The Lotus Blossom, also known as Lotus Panda, is a sophisticated Chinese APT group involved in cyber espionage for over a decade. They have recently enhanced their tactics by deploying new Sagerunex backdoor variants that utilize third-party cloud services and social media for command-and-control activities. This article examines their tactics, techniques, and procedures, detailing their operational framework along with the challenges we face against such persistent threats.…
Read More Tag: EXFILTRATION
Trend Research reveals the exploits of Water Gamayun, a suspected Russian threat actor leveraging a zero-day vulnerability (CVE-2025-26633) in Microsoft Management Console to deploy malware. Their methods include custom payloads, data exfiltration techniques, and the use of backdoor malware. This campaign poses severe risks to organizations, including data theft and operational disruption.…
Read More 
The TsarBot Android Banking Trojan targets over 750 applications, employing phishing sites and overlay attacks to steal sensitive information. It can manipulate the device’s screen, perform fraudulent transactions, and capture user credentials via a fake lock screen. This threat emphasizes the persistent dangers posed by banking malware.…
Read More 
This article discusses the risks associated with misconfigured Jenkins instances in CI/CD pipelines, highlighting a specific case where an exposed Jenkins service led to unauthorized access and severe security vulnerabilities. The findings from CloudSEK’s BeVigil underscore the potential consequences of such misconfigurations, including remote code execution, credential theft, and regulatory risks.…
Read More 
Summary: A new campaign utilizing the PJobRAT Android malware has been detected, targeting users in Taiwan under the guise of chat applications. This malware, previously aimed at Indian military personnel, has evolved to harvest sensitive information while masquerading as messaging apps. Security researchers indicate its operation spanned nearly two years before pausing in October 2024.…
