465f95fba9f0f11ee65962/
Discovered: 2025-03-27 07:51:50.113913
Published: 2025-03-27 07:50:41.641973
Description :
The website nadra.gov.pk, which serves as the official portal for the National Database and Registration Authority (NADRA) of Pakistan, has recently fallen victim to a ransomware attack perpetrated by the Babuk2 actor.…
Read More Tag: GOVERNMENT

Summary: The UAE government successfully thwarted a major cyberattack aimed at 634 government and private entities, attributed to a hacker known as “rose87168.” The breach, potentially exposing around six million customer records, raises significant concerns about ongoing cyber threats to the UAE, highlighting the necessity for robust cybersecurity measures.…
Read More Victim: nadra.gov.pk – NADRA official Of Pakistan Army
Country : PK
Actor: babuk2
Source: http:/bxwu33iefqfc3rxigynn3ghvq4gdw3gxgxna5m4aa3o4vscdeeqhiqad.onion/blog/a3ddb365f1307e9df5b9e0c16ceaf025b9af209f95465f95fba9f0f11ee65962/
Discovered: 2025-03-27 04:53:01.380860
Published: 2025-03-27 04:51:54.045200
Description :
NADRA, the official agency of the Pakistan Army responsible for national identity management, has fallen victim to a ransomware attack perpetrated by the Babuk2 hacking group.…
Read More 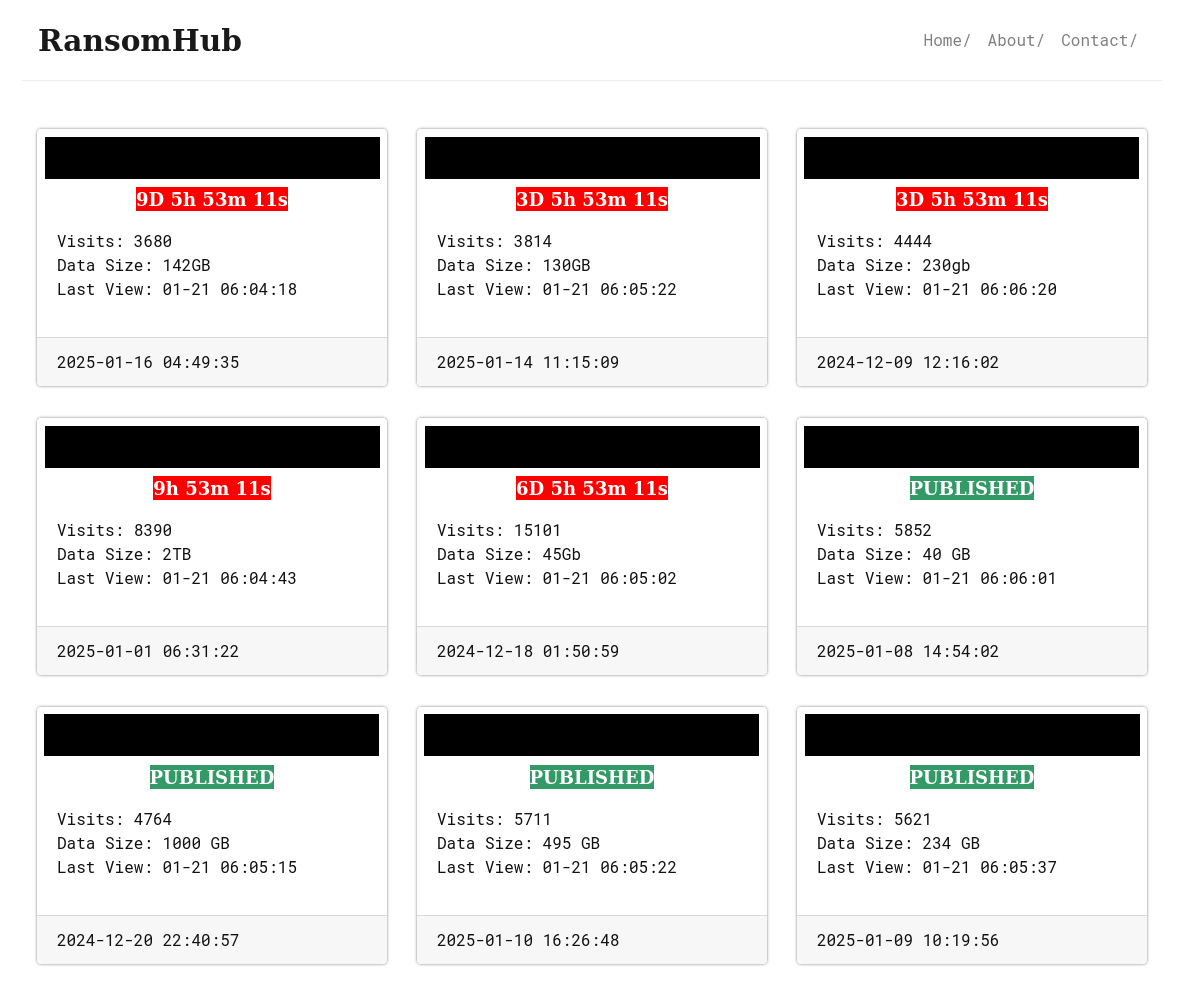
ESET researchers examine the ransomware landscape in 2024, highlighting the emergence of RansomHub, a prominent ransomware-as-a-service (RaaS) group linked to established gangs like Play, Medusa, and BianLian. The article discusses the rise of EDR killers, particularly EDRKillShifter, developed by RansomHub, and reflects on the shifting dynamics of ransomware payments and victim statistics.…
Read More 
Summary: Advanced, an IT services provider for UK healthcare, was fined £3.1 million for security failures linked to a ransomware attack in 2022 that compromised the data of 79,404 individuals. The attack disrupted NHS services significantly and raised concerns about the adequacy of cybersecurity measures within the sector.…
Read More 
Summary: OpenAI has increased its bug bounty payout to 0,000 to enhance the discovery of critical vulnerabilities. This initiative is part of a larger security program that includes funding for cybersecurity research and collaboration with experts. OpenAI is actively inviting hackers to propose projects and providing microgrants to accelerate the development of innovative security solutions.…
Read More 
Summary: A Chinese hacker group, FamousSparrow, has launched cyber attacks targeting a U.S. trade group and a Mexican research institute, deploying advanced versions of their backdoor tools, SparrowDoor and a new variant of ShadowPad. This marks the first observed use of ShadowPad by this group, which has a history of attacks involving hotel and government sectors.…
Read More 
Summary: Colin Ahern, New York state’s first chief cyber officer, reflects on his journey from military intelligence to leading cybersecurity efforts. During his tenure, he has focused on protecting government systems from escalating cyber threats, particularly ransomware. Ahern discusses the collaboration needed between state and local governments, as well as the essential role of education in promoting cybersecurity awareness.…
Read More 
Summary: A Chinese hacking group known as FamousSparrow, previously considered dormant, has resurfaced to target organizations in the U.S., Mexico, and Honduras. Researchers from ESET discovered upgrades to their backdoor tool, SparrowDoor, indicating ongoing cyber-espionage activities since 2022. The group is linked to a series of attacks on various sectors, including government and research institutes, using sophisticated malware and tools, showcasing a notable evolution in their tactics.…
Read More 
Summary: President Donald Trump’s intelligence chiefs defended their handling of a messaging app discussion regarding a U.S. military strike, asserting no classified information was shared despite new revelations. The House Intelligence Committee witnessed heated exchanges over the implications of the leaked Signal conversation that included sensitive military details.…
Read More 
Summary: MORSE Corp, a defense contractor based in Cambridge, Massachusetts, has settled with the U.S. government for .6 million due to violations of federal cybersecurity requirements. The settlement stems from allegations that the company misrepresented its cybersecurity posture and failed to comply with standards set by the National Institute of Standards and Technology.…
