Keypoints :
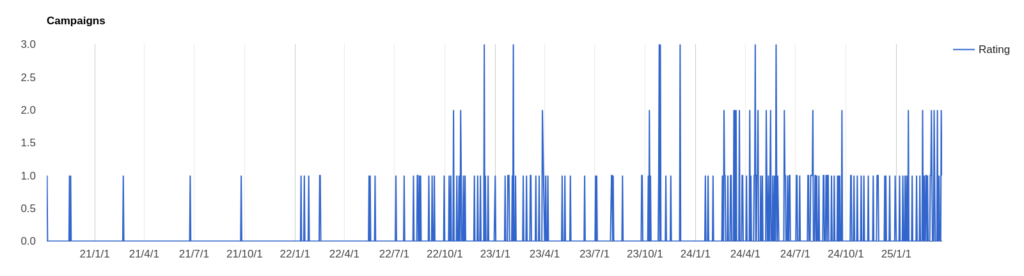
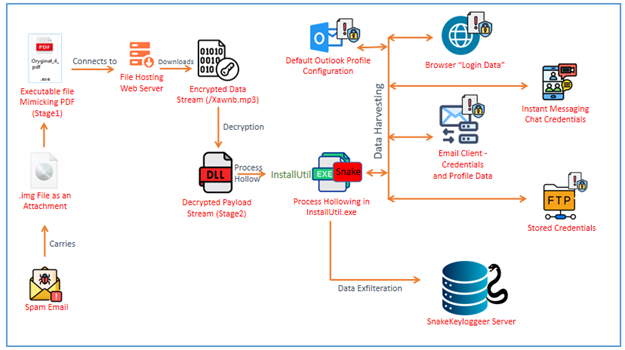
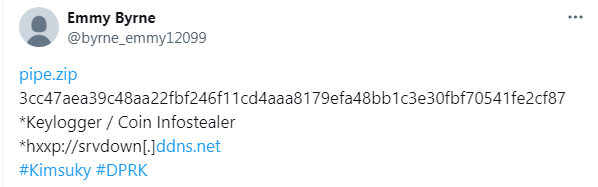
Transportation and logistics sector is a major target for cybercriminals due to valuable data.…
The transportation and logistics industry is increasingly targeted by cybercriminals as they exploit vulnerabilities to disrupt operations and steal sensitive data. Major incidents include ransomware attacks affecting ports and airports, along with data breaches that raise severe concerns about data security within the sector. Affected: transportation and logistics industry, public infrastructure, cybersecurity sector
Read More