Read More 
Recent social engineering tactics have evolved to include a variant of the SectopRAT malware, which is disguised as a Cloudflare verification challenge. This Remote Access Trojan employs extensive techniques for data exfiltration and uses various evasion methods to avoid detection. Affected: Users, Browsers, Cryptocurrency Holders
Read More Keypoints :
ClickFix-style social engineering techniques are becoming more prevalent among threat groups.…
Summary: RedCurl, a Russian-speaking threat actor, has shifted tactics by deploying a new ransomware called QWCrypt, primarily targeting virtual machines. This marks a notable change from its previous focus on corporate espionage since 2018. The group uses phishing methods for initial access while maintaining a low profile and avoiding public ransom demands.…
Read More 
This article highlights the cybersecurity vulnerabilities that arise when financial institutions rely on third-party vendors. It details how CloudSEK’s SVigil platform discovered exposed credentials of a key communication service provider, which led to a significant data breach affecting a major banking entity. The timely detection helped prevent potential misuse of sensitive data and loss of customer trust.…
Read More 
INDOHAXSEC, a recent Indonesian hacktivist group, has conducted various cyberattacks including DDoS and ransomware targeting government entities and companies, motivated primarily by political agendas related to pro-Palestinian sentiments. They use a combination of custom and off-the-shelf tools, and maintain a notable presence on platforms like GitHub and Telegram.…
Read More 
Summary: The UAE government successfully thwarted a major cyberattack aimed at 634 government and private entities, attributed to a hacker known as “rose87168.” The breach, potentially exposing around six million customer records, raises significant concerns about ongoing cyber threats to the UAE, highlighting the necessity for robust cybersecurity measures.…
Read More 
