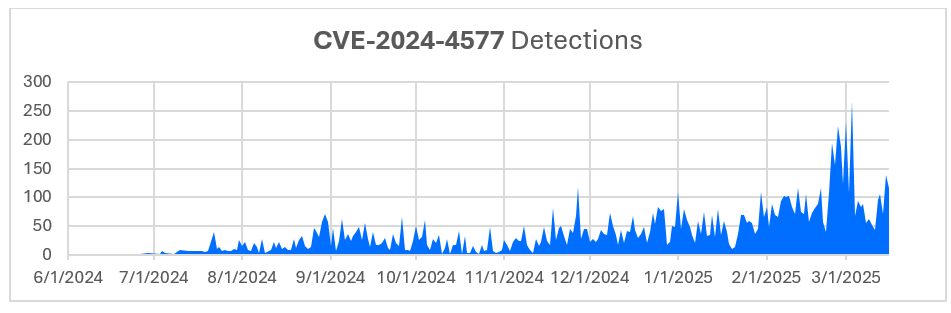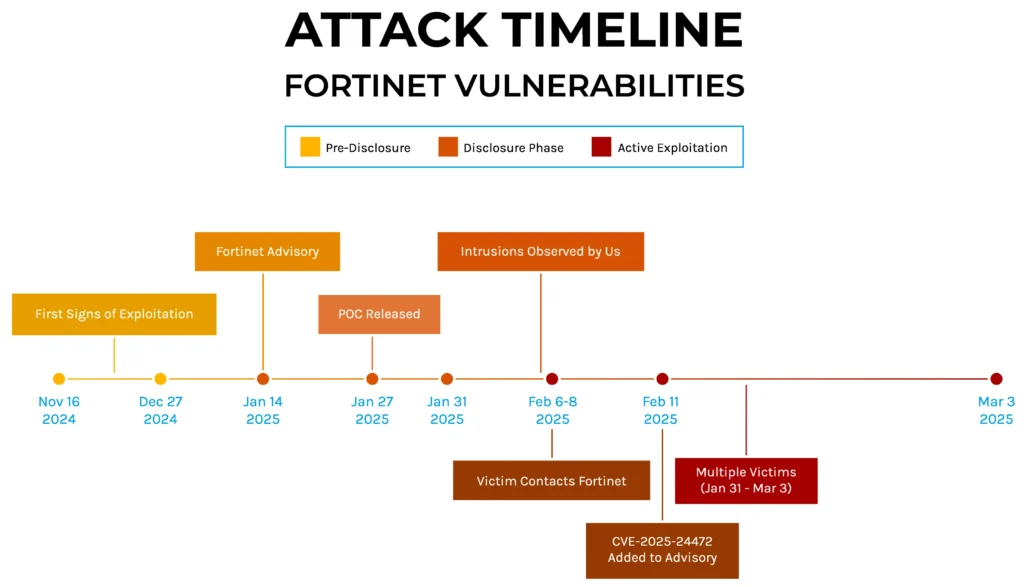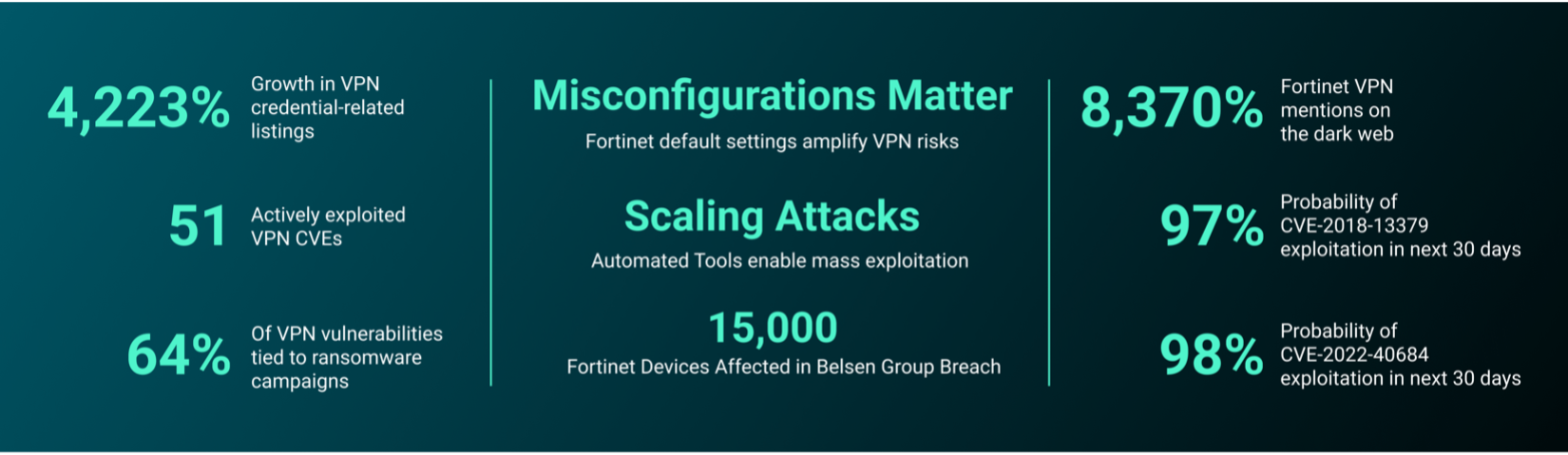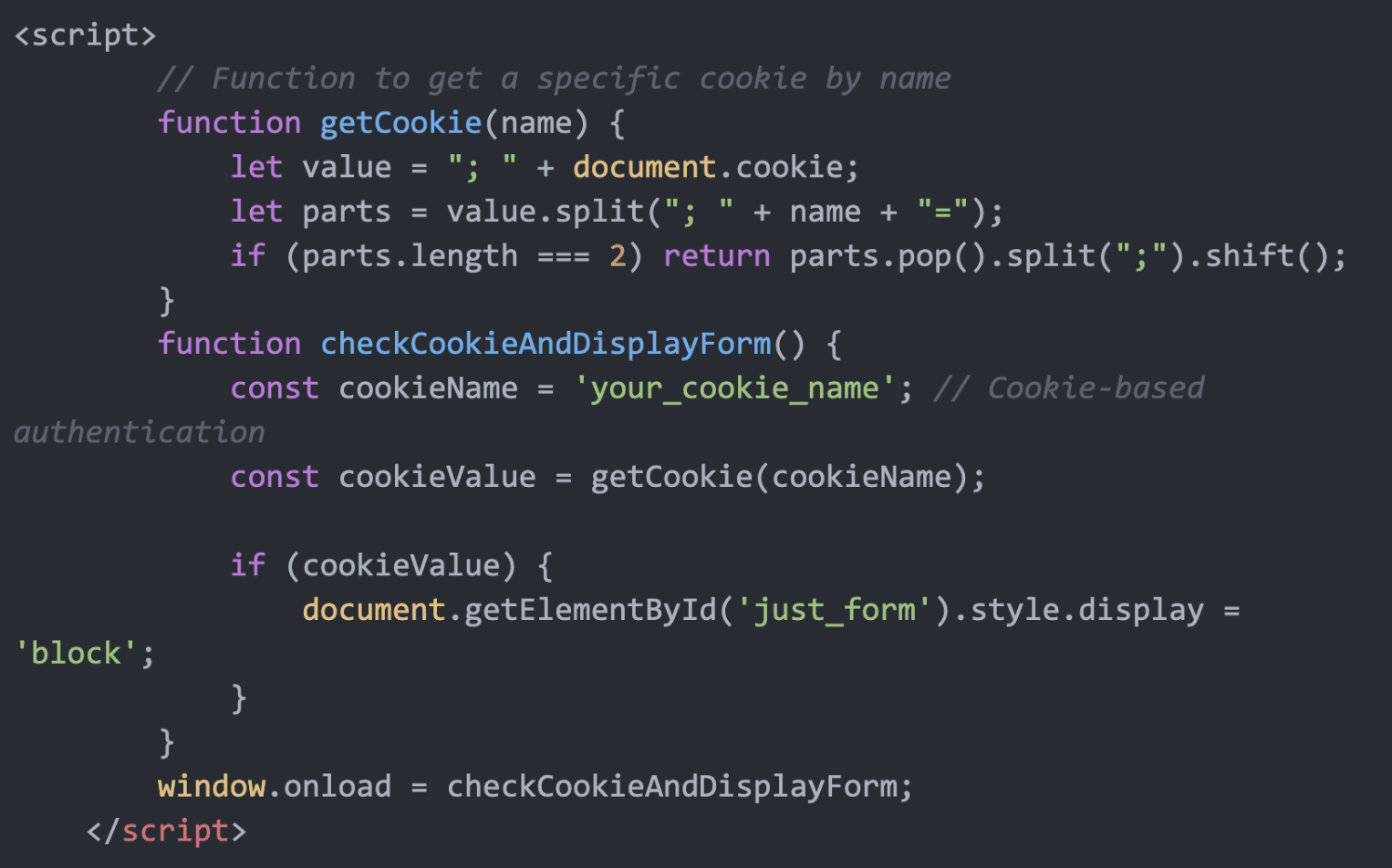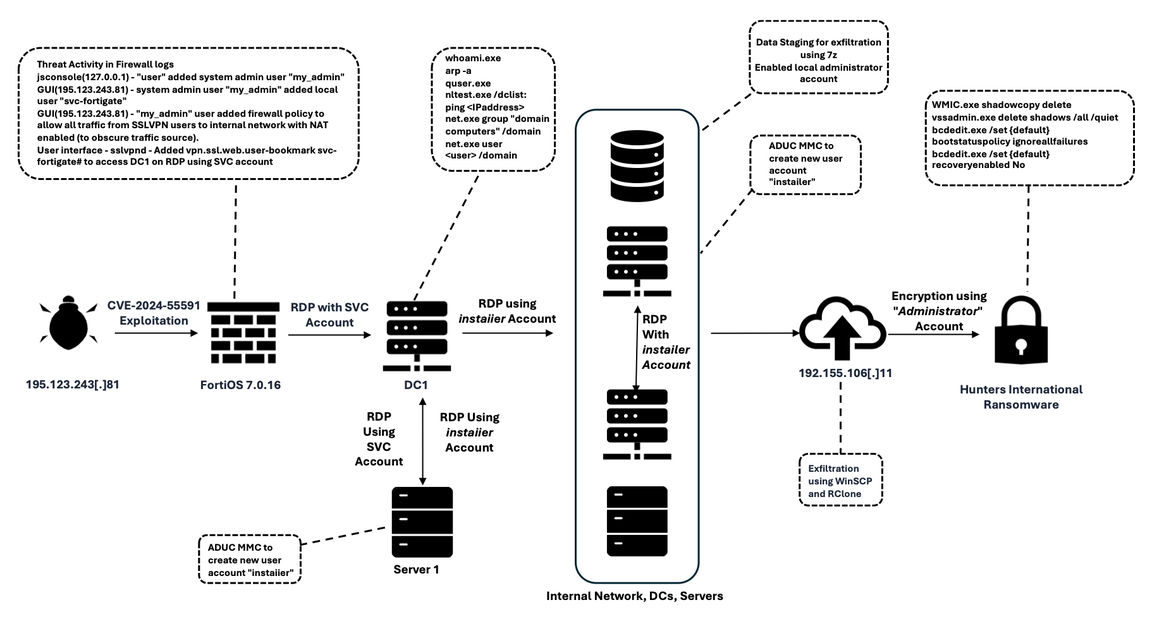
Summary: In February 2025, the eSentire Threat Response Unit (TRU) uncovered a sophisticated ransomware campaign by the Hunters International group against a retail organization, utilizing vulnerabilities in FortiOS for initial access. The attack involved the creation of a super admin account, lateral movement within the network, and the deployment of a new variant of ransomware designed to evade detection and prevent data recovery.…
Read More