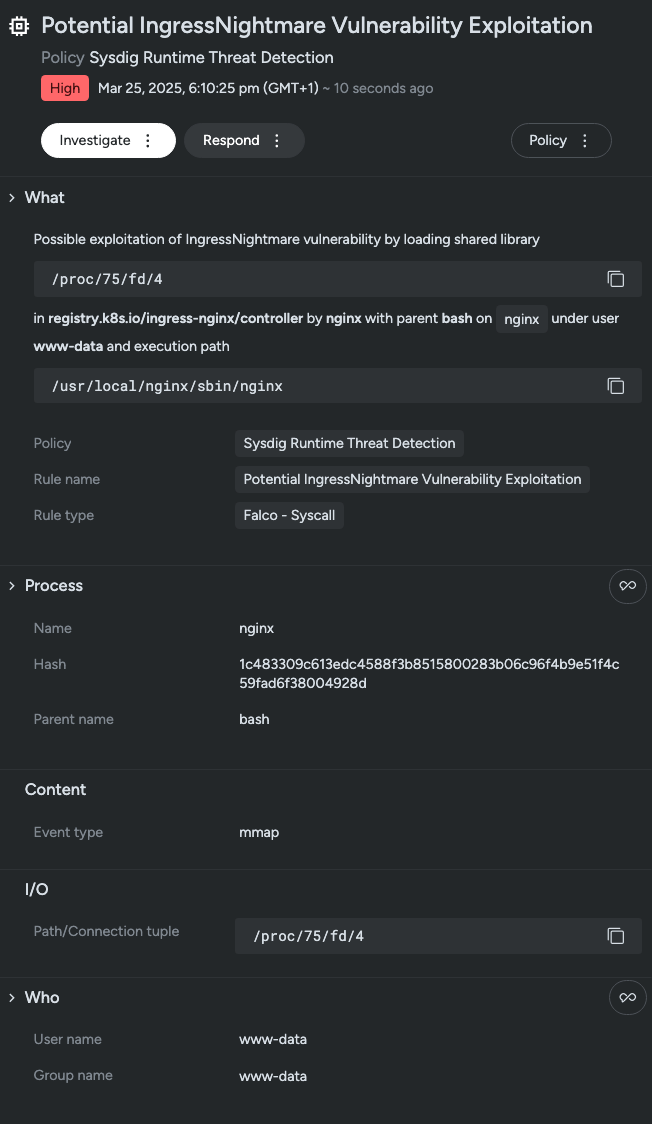
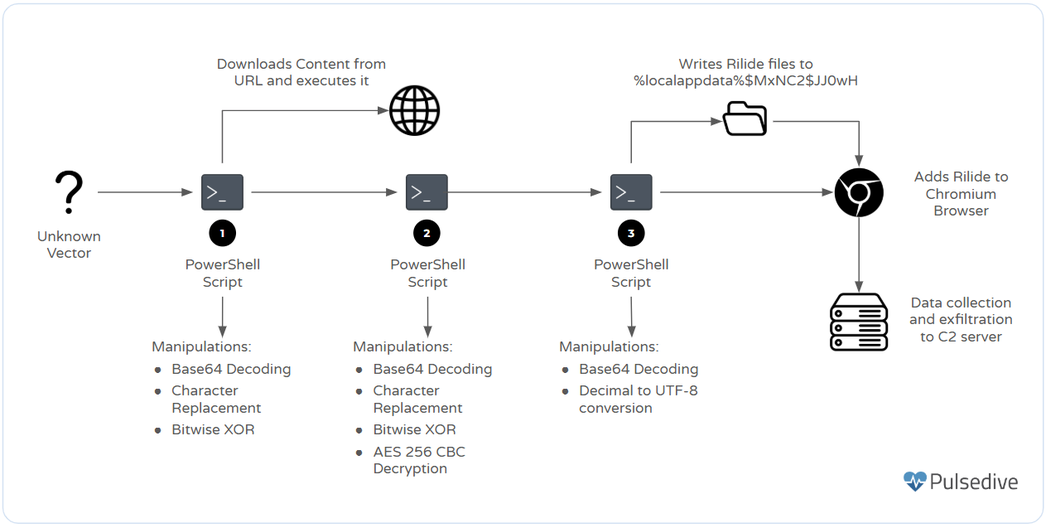
Keypoints :
ClickFix-style social engineering techniques are becoming more prevalent among threat groups.…
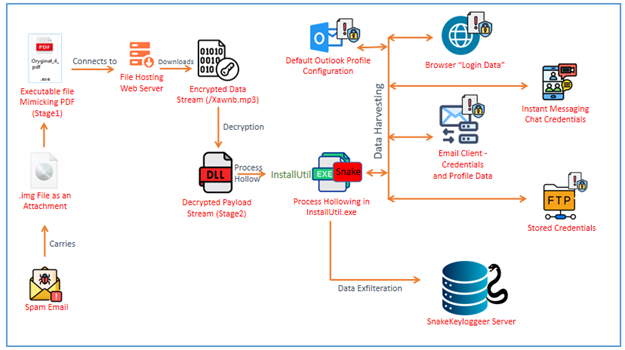
Recent social engineering tactics have evolved to include a variant of the SectopRAT malware, which is disguised as a Cloudflare verification challenge. This Remote Access Trojan employs extensive techniques for data exfiltration and uses various evasion methods to avoid detection. Affected: Users, Browsers, Cryptocurrency Holders
Read More