A major telecommunication company in Asia has been targeted by a persistent threat actor identified as Weaver Ant, linked to China. The group has used stealthy techniques like web shells to maintain access and facilitate cyber espionage. This highlights the need for organizations to develop robust defense strategies against state-sponsored threats.…
Read More 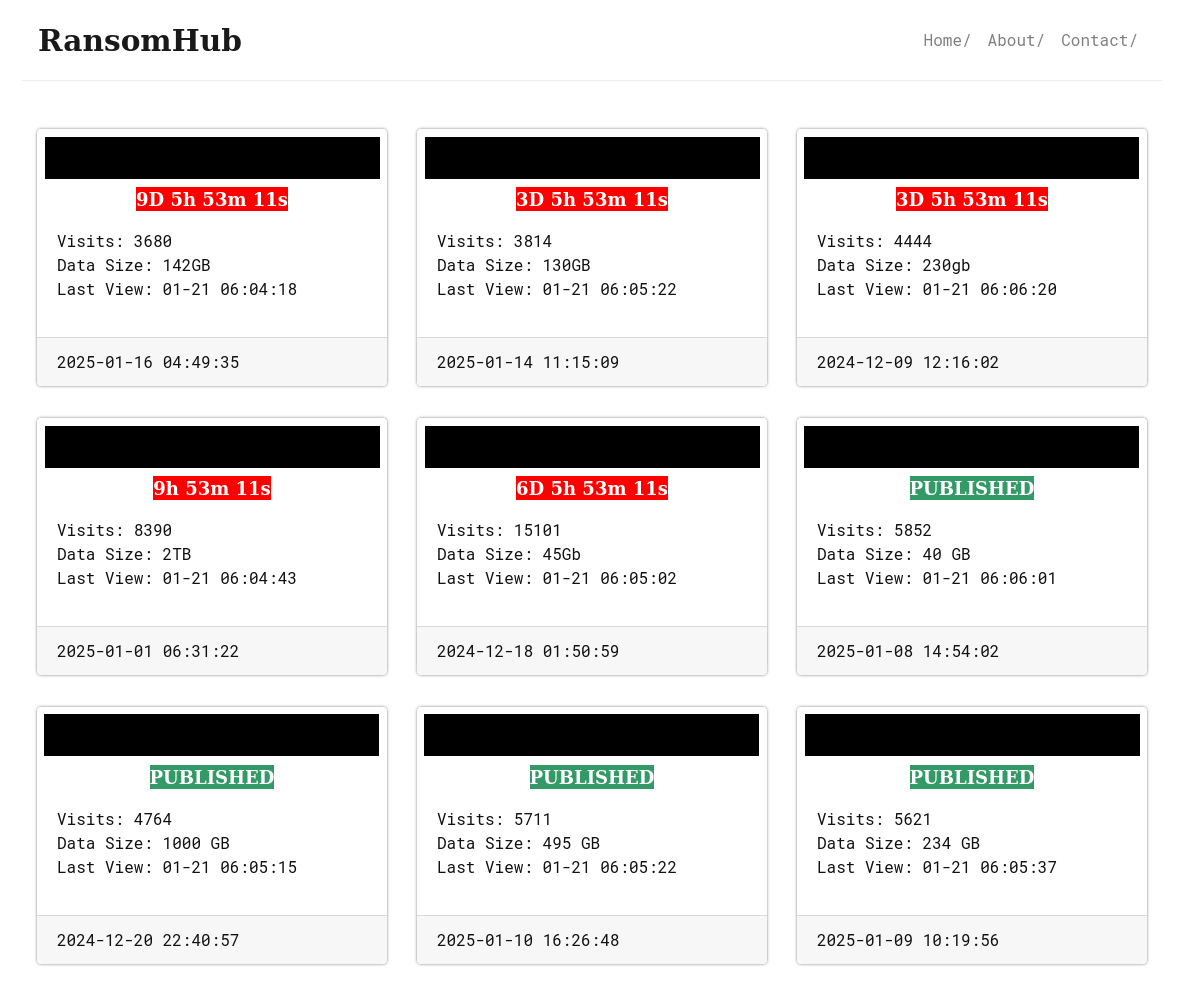
ESET researchers examine the ransomware landscape in 2024, highlighting the emergence of RansomHub, a prominent ransomware-as-a-service (RaaS) group linked to established gangs like Play, Medusa, and BianLian. The article discusses the rise of EDR killers, particularly EDRKillShifter, developed by RansomHub, and reflects on the shifting dynamics of ransomware payments and victim statistics.…
Read More 
Summary: MORSE Corp, a defense contractor based in Cambridge, Massachusetts, has settled with the U.S. government for .6 million due to violations of federal cybersecurity requirements. The settlement stems from allegations that the company misrepresented its cybersecurity posture and failed to comply with standards set by the National Institute of Standards and Technology.…
Read More 
The article discusses the ongoing smishing campaigns targeting the Italian public, particularly focusing on scams related to the INPS (National Social Security Institute). The scams involve the theft of identity documents, mostly selfies where the document is displayed next to the victim’s face. Despite continuous monitoring and takedown efforts by CERT-AGID, these fraudulent activities continue to proliferate, leading to an increase in victims and the illegal sale of personal documents on the dark web.…
Read More 
Summary: The threat actor group RedCurl has evolved from corporate espionage to deploying a ransomware encryptor, QWCrypt, targeting Hyper-V virtual machines. Their tactics now include sophisticated phishing schemes and stealthy methods for lateral movement within networks. This strategic shift raises questions about their motives and operational goals, as they blend espionage with ransomware attacks.…