Read More Here’s a summary of the hacking incidents based on the provided report:
Minaton4kpoloz
Read More 1. Target: disperindag.jatengprov.go.id/v3/publik/berita_b… Source: defacer.id/mirror/id/144135 Victim Country: Indonesia Sector: Government Affairs – This target is related to the provincial government’s public information platform.
2. Target: kecbrangsong.kendalkab.go.id/berita/id/20250115… Source: defacer.id/mirror/id/144134 Victim Country: Indonesia Sector: Government Affairs – Another website belonging to a local government, focusing on local news and public announcements.…
Summary: The video discusses significant cybersecurity threats from vulnerabilities in software and hardware, particularly focusing on a long-known Microsoft bug that is being exploited by multiple hacker organizations. Steve Gibson addresses critical issues such as the risk presented by remote takeovers of Apache Tomcat servers, the dangers of using the Signal app for sensitive communications by government officials, and the impending threat of post-quantum cryptography to current security systems.…
Read More 
Summary: Google has addressed a high-severity zero-day vulnerability, CVE-2025-2783, in Chrome that was being exploited to escape the browser’s sandbox for espionage attacks targeting Russian organizations. The flaw allows attackers to deploy sophisticated malware through phishing campaigns. The patch is being rolled out for users globally, with further details on the attacks yet to be fully disclosed by Google.…
Read More 
Summary: Google has released urgent fixes for a high-severity vulnerability in Chrome for Windows, known as CVE-2025-2783, which has been actively exploited to target organizations in Russia. The flaw involves an incorrect handle in Mojo, allowing attackers to bypass browser protections through phishing emails. This marks the first actively exploited Chrome zero-day of the year, with attacks linked to a sophisticated APT campaign called Operation ForumTroll.…
Read More 
Kaspersky technologies identified a sophisticated wave of malware infections targeting various organizations through phishing emails leading to malicious links. A critical zero-day vulnerability in Google Chrome, identified as CVE-2025-2783, allowed attackers to bypass the browser’s sandbox. The malware campaign, dubbed Operation ForumTroll, aimed at espionage targeting media outlets and government entities in Russia.…
Read More 
Summary: A major telecommunications company in Asia suffered a breach by Chinese state-sponsored hackers known as Weaver Ant, who maintained a prolonged presence in their systems for over four years. The attackers employed advanced techniques, including the use of web shells and a unique tool dubbed INMemory, to facilitate cyber espionage and maintain access to sensitive data.…
Read More 
Summary: A recent investigation has revealed nearly 200 unique command-and-control domains linked to the malware Raspberry Robin, a complex threat actor that acts as an initial access broker for various criminal groups, particularly those associated with Russia. This malware facilitates access for various malicious strains and employs multiple distribution methods, including USB propagation and communication via Discord.…
Read More 
Summary: Kaspersky Labs has identified a complex cyber-espionage campaign named Operation ForumTroll, utilizing a new Google Chrome zero-day exploit (CVE-2025-2783) initiated through spear-phishing emails. The attack required no additional action from victims once they accessed the malicious link, with the exploit bypassing Chrome’s sandbox protections. This operation is believed to be conducted by a state-sponsored APT group targeting Russian media, educational institutions, and government organizations.…
Read More 
Summary: Google has released a patch for a critical vulnerability (CVE-2025-2783) in its Chrome browser that was exploited in a state-sponsored cyberespionage campaign. Kaspersky identified this vulnerability as part of a sophisticated attack targeting Russian organizations, utilizing drive-by downloads through phishing techniques. The patch was expedited following the discovery of a sandbox escape flaw that compromised Chrome’s security measures.…
Read More