This advisory addresses the significant threat posed by the “fast flux” technique, used by malicious cyber actors to evade detection and maintain command and control infrastructure. Fast flux enables the rapid alteration of DNS records, complicating tracking and blocking actions. The advisory calls for collaborative efforts from government entities and service providers to enhance detection and mitigation capabilities against fast flux activities.…
Read More Tag: EXPLOIT

Summary: North Korean threat actors, notably the Lazarus Group, have employed a new social engineering tactic called ClickFix to lure job seekers within the cryptocurrency sector, delivering a Go-based backdoor named GolangGhost on Windows and macOS. In parallel, a surge in fraudulent IT worker schemes has been detected in Europe, with North Korean nationals posing as legitimate remote workers to generate illicit revenue while circumventing international sanctions.…
Read More 
Summary: Counterfeit smartphones have been found preloaded with a modified version of the Triada Android malware, affecting over 2,600 users primarily in Russia. This malware can steal sensitive information, control devices remotely, and has been distributed through compromised production processes. The ongoing threat from Triada highlights vulnerabilities in the hardware supply chain and the potential financial gain for attackers.…
Read More 
Summary: A new vulnerability in Google’s Quick Share utility for Windows has been revealed, allowing potential denial-of-service (DoS) attacks and unauthorized file transfers. The flaw, tracked as CVE-2024-10668, is part of a broader set of vulnerabilities that could lead to arbitrary code execution if exploited. Although an initial fix was issued, follow-up analysis indicated that some problems were not adequately addressed, leaving users at risk.…
Read More 
Summary: The CVE controversy surrounding a CrushFTP vulnerability highlights the tensions between the vulnerability intelligence firm VulnCheck and CrushFTP regarding the assignment of CVEs. Following a critical vulnerability disclosure, two separate CVEs were assigned by different organizations, leading to confusion and exploitation attempts shortly after the flaw was publicized.…
Read More 
RapperBot is a malware family targeting IoT devices, first observed in June 2022. A recent variant launched a significant DoS attack on the AI startup DeepSeek. The malware, designed for ARM architecture, employs various techniques for obfuscation and managing socket connections. Affected: IoT devices, AI firms
Read More Keypoints :
RapperBot is a malware family specifically targeting Internet of Things (IoT) devices.…
This content explores the significance of Cyber Threat Intelligence (CTI) in improving organizational security and understanding the threat landscape. It delves into the motivations of various types of threat actors, their tactics, and how to effectively mitigate risks. The goal is to provide a comprehensive guide that enhances awareness and proactive measures against cyber threats.…
Read More 
This article explores Russia’s cognitive warfare tactics, rooted in Soviet KGB doctrines, and their modern adaptations involving disinformation and cyber operations. It presents strategies to counter these tactics, including targeted cyber retaliation and strategic communication, utilizing frameworks such as SWOT and DIMEFIL. A comprehensive analysis is provided on the strategic environment and implications of Russian hacktivist groups, along with methods for dismantling them from within.…
Read More 
Summary: Security researcher Dylan has revealed eight critical zero-day vulnerabilities in the Netgear WNR854T router, which has been unsupported since its release in 2017. These vulnerabilities range from buffer overflows to command injection flaws, posing severe risks of remote code execution and unauthorized access. The vendor has declined to address the issues due to the device being classified as end-of-life (EOL).…
Read More Victim: Polizia italia mail access
Country : IT
Actor: babuk2
Source: http:/bxwu33iefqfc3rxigynn3ghvq4gdw3gxgxna5m4aa3o4vscdeeqhiqad.onion/blog/62fb4410d877de37af265a67e06d9aede52773ae9e949b381f0e89b4a4f337ec/
Discovered: 2025-04-03 03:20:43.528510
Published: 2025-04-03 03:19:37.234277
Description :