Read More 
Summary: The integration of Generative AI (GenAI) in enterprise environments has surged, paving the way for significant security worries, particularly concerning the sharing of sensitive data. A recent report emphasizes the implications of “shadow AI,” where employees utilize personal accounts for GenAI applications, heightening the risk of data exfiltration.…
Read More 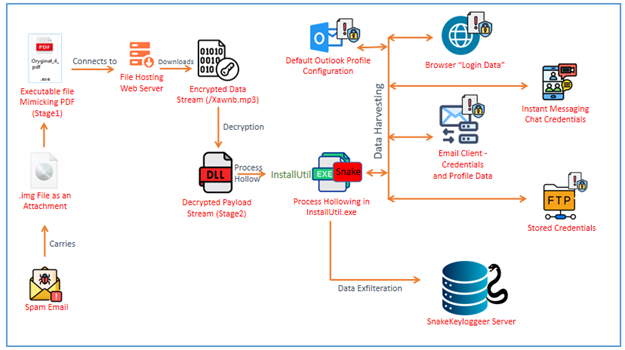
The SnakeKeylogger campaign illustrates a sophisticated credential-stealing threat targeting both individuals and businesses. Utilizing multi-stage infection techniques, it cleverly evades detection while harvesting sensitive data from various platforms. Attackers employ malicious spam emails containing disguised executable files to initiate the infection. Affected: Individuals, Businesses, Email Clients, Web Browsers, FTP Clients.…
Read More 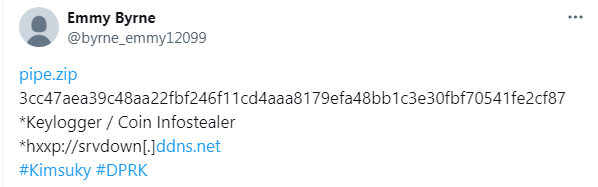
Kimsuky, a North Korean APT group, has been identified as engaging in sophisticated cyber espionage techniques targeting various nations, including South Korea, Japan, and the U.S. Their attack methods involve a series of malware payloads delivered via a ZIP file, leading to data exfiltration and sensitive information theft.…
Read More 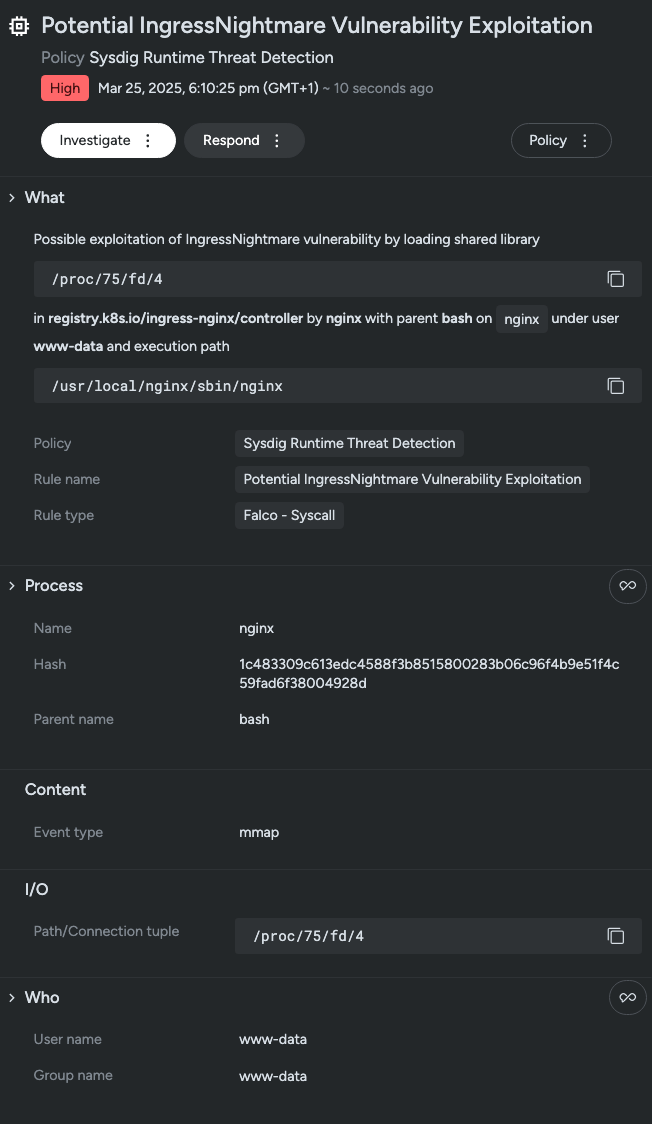
A set of critical vulnerabilities, including CVE-2025-1974, affecting the Ingress NGINX Controller in Kubernetes was disclosed, posing severe threats such as remote code execution. Organizations are encouraged to mitigate these risks by promptly upgrading to the latest versions of the NGINX Controller and securing admission webhook endpoints.…
Read More 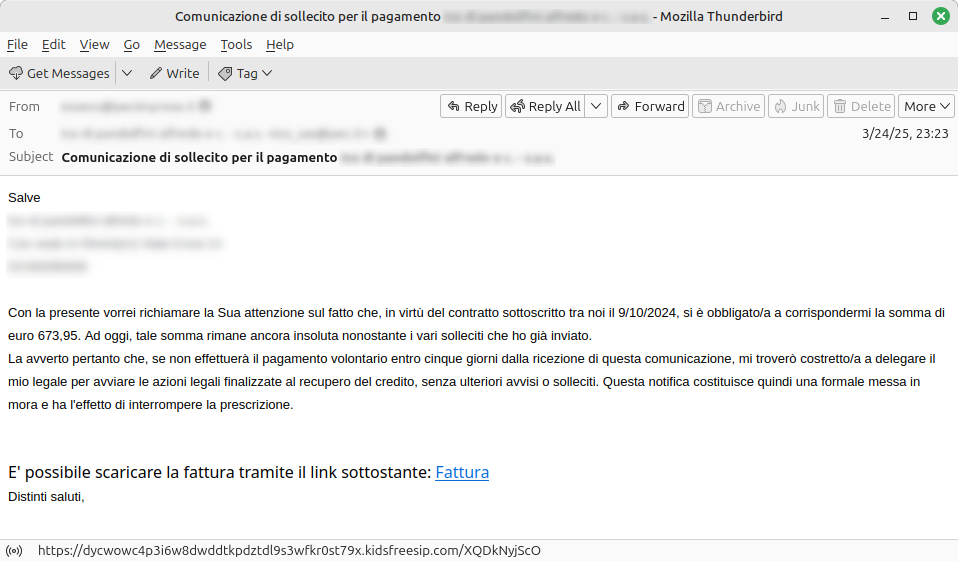
A new malicious campaign has been detected, targeting users of certified email (PEC) accounts. The attackers exploit the perceived reliability of these communications to enhance their success rate. The malware used has shifted from Vidar to AsyncRat, a remote access trojan (RAT), indicating a potential escalation in the attack’s objectives.…
Read More