In a significant cybersecurity incident, the Babuk2 ransomware group has targeted the Polizia Italia, gaining unauthorized access to their email systems. This breach, which took place in Italy, poses serious implications for the country’s law enforcement integrity and data security, as sensitive information may have been compromised.…
Read More 
This article discusses strategies to counter China’s use of state-sponsored proxies in hybrid warfare. It analyzes the threats posed by these proxies, such as cyber groups and political influence networks, and outlines a comprehensive approach utilizing frameworks like DIMEFIL and SWOT. A coordinated response involving diplomatic, military, economic, and cyber measures is emphasized to effectively deter and disrupt China’s hybrid tactics.…
Read More 
The article discusses a sophisticated ransomware attack involving Qilin ransomware, which utilizes the technique of bring-your-own-vulnerable-driver (BYOVD) to bypass traditional Endpoint Detection and Response (EDR) measures. The analysis uncovers the exploitation of a lesser-known driver, TPwSav.sys, in the context of a ransomware-as-a-service model. It emphasizes the vulnerabilities exploited, the attack chain, and the retaliation measures taken by Blackpoint’s Security Operations Center (SOC).…
Read More
John the Ripper is a powerful hash-cracking tool that efficiently cracks various hash types such as Windows authentication hashes, /etc/shadow hashes, and password-protected files. Through practical tasks, users learn the syntax, features, and methods to conduct dictionary attacks and utilize custom rules. Affected: Windows systems, Linux systems, password-protected ZIP and RAR files
Read More Keypoints :
John the Ripper is a versatile tool for hash cracking.…
The “RolandSkimmer” campaign utilizes malicious browser extensions and LNK files to execute persistent credit card skimming attacks, primarily targeting users in Bulgaria. The malware collects sensitive data through deceptive mechanisms while maintaining stealth and adaptation to its victims’ environments. Affected: Microsoft Windows, Chrome, Edge, Firefox
Read More Keypoints :
The “RolandSkimmer” campaign targets Microsoft Windows users through malicious LNK files and browser extensions.…
Summary: A new wave of phishing attacks, termed “quishing,” uses QR codes to deceive victims into revealing their credentials. Researchers from Unit 42 have identified evolving strategies among attackers, employing QR codes to mask malicious URLs and making it difficult for traditional security measures to detect threats.…
Read More 
The Socket research team uncovered a malicious Python package named disgrasya on PyPI, designed to automate carding attacks against WooCommerce stores using CyberSource as a payment gateway. This openly malicious tool facilitates the testing of stolen credit card numbers, allowing low-skilled fraudsters to simulate transactions without raising fraud detection alarms.…
Read More 
Summary: Multiple vulnerabilities have been discovered in Jan AI, an open-source alternative to ChatGPT, which could allow remote attackers to exploit the system without authentication, according to security platform Snyk. The issues include arbitrary file write capabilities and remote code execution risks due to insufficient protections.…
Read More 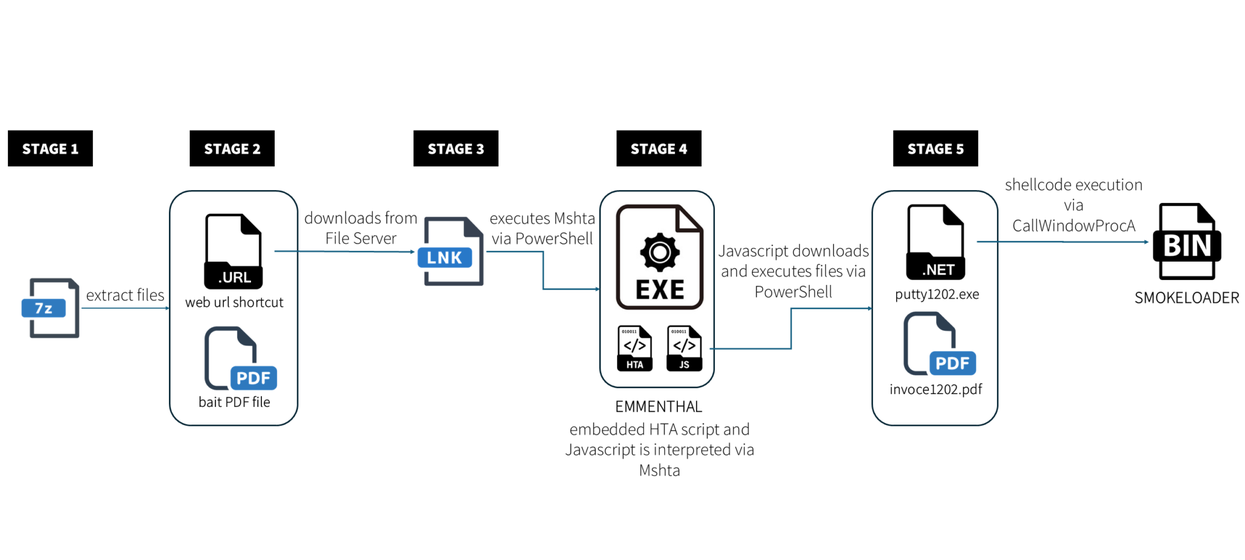
Summary: G DATA security researchers have uncovered a sophisticated malware infection chain targeting First Ukrainian International Bank, centering on the enhanced SmokeLoader and its intermediary, Emmenhtal Loader. The attack utilizes social engineering, living off the land binaries, and advanced evasion techniques to deploy multiple malware stages stealthily without detection.…
Read More Summary: The video discusses the recent bankruptcy filing of 23andMe, a popular genetic testing service, and the implications for its customers’ DNA data. It also covers allegations of a data breach involving Oracle Cloud, highlighting an attack that reportedly succeeded despite Oracle’s denial. Additionally, the video delves into newly released vulnerabilities discovered by Whiz in the EngineX ingress controllers that can lead to remote code execution.…
Read More 
RapperBot is a malware family targeting IoT devices, noted for conducting a large-scale attack against Chinese AI startup DeepSeek. Observed since June 2022, RapperBot has evolved through improved capabilities and malicious strategies, including SSH brute force attacks. The malware is designed to expand its attack surface by leveraging specific vulnerabilities.…
Read More